- Jamf Nation Community
- Products
- Jamf Pro
- Re: System Extension [activated waiting for user]
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
System Extension [activated waiting for user]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2020 11:57 AM
I'm working on setting up a policy for GlobalProtect 5.1.4 which switches to System Extension from Kernel Extensions.
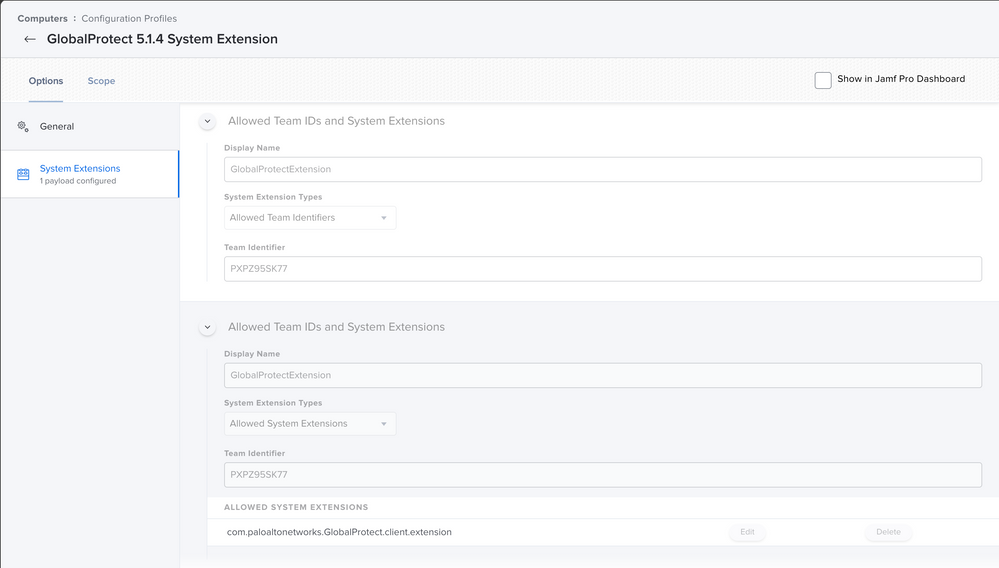
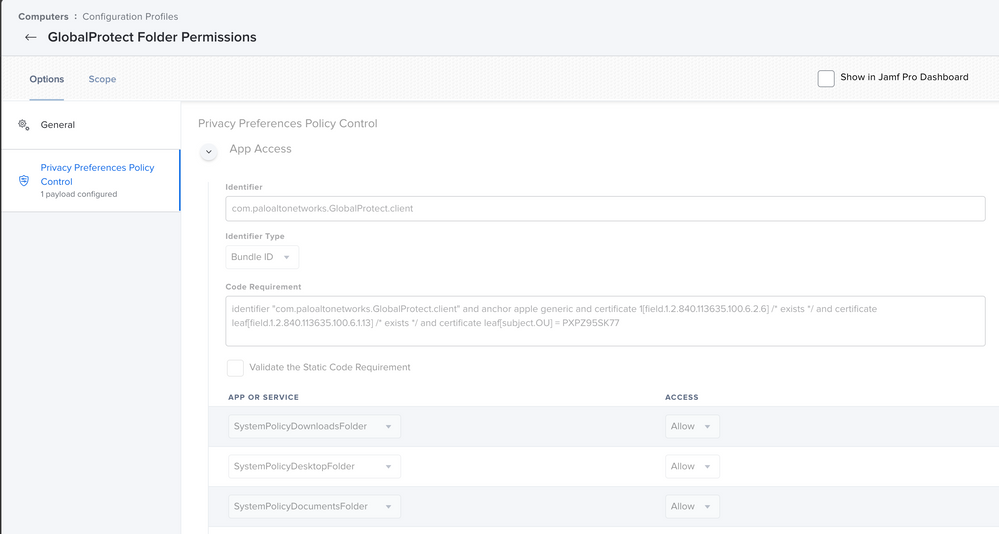
I've set up a config profile to approve the system extension.
