- Jamf Nation Community
- Products
- Jamf Pro
- Re: Silver Sparrow Malware
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Silver Sparrow Malware
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 05:38 AM
I just read about this new malware found to have infected 30,000 macs. Here's the link to information: https://redcanary.com/blog/clipping-silver-sparrows-wings/
Has anyone come up with some strategies to find and remove this from macs in their environment?
Thanks for sharing.
- Labels:
-
Jamf Admin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-25-2021 08:02 AM
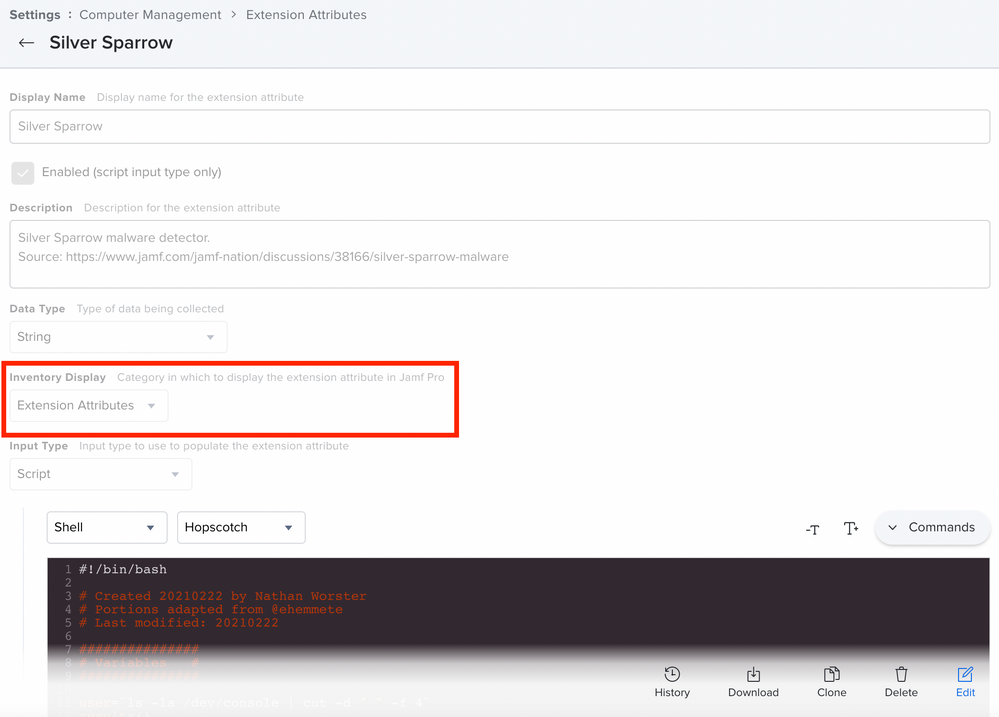
Hey @jonathan.rudge The setting under Inventory Display allows you to set where on a computer's inventory display the results of an EA should appear.
For the sake of completeness: The dropdown menus at Default Mode and Default Theme are only there to customize the syntax highlighting and the appearance of scripts within the Jamf Pro interface. These settings have no effect on the functionality of a script ;-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-25-2021 09:31 AM
@abuehler thanks, all sorted now. Did a test on my own MacBook and it reported back and the smart group alerted! Great script thanks everyone
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-25-2021 10:05 AM
I'm interested in the real world infection totals. Assuming most here are running at least some sort of Anti Virus and Malware solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-26-2021 05:03 AM
Yesterday, I used the touch command to create one of the suspect files. The EA and Smart group reported it. Today that file is gone. Could it be the result of the releases of MRT 1.66 and XProtect 2129? I haven't check the logging from our security agents to determine whom is responsible.
Has anyone else observed the files are being deleted?
EDITED - Ignore my statements above. I the test file is in place on my test device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-26-2021 06:28 AM
@jhalvorson Any chance your file that was deleted was in /tmp?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-26-2021 06:32 AM
@julhs the file I created was /Users/testusername/Library/Application Support/verx_updater
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-03-2021 09:04 PM
Hi All - Script work great for me. Can someone share steps how to delete those files through policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 12:18 AM
@agakhan_admin
I think, it could be a good way to write a script and delete the files with the rm - command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 01:28 AM
Will the script be like below?
!/bin/zsh
rm -R /Applications/tasker.app
rm -R/tmp/agent.sh
rm -R/tmp/version.json
and so on.....
