Hi all
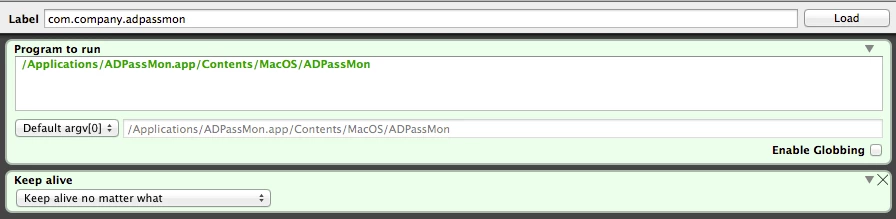
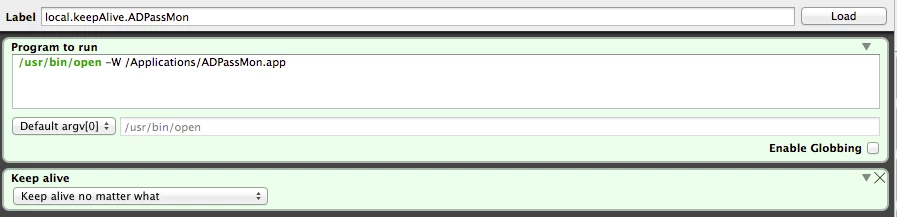
I'm trying to create an Extension Attribute to report back the status of a Global LaunchAgent which is in /Library/LaunchAgents
When run from the user context it reports back correctly but when run as root it does not, i've gone through most of the dicussions and tried adding in ls -l /dev/console | cut -d " " -f4 then sudo -u to the logged in user but my script fu is weak.
Can any one advise how to make the script below run the launchctl list command as the logged in user as an extension attribute ?
Cheers,
Andy
#!/bin/sh
agentloaded=`launchctl list | grep local.keepAlive.ADPassMon | awk '{print $NF}'`
if [ "${agentloaded}" == "local.keepAlive.ADPassMon" ]; then
echo "<result>Loaded</result>"
else
echo "<result>not loaded or installed</result>"
fi