First I tried just the team ID, then I added the ALLOWED SYSTEM EXTENSIONS as well.
but when I run systemextensionsctl list I get
1 extension(s)
--- com.apple.system_extension.network_extension
enabled active teamID bundleID (version) name [state]
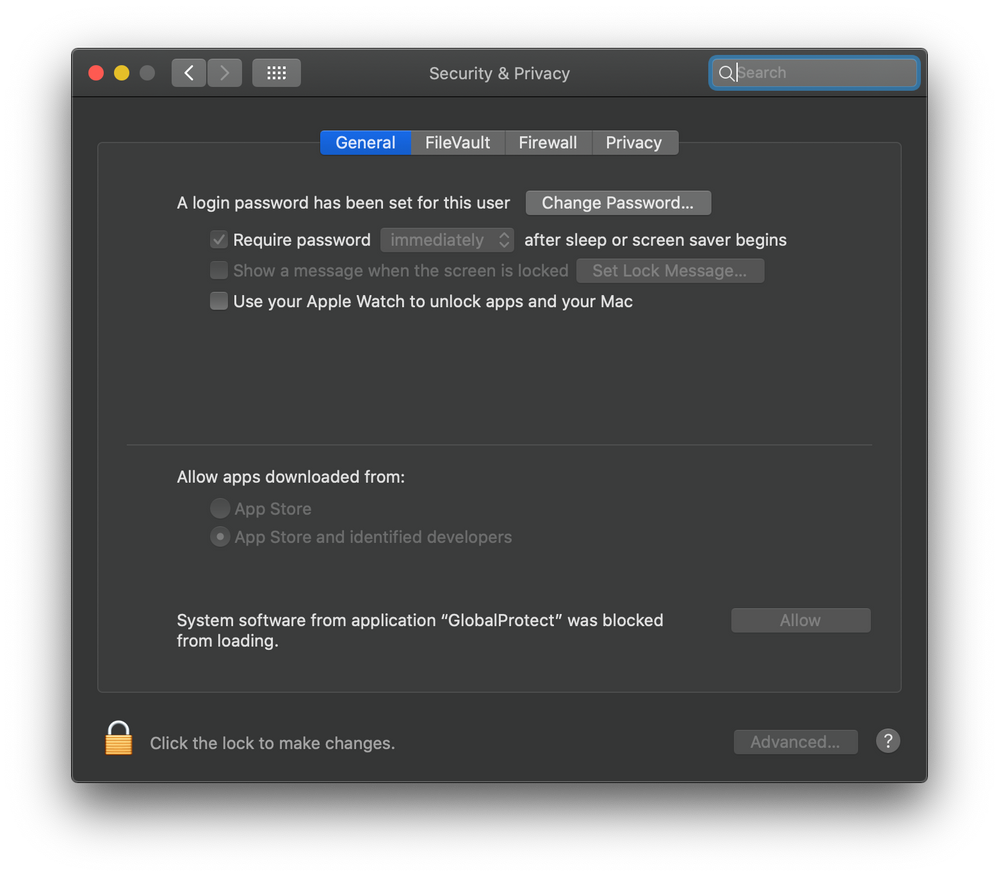
* PXPZ95SK77 com.paloaltonetworks.GlobalProtect.client.extension (5.1.4-45/1) GlobalProtectExtension [activated waiting for user]and System Preferences>Security & Privacy still has this prompt
How can I approve this for the user?
I tried a blanket PPPC config profile that just gave it all access, but still have that prompt.
Anyone know how to solve this?
- Labels:
-
Configuration profiles
-
Policies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2020 03:32 PM
The configuration profile must be present before the client (and system extension) are installed, otherwise the user will still be prompted to allow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-12-2020 09:06 PM
#racecondition
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-13-2020 09:28 AM
Unfortunately, yes. I'm also not sure 'blanket' system extensions work in the same way they do with kernel extensions.
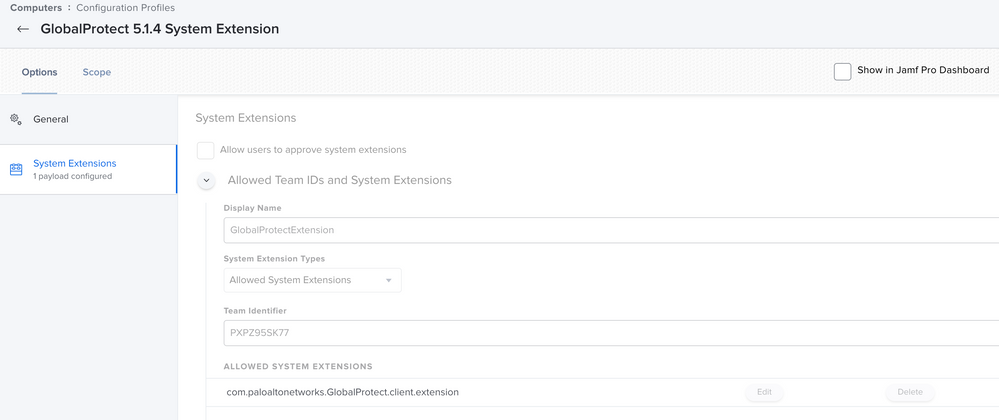
I had to explicitly name the extension in addition to providing the Team ID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-13-2020 10:38 AM
Correct with SEXT both team ID and extension name, however its appears there in the profile, perhaps the 1st section of the profile that lists just the team id only should be removed, for GP 5.1.4 I only have the 2nd item in the config TeamID and SEXT named. and its working for me. of course I still have the config layed down prior to deployment as its needed. FYI I also still have the GP KEXT profile on these machines as we are in transition haven't tried clean in stall without that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-13-2020 02:13 PM
Technically these are duplicates with conflicting permission. You may have been overly specific with the second item.
