- Jamf Nation Community
- Products
- Jamf Pro
- Re: Okta SSO Login failure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-27-2024 09:25 AM
Greetings all,
We are in the very earliest stages of setting up Okta. I'm currently working on configuring our JSS Dev environment to use Okta for SSO.
I'm working directly with our internal Identity Management team who manages our Okta instance. They setup the integration on the Okta side, but I have no idea how they went about it.
In the JSS dev, I've enabled SSO using Okta, added the necessary metadata URL provided by the IAM team, etc.
When attempting a login, I am presented with the expected Okta user name screen, followed by the password screen, suggesting that the login process is working (and I've received notifications of a successful login), but then directed to an error message:
Safari can't find the server.
Safari can't open the page "https://https//<mysandbox>.jamfcloud.com/saml/SSO" because the Safari can't find the server "https".
Note the extra "https// in the Url.
The Okta team says everything is OK on their end, and I've reviewed the JSS SSO settings with them, and they see no issues on the JSS side.
A similar, but not identical, error message appears in Chrome.
Has anyone seen this before? Any thoughts?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2024 10:00 AM
Problem solved. Turns out the Okta team misread or mistyped the URL. They fixed that and now SSO sign in is working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-27-2024 11:08 PM
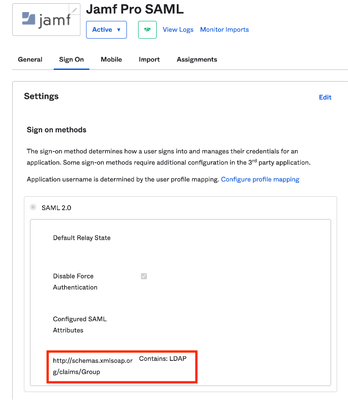
Maybe try a SAML tracer like "rcFederation Tracer" to validate what is happening. I had issues too which turned out to be that the response was trying to send all the group memberships but there was a max number. For me I had to get my Identity team to specify what groups to look for.
In this test example they added the group called LDAP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-28-2024 07:13 AM
@wsmits Thank for the suggestion. I ran rcFederationtracer and found 2 resulting outputs.
I know nothing of how federation is supposed to work, so I'm making assumptions here based on the resulting files;
It appears the first output is the request from my JSS sandbox to the Okta instance.
the second file appears to be the response from Okta, after a successful authentication, telling the browser where it should redirect to, and I'm seeing the bad URL there.
Given my lack of knowledge here, I'm going to open a ticket with Jamf support as well, but I think this gives me some additional info that I can provide to our Okta team as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2024 06:52 AM
Assuming this is the MenuBar App. It sounds like you may not have the OktaAuthServer key set correctly.
- Can you share your sanitized Configuration Profile?
- Are your Okta admins seeing the authenticate attempt for your tests?
- OktaAuthServer should be your Okta auth server, and you dont want to add https:\\ in the URL as that is added automatically.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2024 09:59 AM
@AJPinto Are you referring to Jamf Connect? That's the next step for us. Currently working on using Okta for SSO, which is now working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2024 05:19 AM
Crap, yes. I was on the Connect wagon.
So long as the Entity ID, and Identity Provider Metadata Source are correct in your Jamf Console, the issue is going to be within Okta. My guess is they setup the Single sign on URL incorrectly in the General SAML Settings for the Jamf Pro app integration. Basically, you are getting to your Okta auth realm because Jamf Pro is setup correctly, but when Okta is redirecting you back to Jamf, it's sending you to the wrong URL.
Have them check the Single sign on URL, and make sure it is just instancename.jamfcloud.com/saml/SSO without https://.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-01-2024 10:00 AM
Problem solved. Turns out the Okta team misread or mistyped the URL. They fixed that and now SSO sign in is working.