- Jamf Nation Community
- Products
- Jamf Pro
- Re: macOS Catalina and 'Activation Lock'
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
macOS Catalina and 'Activation Lock'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
06-04-2019
03:31 AM
- last edited on
03-04-2025
07:29 AM
by
![]() kh-richa_mig
kh-richa_mig
I have not yet seen full details of this new feature but the summary indicates it is like the activation lock on iPhones.
You enter your Apple ID and turn on the feature and after that no-one can erase the laptop unless they unlock it with the same Apple ID. The idea being that like iOS since it cannot be erased it can continue to report its location to 'Find my Mac' and that if you presumably also have FileVault enabled thieves cannot login. With the overall goal to make it less attractive to steal such protected Macs.
It is indicated that this will only be possible on a T2 equipped Mac.
Presumably it also utilises secure boot.
Now this all sounds great especially for home users. It however also sounds like a potential minefield for enterprises. (That is all us here.)
As battle worn Mac admins will know Apple IDs are not enterprise friendly. They cannot cope with more than a handful of devices. So how are enterprises supposed to enable this feature for thousands, or hundreds or even just a hundred Macs? Secondly what happens if you don't centrally enable this but when you issue a laptop a user themselves enables this? If they leave and hardback the laptop you likely will not be able to unlock it as you will not have their personal Apple ID credentials.
For iOS you can use Apple Configurator to 'supervise' a device to provide a backdoor but what about Macs?
Since this system may well involve using JAMF to help manage it maybe JAMF are able to comment. Otherwise the audience here is certainly going to want to use this or prevent this.
- Labels:
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-04-2019 05:32 AM
I would assume like currently DEP enabled iOS devices in Jamf, if the Mac is DEP enabled (I.e under supervision) and enrolled into a MDM it will allow admins to override the lock.
Like most of the changes we saw in Mojave, unless your using a modern MDM and using Apple Business/Schools Manager life is going to be made very difficult managing Catalina mac's in the enterprise
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-04-2019 04:46 PM
I have not read up on the Catalina OS yet, we are still trying to iron out some incompatible SW for Mojave and the need for KEXTS... which BTW sticks for MDM management. Are you listening Apple?
But if what you are saying is a new feature I can see loads of issues with difficulties in management abilities. I do, however, think it is too soon to make any guesses on the final projects outcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-04-2019 05:04 PM
If you are concerned about this, contact your Apple SE now. They can convey customer impact to the engineers.
A DEP-enrolled Mac should behave like a company device, where Activation Lock can be overridden by the DEP administrator. The customer can request an Activation Unlock. Since this is a Mac, they will need to streamline this request as the process currently takes a few days for iOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-04-2019 06:34 PM
At a guess, this would be more reason to make sure the devices are DEP setup. Because I'm guessing Jamf will update to have a release activation lock like they do for iphones. Pain for any that aren't in DEP though, especially in places where DEP is still not available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-06-2019 04:15 AM
Yes I have since seen a further article post WWDC and DEP would give you the equivalent of supervised mode and like iOS a means of unlocking devices.
Currently the powers that be in our company have denied me the ability to use DEP as it requires exposing our system to the Internet. There was a vulnerability in DEP discovered - since fixed. See - https://appleinsider.com/articles/18/09/27/apples-device-enrollment-program-vulnerable-to-attack-over-device-serial-authentication
I have raised this activation lock feature as a need to review this decision.
Related to this possibly is that Apple are introducing 'Managed' AppleIDs for enterprise use and this is in the limited info so far tied to a Microsoft Azure Active Directory backend. Our company however is very much opposed to using AD especially a cloud AD so this also may become a problem.
I am hoping this feature will not be limited to Azure AD and that 'Managed' AppleIDs will be possible with other directory server systems i.e. ones own internal system. (Even OpenDirectory has not yet been mentioned for this.)