AFAIK the only reason to populate the "allowed system extensions" area is if you intend to whitelist only certain sexts from the same Team ID while blocking all other sexts. Inasfar as you trust the vendor, you should allow them all.
Remove the second payload and see what happens.
(On another note, why didn't Apple call these things Mac Extensions / MEXT, or Apple Extensions / AEXT, or User Extensions / UEXT? I fail to understand how this made it all the way through the development cycle and got product marketing's blessing.
Somebody in the SWE group went through the trouble of calling the utility systemextensionsctl instead of sextctl, which would have otherwise mirrored the previous kext prefixes for that family of utilities. This suggests that someone was paying attention and danced around the issue during their scrum meetings.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-13-2020 06:22 PM
I believe for system extensions they can not be whitelisted with just team id (like KEXTS can be) they must Alis list the System Extension itself (so for me the 2nd part of the config profile with the names system extension com.paloal.xxxx must be used, it might not be working as the 1st part of the config profile lists only the team id and perhaps its getting stuck on that part, try a config profile with only the 2nd item listing the system extension by name and deploy system extension and install the app to see if it properly whitelists and enables the system extension
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2020 09:55 AM
Looking to see if there was an open PI regarding signed Configuration Profiles uploaded to JSS 10.21.0, I came across this PI for System Extensions that sounds like it might be applicable here:
PI-007713 Jamf Pro fails to include the Allowed Team Identifiers setting in the System Extensions payload of a computer configuration profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2020 11:29 AM
@jkryklywec @bradtchapman I used only the second payload, and also made sure the profile was installed before the software was installed and that seems to have resolved the issue. At least on my test computer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-15-2020 01:16 PM
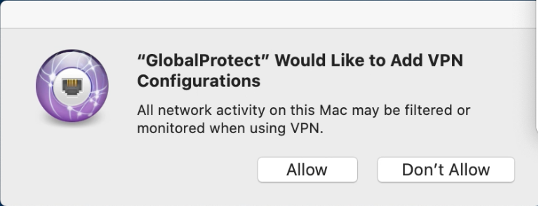
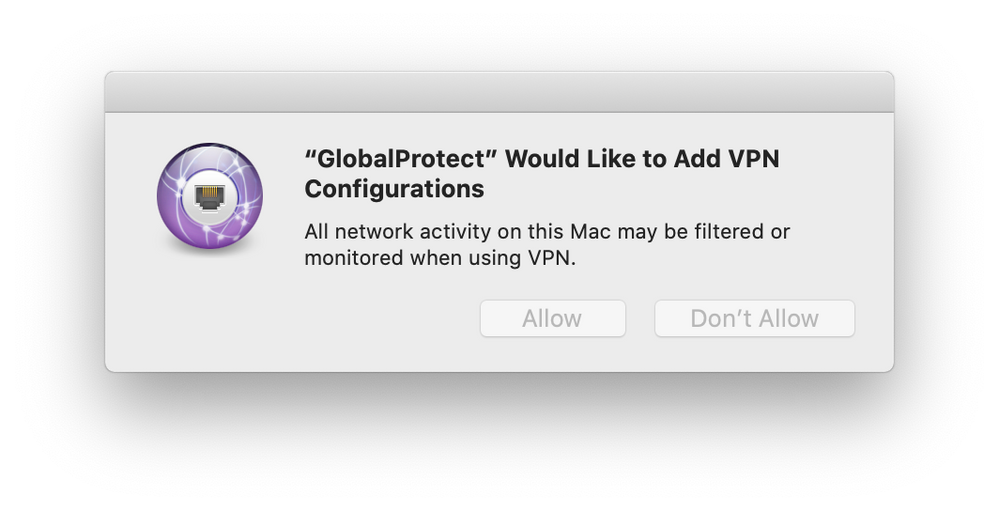
I can get the extension trusted
but my issue is that end users will now receive a prompt stating ""GlobalProtect" Would like to Add VPN Configurations" with an Allow or Don't Allow button. I'd like to suppress that or automate the choice of "Allow"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2024 01:01 PM
I am curious to find out if you figure out how to suppress that pop up so user don't see the pop up at all, it will automatically allowed it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-15-2020 11:38 PM
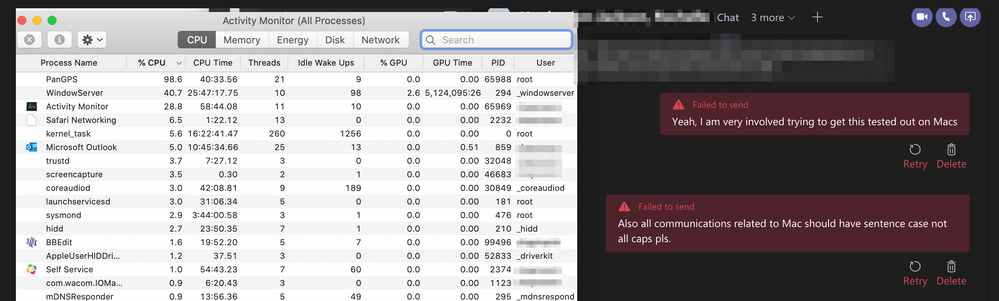
We started having issues with 5.0.8-4 and Catalina where any O365 traffic was having issues with Autosave (Word, Excel, PPT), syncing with OneDrive, Sharepoint (sites not loading), websites not loading completely, and Teams not sending messages. If the Gateway was changed or the GPCS was refreshed then the behavior briefly went away until the Gateway reconnected. Some days it was impossible to work, so I was able to disable VPN, but for end users, it's set to be always on.
