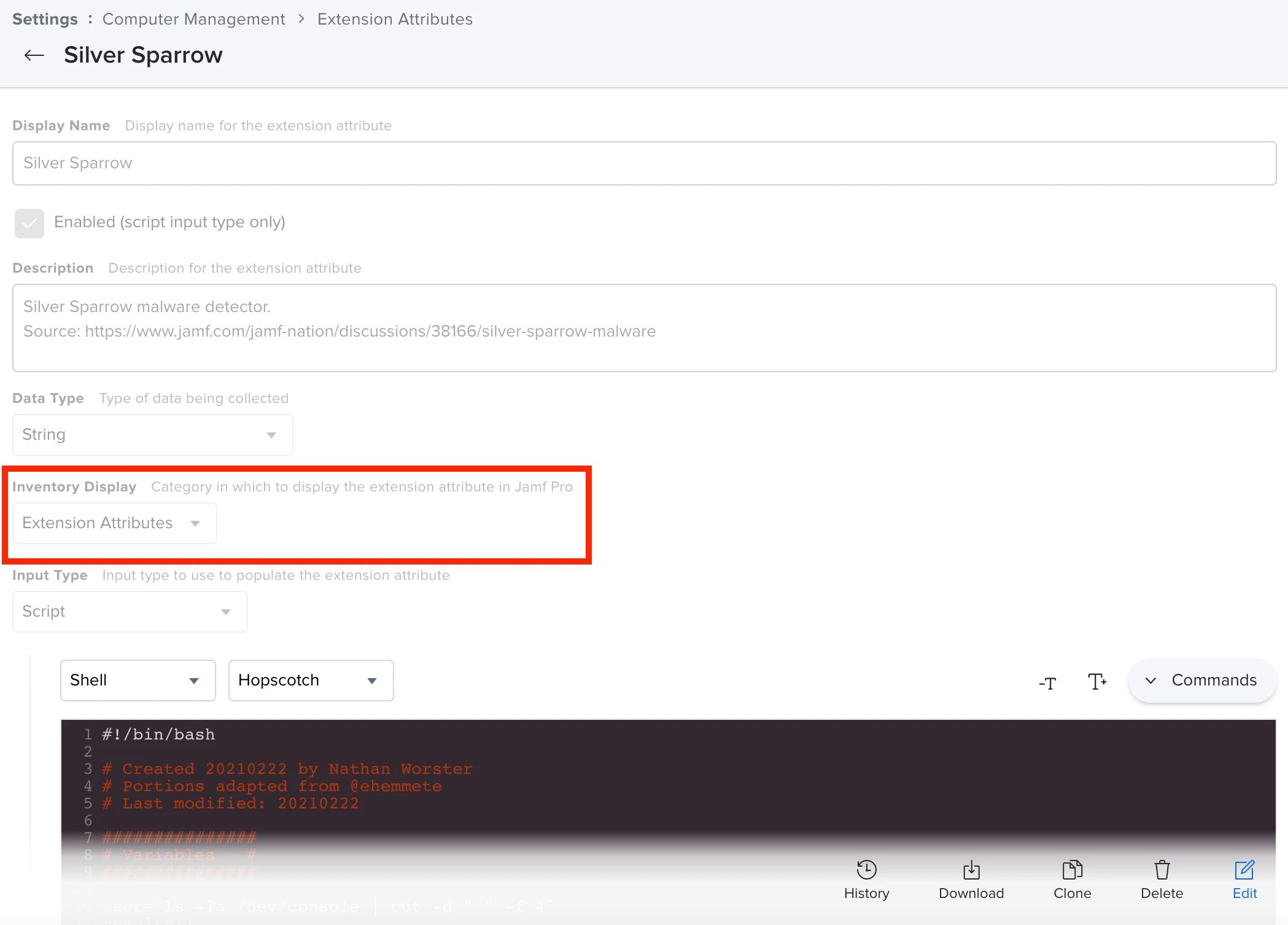
I just read about this new malware found to have infected 30,000 macs. Here's the link to information: https://redcanary.com/blog/clipping-silver-sparrows-wings/
Has anyone come up with some strategies to find and remove this from macs in their environment?
Thanks for sharing.