This is something JAMF and especially JAMF Connect needs to address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-17-2019 04:52 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2020 10:51 AM
Just wanted to share a quick update. According to our Jamf CSM:
"I have not yet seen a customer run into a Catalina machine that is managed by Jamf and Activation Locked. This is because Jamf Pro has never sent the "allow" command to eligible Catalina devices, even users who have Find My enabled are not Activation Locking their devices."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2020 03:56 PM
https://developer.apple.com/documentation/devicemanagement/get_the_bypass_code_for_activation_lock
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2020 08:29 AM
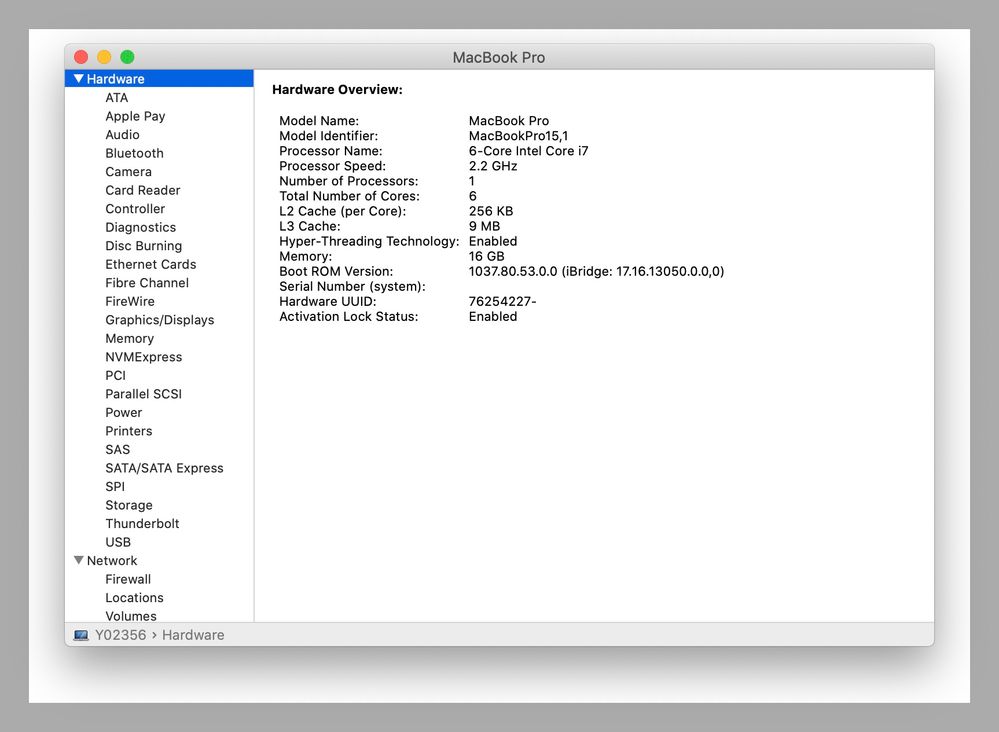
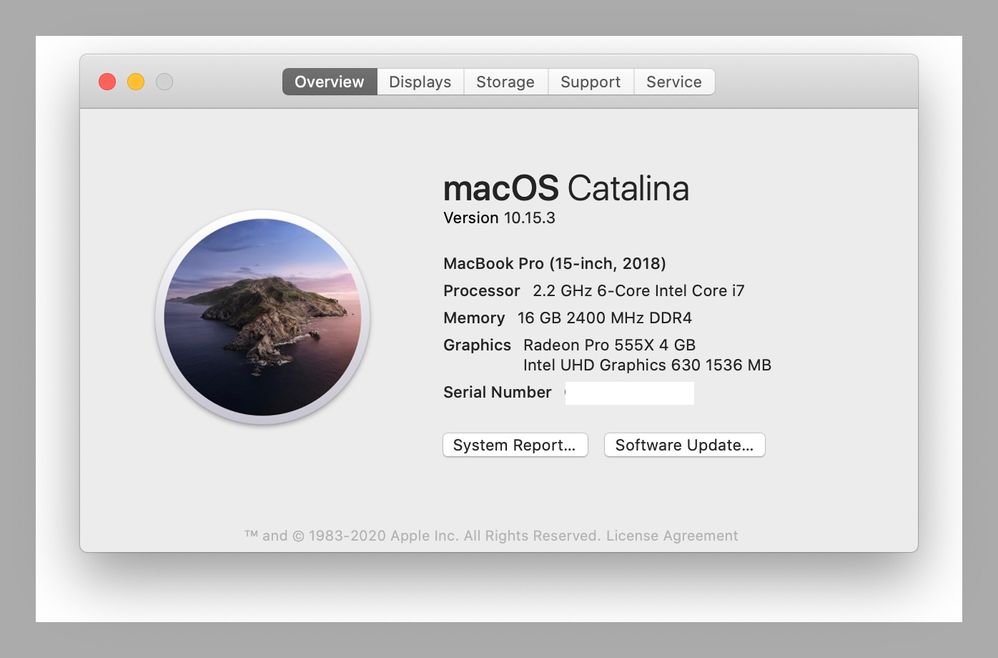
@jtrant Unless I am misinterpreting things your Jamf CSM is wrong. See the following screen captures. These are taken on a MacBook Pro 15-inch 2018 model which therefore has a T2 chip. As per the screen captures it is running Catalina 10.15.3 and is logged in to iCloud and is managed by Jamf. Again according to the screen captures it does have Activation Lock enabled.
Jamf binary information is -
% jamf -version
version=10.17.0-t1572881164
The following command also queries the status of Activation lock and returns it in Terminal.