I imagine that most users will just bypass autosave and save locally, which defeats the purpose of having OneDrive.
We opened a case with Palo Alto, Microsoft, and Apple. Palo Alto said it was a Safari issue. Microsoft confirmed that they use Webkit in their apps, Apple said, hey we'd love to help (and I don't know what behind the scenes things might be happening, but there is no partnership that I know of between Palo Alto and Apple, so its a crapshoot?)
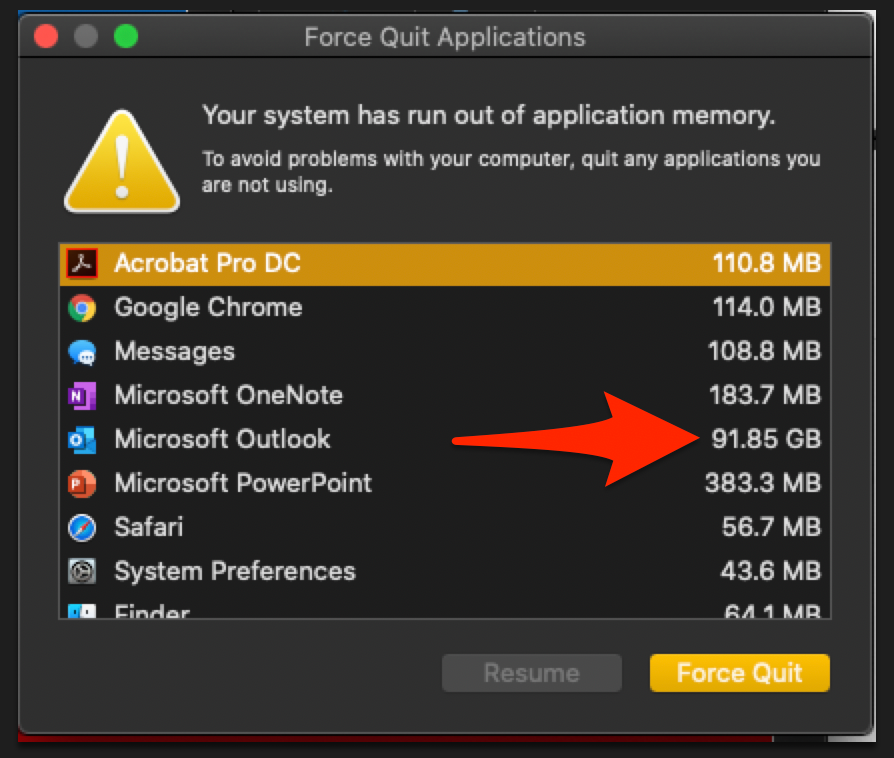
One user got this from his ISP (COX Communications) along with his system warning him of his apps running out of memory.
So Moving to 5.1.4-45 was supposed to fix this issue, except that at the time our version of Jamf didn't support the System Extension payload and there was little or very hard to find documentation for Mac on Palo Alto's site. Until this weekend when we upgraded from Jamf Pro 10.13.1 to 10.22.1 (yeah, I know). Still, now that we have the payload, we reached out to Palo Alto once again for documentation on how to configure their stuff, and I feel bad for the engineer, who was very helpful, even though he ended up finding this same article. (Personally, I think the devs don't know that MDM also applies for Mac, but whatever.)
Because of this oversight, they shared with us that the kext would be removed but don't account for the fact that it being whitelisted by MDM stays put, until the device is taken out of scope for the KEXT whitelist config profile. To me it would appear that support for Catalina may have been dropped altogether.