"/tmp/version.plist"
"/tmp/agent"
"/tmp/verx"
"/Users/$user/Library/._insu"
"/Users/$user/Library/Application Support/agent_updater/agent.sh"
"/Users/$user/Library/Application Support/verx_updater/verx.sh"
"/Users/$user/Library/Application Support/verx_updater"
"/Users/$user/Library/Launchagents/agent.plist"
"/Users/$user/Library/Launchagents/init_agent.plist"
"/Users/$user/Library/Launchagents/verx.plist"
"/Users/$user/Library/Launchagents/init_verx.plist"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 03:15 AM
Quick & d... modified EA and Removal Script to include all existing user accounts:
Removal Script scoped on infected clients:
#!/bin/bash
# Created 20210222 by Nathan Worster
# edited 20210304 by Rémi Brinckmann
# Portions adapted from @ehemmete
# Last modified: 20210222
###############
# Variables #
###############
useraccounts=$(ls /Users/ | grep -v Shared)
result=()
filesFound=0
exitCode=0
for user in $useraccounts
do
suspiciousFiles=(
"/Applications/tasker.app"
"/tmp/agent.sh"
"/tmp/version.json"
"/tmp/version.plist"
"/tmp/agent"
"/tmp/verx"
"/Users/$user/Library/._insu"
"/Users/$user/Library/Application Support/agent_updater/agent.sh"
"/Users/$user/Library/Application Support/verx_updater/verx.sh"
"/Users/$user/Library/Application Support/verx_updater"
"/Users/$user/Library/Launchagents/agent.plist"
"/Users/$user/Library/Launchagents/init_agent.plist"
"/Users/$user/Library/Launchagents/verx.plist"
"/Users/$user/Library/Launchagents/init_verx.plist"
)
###############
# Script #
###############
for suspiciousFile in "${suspiciousFiles[@]}"; do
#echo "Looking for $suspiciousFile in User Profile of $user"
if [ -e "$suspiciousFile" ]; then
filesFound=$(expr $filesFound + 1)
infected+=("$suspiciousFile")
echo "Found $suspiciousFile - trying to remove it"
rm -rf "$suspiciousFile"
if [[ $? -gt 0 ]]; then
echo "ERROR: Could not remove $suspiciousFile"
exitCode=1
infected+=("$suspiciousFile")
else
echo "SUCCESS: Removed $suspiciousFile"
cleaned+=("$suspiciousFile")
fi
fi
done
done
if [ $exitCode -ne 0 ]; then
echo "Files that could not be deleted: ${infected[@]}"
else
echo "All Files removed: ${cleaned[@]}"
fi
exit $exitCodeModified EA:
#!/bin/bash
# Created 20210222 by Nathan Worster
# edited 20210304 by Rémi Brinckmann
# Portions adapted from @ehemmete
# Last modified: 20210222
###############
# Variables #
###############
useraccounts=$(ls /Users/ | grep -v Shared)
result=()
filesFound=0
for user in $useraccounts
do
suspiciousFiles=(
"/Applications/tasker.app"
"/tmp/agent.sh"
"/tmp/version.json"
"/tmp/version.plist"
"/tmp/agent"
"/tmp/verx"
"/Users/$user/Library/._insu"
"/Users/$user/Library/Application Support/agent_updater/agent.sh"
"/Users/$user/Library/Application Support/verx_updater/verx.sh"
"/Users/$user/Library/Application Support/verx_updater"
"/Users/$user/Library/Launchagents/agent.plist"
"/Users/$user/Library/Launchagents/init_agent.plist"
"/Users/$user/Library/Launchagents/verx.plist"
"/Users/$user/Library/Launchagents/init_verx.plist"
)
###############
# Script #
###############
for suspiciousFile in "${suspiciousFiles[@]}"; do
#echo "Looking for $suspiciousFile in User Profile of $user"
if [ -e "$suspiciousFile" ]; then
filesFound=$(expr $filesFound + 1)
result+=("$suspiciousFile")
fi
done
done
if [ $filesFound -ne 0 ]; then
echo "<result>"Yes: "${result[@]}</result>"
else
echo "<result>No</result>"
fi
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 08:37 AM
How many people actually found infections?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 08:56 AM
So far I've found five, while our AV has detected one. Manually searching through each, I ended up edited the above to include the following directories:
~/Library/Application Support/com.tasks.updater/
~/Library/Application Support/com.hello.tasker/
5 out of 2,400 macs
Seen on 10.14.x-10.15.x
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 10:02 AM
It would probably be useful to know fleet size also. I currently have not seen any infections out of about 300 machines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 10:02 AM
@maristchris Using a script to detect I've seen zero. We also have SentinelOne so I don't know if that might have found something and dealt with it. I don't have access to that side of things to know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 10:11 AM
Nothing here. About 150 Macs. Nothing in the McAfee EP either. Thanks for the scripts and EA above!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 01:42 PM
Appreciate the scripts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-07-2021 11:56 PM
Hi @rbrinckmann I used your Modified EA and now it is showing my whole Computers numbers that are enrolled... I think I have messed up something.. I tried to use the earlier EA @ncworster mentioned and it is still showing numbers of all enrolled machines. Any advice?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2021 11:14 AM
@agakhan_admin How is your Smart Group setup?
Try: name of your Extension Attribute
Operator: Like
Value: Yes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2021 09:10 PM
@atomczynski Thank you, Value was missing. I put it.
Further, now there were 2 MacBook that was detected earlier with the suspect files, the count it detected is "0" now. They are gone, not sure how. Any idea?