% /usr/sbin/system_profiler SPHardwareDataType | awk '/Activation Lock Status/{print $NF}'
Enabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2020 08:50 AM
We solved this by removing local admin on the machines. If a user is not a local admin they cannot enable Activation Lock as it requires an admin Login and Password.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2020 08:54 AM
@lockwojo , I will point out that it does not appear that your Mac in the screenshots is supervised which may be what changes whether activation lock enables or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-06-2020 06:58 AM
@lockwojo What enrollment process did you use? Not DEP/automated enrollment, since not supervised in your screenshots.
Also : what is the order: first iCloud (and thus activation lock) , then enroll?
The Jamf person is correct IF YOU USE AUTOENROLL. if not, it depends on the order of things I guess. (not tested, DEP is default for our org)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2020 11:07 AM
the non Pro iMacs do not have T2 chips so they will not activation lock
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-13-2020 01:36 PM
Following up on this, it does appear that Activation Lock is enabled upon iCloud sign in, regardless of supervision status on T2 Macs. In my case, the System Report showed 'Disabled' but running the script above showed 'Enabled'. I booted the Mac to recovery mode and tried to wipe the drive and was then prompted for a password.
My initial response is to disable the setting using a plist file (com.apple.icloud.managed.plist) and setting "DisableFMMiCloudSetting" to "YES". This would only prevent clients from activating the feature and would not disable it on clients that have already done so.
I've followed up with my Jamf CSM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2020 12:58 AM
@jtran That is curious, I have so far used the System report status. Strange the script shows enabled.
The fact that you are asked to enter a password when booting to recovery is expected behaviour, because there is a configured local user.
Activation lock (if active) will show at a later step . I expect this behaviour when you try to re-install a activation locked T2 mac:
- erase the mac (I expect that work after 'forgot all passwords')
- re-install (should that work?, I am not sure)
- run setup assistant (should defenitively meet activation lock after connecting to wifi)
Share your finding with us. I am interested
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2020 04:45 AM
I have run into the issue of having a Mac returned to us which was Activation Locked, and being unable to manually wipe it using Internet Recovery.
Wiping the machine by connecting it to an ethernet cable, booting normally, and sending the remote wipe command from the JSS worked perfectly. Returning to Internet Recovery, the Mac then proceeded through the 'activation' process before allowing me to reinstall macOS as normal. If your Mac is able to gain WiFi access at the FileVault login screen, then you may not even need to use the ethernet cable.
Our Macs are enrolled with DEP, so I cannot confirm the behaviour of a manually enrolled Mac. It seems, however, that an MDM wipe removes the Activation Lock.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2020 12:05 PM
@maurits , confirming that the password I was asked for was an Apple ID - not a local account password.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-17-2020 11:47 AM
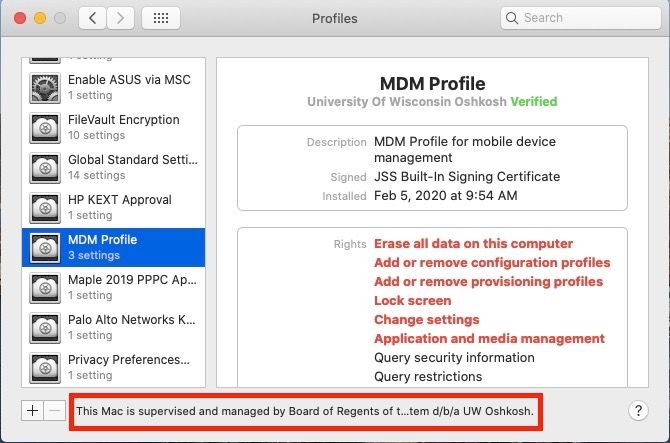
@nelsoni I see above you have highlighted a piece of the MDM profile showing the profile is being managed, next to +/- buttons. Is there some special way you are making this appear? I don't see it myself in my MDM profile but would prefer to have that language appear to inform users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-17-2020 12:24 PM
mconners, This text appears when the device is DEP enrolled and supervised by Jamf.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-17-2020 01:46 PM
That's interesting @nelsoni as we do both, supervised by Jamf and DEP enrolled, for a few years actually. I wonder how we can get that to display? I will reach out to Jamf support, I bet it is a simple checkbox that I am missing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-17-2020 08:29 PM
I should clarify that it only shows up on Catalina machines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-18-2020 11:00 AM
Looks like this feature is coming in Jamf Pro 10.20.0, according to the release notes for Beta 1.
In the meantime, I've restricted Find My Mac for all clients using a configuration profile, with the exception of those with it enabled. Once they disable, they fall into scope for the restriction and are then made eligible for Catalina.
I'd be interested to hear how others are working around this issue.