I tested 5.1.4-45 on a 13" 2018 MBP with 10.15.5 by completely uninstalling GPCS (with their uninstaller). Allowed the system Extension, manually, and still had issues with Teams. All other o365 products works as expected. Once I un-scoped the KEXT Profile, Teams and the Office apps worked without issue.
So now all that's left is to test this payload and address the issue @daniel.behan regarding ""GlobalProtect" Would like to Add VPN Configurations" with an Allow or Don't Allow button.
But there is also one other issue that I am chasing a screenshot of, which is a Keychain login prompt. I should be talking to the engineer again before the week is out. I'll post my findings here once I hear back.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-16-2020 06:50 AM
@daniel.behan @TechM I think the allow VPN prompt comes from GP being on the computer Before the system extension config profile. When that happens I uninstall and reinstall GP. (we have a Self Service policy configured that Wipes GP off the computer, and reinstalls it and sets it back up. So I just tell Users to click that button and it's stopped that "Add VPN Configurations" prompt 100% of the time.
Regarding the keychain prompt, the user just needs to enter their password and click always allow. There isn't really another way around it that I've ever figured out, and I've asked about it and looked into it a decent amount.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-16-2020 08:43 AM
@strayer @daniel.behan Our challenge is the business wants this to be Always On and have as little user interaction as possible. Basically they want it totally automated.
I've found the article that talks about the Keychain login prompt.
https://docs.paloaltonetworks.com/globalprotect/5-1/globalprotect-app-release-notes/gp-app-release-information/globalprotect-app-upgrade-downgrade-considerations.html
Among other things, it says: "The following Keychain pop-up prompt can appear if the Save User Credentials option is enabled in the portal configuration"
As for my test results from setting those two payloads, some of the issues came back that were experienced with Teams:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-17-2020 07:22 AM
@strayer I'd be curious to see how to avoid the prompt to allow a vpn configuration. I get it every time, even installing manually. And now there's an issue with PPPC because the bundle ID changed from com.paloaltonetworks.GlobalProtect in version 5.0.x to com.paloaltonetworks.GlobalProtect.client in version 5.1.x
I was able to make another profile for version 5.1.x, but it only works for new builds, but not upgrades. When a user upgrades, the Profile isn't honored. I had version 5.0.x uninstalled, reset the TCC settings on the Mac, applied the new Profile, then installed 5.1.x and it still prompted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-17-2020 07:50 AM
@daniel.behan I'm really not sure why your experience is much different than mine, That prompt has only happened for us a few times, and each time our Reset GlobalProtect policy has fixed it.
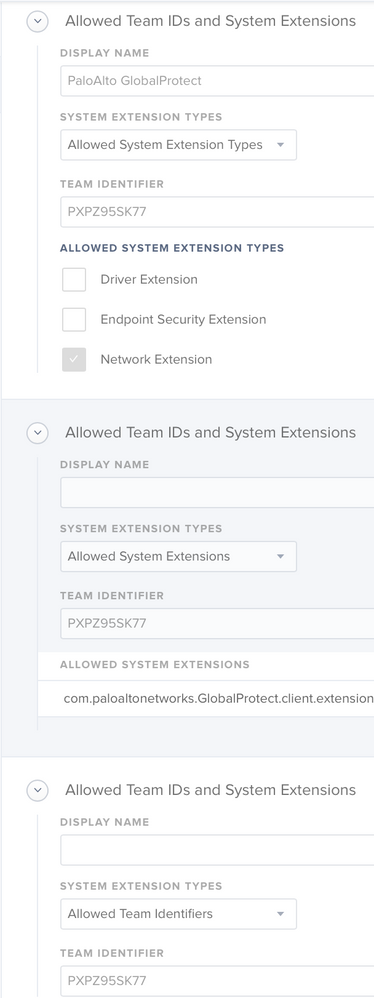
I've attached screenshots of the 2 GlobalProtect related config profiles that are pushed to every Catalina Machine.
Our "Reset GlobalProtect" Self service option triggers 3 other policies in a row.
First is the uninstall global protect
then it installs the relevant GlobalProtect settings (a .plist that presets the portal). (we initially developed this to switch users from one portal to another automatically, but it has become a useful troubleshooting step for us.)
then it reinstalls the GlobalProtect application.
Here is the script that I use to uninstall, I used suspicious package to take it out of the GlobalProtect install package.
