- Jamf Nation Community
- Products
- Jamf Pro
- Re: Smart group with computers on local network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
03-08-2018
06:51 AM
- last edited on
03-04-2025
05:21 AM
by
![]() kh-richa_mig
kh-richa_mig
I'm trying to determine if a Mac is On or Off the Corporate Network when scoping policies and a found @Rosko Joshua Roskos process on his git hub page https://github.com/jamfprofessionalservices/macNetworkLocation
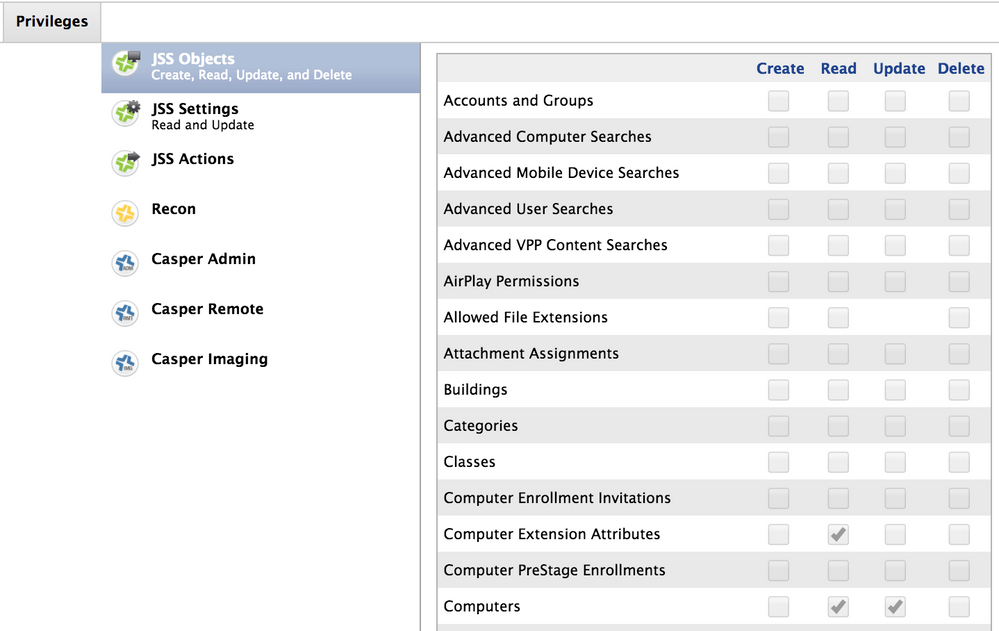
The Issue I have run into is the API user w/ the following permissions:
Read & Update permission for Computer Objects
Read permission for Computer Extension Attributes
I found Computer Extension Attributes but not Computer Objects, there is Computers but if I give this Read & Update permission the script fails at "Sending network location to Jamf Pro..."
If I give the API user full admin permission the script is successful, so just need to fins out what permissions the API account needs
Solved! Go to Solution.
- Labels:
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2018 06:55 AM
After much trial and error the permissions for API user are;
- Read & Update permission for Computers
- Read permission for Computer Extension Attributes
- Update permission for Users
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2018 06:55 AM
After much trial and error the permissions for API user are;
- Read & Update permission for Computers
- Read permission for Computer Extension Attributes
- Update permission for Users
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2018 07:45 AM
Hmm. I like the idea of this process @Rosko has put together. My only issue with it is I don't see a way that it can be used to update a computer's Network Segment, which we use to determine which distribution point a Mac should be pointed to for policies. As we have a Limited Access JSS in a cluster, external clients can run policies, but the one consistent problem I face is that unless I'm constantly on top of getting new network IP ranges input into Jamf Pro as they are set up in the organization, some Mac clients believe they are on the outside (if their IP doesn't fall into a known range) and policies fail since the DMZ distribution points can't be hit when inside the network, only when outside.
I would love to use something like what he's outlined to help there, but unless I can also point Macs to the correct DP with it, I don't know that it would help much.
Still, interesting concept. I will play with this and see if I can use it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2018 08:12 AM
@burdett Sorry about that, I will get the notes updated on GitHub!
@mm2270 Unfortunately since the "default distribution point" is handled by the WebApp at check-in when executing a policy there is no way to override the default DP (except at the package level which would apply to everyone). I like the idea, but unfortunately I don't have a great way to implement this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2018 09:03 AM
Yes, thanks for the response @Rosko I suspected that was the case. I wish there was a way to use something like what you've put together to override that, even maybe with an API call, but I don't see a way to do that. As I mentioned, keeping on top of the near constantly changing IP range landscape in a large org is a full time job. I often don't "discover" there are new subnets until I start seeing some Macs fail policies because they are trying to hit our DMZ distribution points while inside the network. As an aside, if anyone has ideas on how to automate keeping IP ranges in sync in the JSS, I'm open to suggestions.
I've still put up your EA and the script (both with some modifications) and am testing it on a few systems now. The only issue I see, occasionally, is that the network state trigger doesn't always kick in and run the policy as it should, which means a Mac may not get an updated EA value if that happens. But that has nothing to do with your process, just an issue with Network State Change in policies I think. Other than that, it works well so far.