This pop-up started 02/06/23 and has been hit or miss with different users reporting it goes away and some stating it shows up every 30mins. What has changed for this to take place?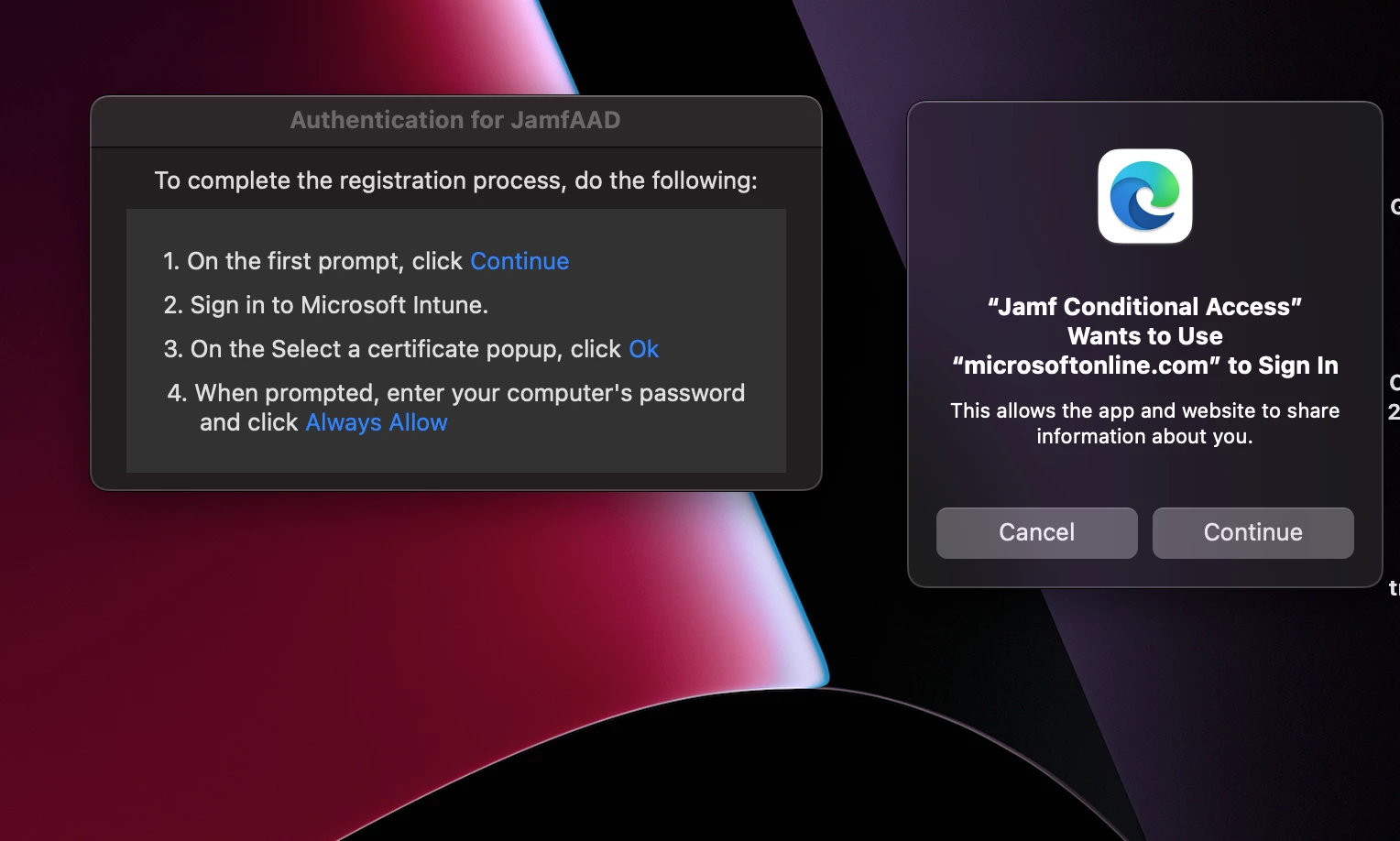
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.