#!/bin/sh
is_debug=1
if [[ "$1" ]] && [ $1 = "-d" ]; then
is_debug=1
fi
echo "is_debug=$is_debug"
USER_ID=`id -u`
if [ "$USER_ID" -ne 0 ]; then
echo "You must be root to run the script. Use sudo $0"
exit
fi
CONSOLE_USER=`stat -f "%Su" /dev/console`
CONSOLE_HOME=`eval echo ~${CONSOLE_USER}`
run_as_console_user=1
console_user_id=`id -u ${CONSOLE_USER}`
if [ $CONSOLE_USER = "root" ]; then
run_as_console_user=0
fi
install_dir=/Applications/GlobalProtect.app/Contents/Resources
app_log_dir=/Library/Logs/PaloAltoNetworks/GlobalProtect
mkdir -p "$app_log_dir"
uninstall_log_dir=$app_log_dir/PanGPInstall.log
if [ $is_debug -eq 1 ]; then
uninstall_log_dir=/var/log/PanGPUninstall.log
fi
exit_code=0
((
checkAndWaitProcess()
{
if [[ "$2" ]]; then
T="$2"
else
T=5
fi
C=0
while [[ C -lt $T ]] &&
( killall -s "$1" >/dev/null 2>/dev/null )
do
let C=C+1
sleep 1
done
killall -s $1 >/dev/null 2>/dev/null
return $?
}
pan_info()
{
curtime=`date`
echo $curtime ' ' $1 >> ${uninstall_log_dir}
}
curver=`defaults read ${install_dir}/../Info CFBundleShortVersionString`
echo "
"
pan_info "Uninstalling GlobalProtect version ${curver}, console user ${CONSOLE_USER}, home ${CONSOLE_HOME}"
pan_info "unloading gp agent"
if [ $run_as_console_user -eq 1 ]; then
launchctl bootout gui/$console_user_id /Library/LaunchAgents/com.paloaltonetworks.gp.pangps.plist
launchctl bootout gui/$console_user_id /Library/LaunchAgents/com.paloaltonetworks.gp.pangpa.plist
else
launchctl remove com.paloaltonetworks.gp.pangps
launchctl remove com.paloaltonetworks.gp.pangpa
fi
pan_info "unloading gp daemon"
launchctl remove com.paloaltonetworks.gp.pangpsd
#wait for 15 sec. while PanGPS quits
if checkAndWaitProcess "PanGPS" 60; then
pan_info "PanGPS didn't quit within 60 sec. Killing"
killall -15 PanGPS
if checkAndWaitProcess "PanGPS" 30; then
pan_info "PanGPS didn't quit after SIGTERM within 30 sec."
fi
fi
#wait for 5 sec. while GlobalProtect quits
if checkAndWaitProcess "GlobalProtect" 5; then
pan_info "GlobalProtect didn't quit within 5 sec. Killing"
killall -15 GlobalProtect
if checkAndWaitProcess "GlobalProtect" 5; then
pan_info "GlobalProtect didn't quit after kill within 5 sec."
fi
fi
ps aux | grep "/Applications/GlobalProtect.app/Contents/Resources/PanGPS" | grep -v grep
if [ $? -eq 0 ]; then
pan_info "PanGPS is still running, force exit"
killall -9 PanGPS
else
pan_info "PanGPS has stopped"
fi
ps aux | grep "/Applications/GlobalProtect.app/Contents/MacOS/GlobalProtect" | grep -v grep
if [ $? -eq 0 ]; then
pan_info "GlobalProtect is still running, force exit"
killall -9 GlobalProtect
else
pan_info "GlobalProtect has stopped"
fi
#check if agent and daemon has been removed from launchd
if [ $run_as_console_user -eq 1 ]; then
if launchctl print gui/$console_user_id/com.paloaltonetworks.gp.pangps > /dev/null 2>&1; then
pan_info "pangps agent not be removed"
exit_code=249
else
pan_info "pangps agent has been removed"
fi
if launchctl print gui/$console_user_id/com.paloaltonetworks.gp.pangpa > /dev/null 2>&1; then
pan_info "pangpa agent not be removed"
exit_code=249
else
pan_info "pangpa agent has been removed"
fi
fi
if launchctl print system/com.paloaltonetworks.gp.pangpsd > /dev/null 2>&1; then
pan_info "pangpsd daemon not be removed"
exit_code=249
else
pan_info "pangpsd agent has been removed"
fi
pan_info "Unloading driver"
ifconfig gpd0 down > /dev/null 2>&1
kextstat -b com.paloaltonetworks.kext.pangpd | grep com.paloaltonetworks.kext.pangpd | grep -v grep
if [ $? -eq 0 ]; then
pan_info "unloading pangpd driver."
kextunload -b com.paloaltonetworks.kext.pangpd
fi
kextstat -b com.paloaltonetworks.GlobalProtect.gpsplit | grep com.paloaltonetworks.GlobalProtect.gpsplit | grep -v grep
if [ $? -eq 0 ]; then
pan_info "unloading split tunnel driver"
kextunload -b com.paloaltonetworks.GlobalProtect.gpsplit
fi
kextstat -b com.paloaltonetworks.GlobalProtect.gplock | grep com.paloaltonetworks.GlobalProtect.gplock | grep -v grep
if [ $? -eq 0 ]; then
pan_info "unloading enforcer driver"
kextunload -b com.paloaltonetworks.GlobalProtect.gplock
fi
if kextstat -b com.paloaltonetworks.kext.pangpd | grep com.paloaltonetworks.kext.pangpd | grep -v grep; then
pan_info "unload pangpd kext failed."
exit_code=250
fi
if kextstat -b com.paloaltonetworks.GlobalProtect.gpsplit | grep com.paloaltonetworks.GlobalProtect.gpsplit | grep -v grep; then
pan_info "unload gpsplit kext failed."
exit_code=250
fi
if kextstat -b com.paloaltonetworks.GlobalProtect.gplock | grep com.paloaltonetworks.GlobalProtect.gplock | grep -v grep; then
pan_info "unload gplock kext failed."
exit_code=250
fi
pan_info "cleaning up sso"
cd ${install_dir}
./PanGPS -dsso
pan_info "Cleanup Dynamic Store"
echo "remove State:/Network/Service/gpd.pan/IPv4" | scutil
echo "remove State:/Network/Service/gpd.pan/DNS" | scutil
pan_info "rm all"
rm -f "/Library/LaunchAgents/com.paloaltonetworks.gp.pangps.plist"
rm -f "/Library/LaunchAgents/com.paloaltonetworks.gp.pangpa.plist"
rm -f "/Library/LaunchDaemons/com.paloaltonetworks.gp.pangpsd.plist"
rm -rf "/Library/Application Support/PaloAltoNetworks/GlobalProtect"
rm -rf "/Applications/GlobalProtect.app"
rm -rf "/Applications/GlobalProtect.app.bak"
rm -rf "/System/Library/Extensions/gplock.kext"
rm -rf "/Library/Extensions/gplock.kext"
rm -rf "/Library/Security/SecurityAgentPlugins/gplogin.bundle"
rm -rf /Library/Preferences/com.paloaltonetworks.GlobalProtect*
rm -rf /Library/Preferences/PanGPS*
if [ $run_as_console_user -eq 1 ]; then
pan_info "removing gp user config files in (${CONSOLE_HOME})."
rm -rf "$CONSOLE_HOME/Library/Application Support/PaloAltoNetworks/GlobalProtect"
rm -rf "$CONSOLE_HOME"/Library/Preferences/com.paloaltonetworks.GlobalProtect*
rm -rf "$CONSOLE_HOME"/Library/Preferences/PanGPS*
#remove password entry from keychain
security delete-generic-password -l GlobalProtect -s GlobalProtect "${CONSOLE_HOME}/Library/Keychains/login.keychain-db"
fi
#10.9 addition to clear system preferences cache
killall -SIGTERM cfprefsd
pan_info "uninstall packages from globalprotect"
for pkg in `pkgutil --pkgs |grep com.paloaltonetworks.globalprotect`
do
pkgutil --forget "$pkg"
done
rm -rf /Library/Logs/PaloAltoNetworks/GlobalProtect/*
pan_info "Uninstallation finished."
exit $exit_code
) 2>&1) >> ${uninstall_log_dir}- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-17-2020 07:01 PM
UPDATE:
Setting up two different Config Profiles to test with individually still has issues with connectivity with Teams and other internet connectivity. The only thing being managed at this point is the Config Profile.
The Mac is scoped.
Config Profile is verified.
Software is installed with the installer with the System Extensions box checked.
Both make no difference as it relates to performance.
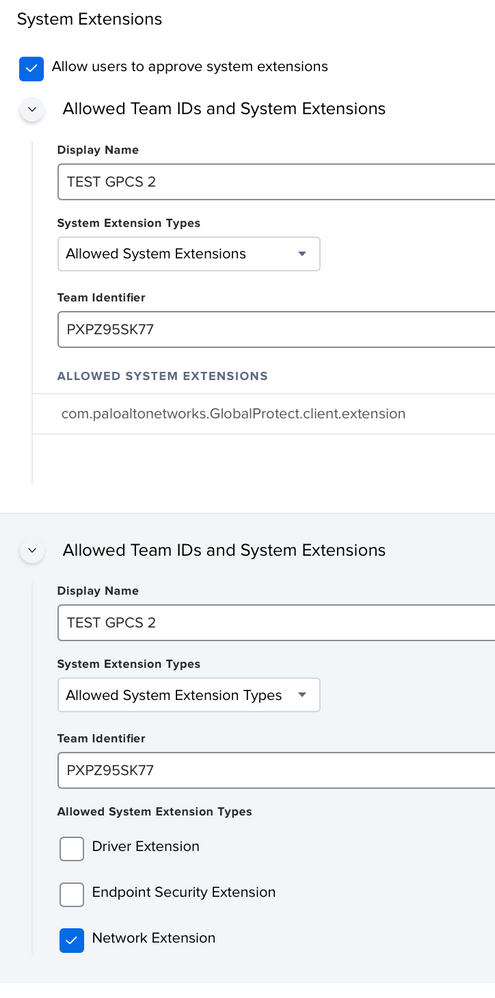
CP #1
CP#2
We still see this prompt:
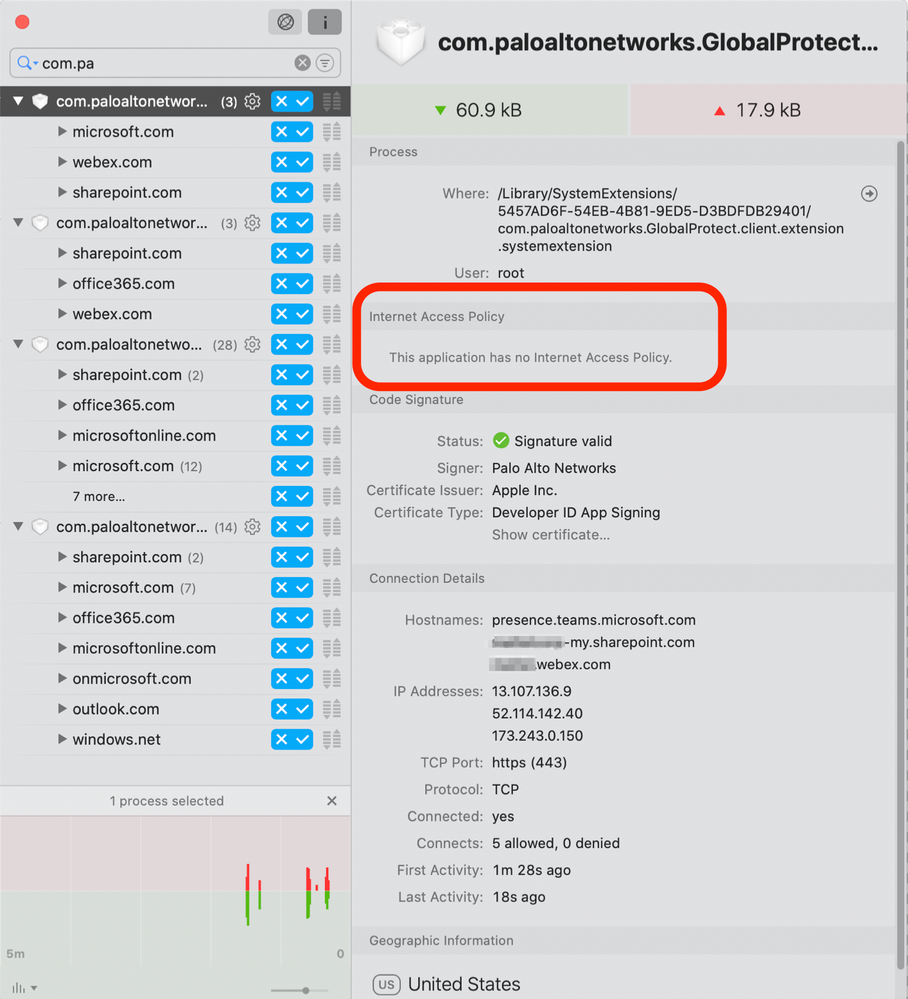
So then I looked in Little Snitch and I see this:
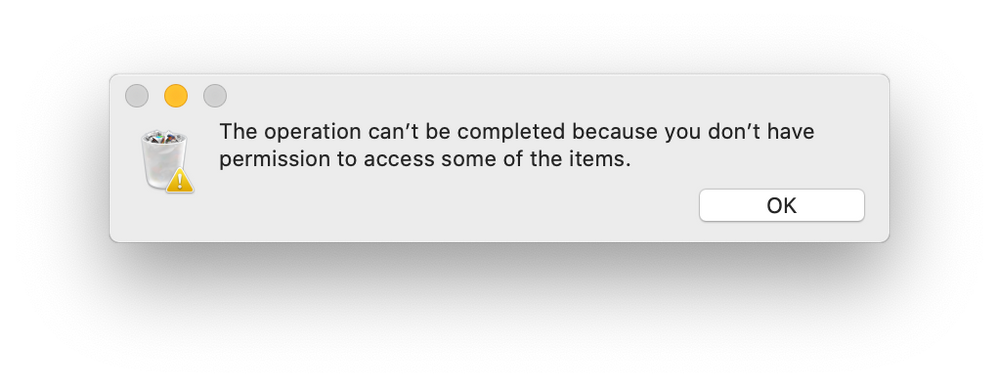
So that message is strange. I can't find any documentation on it. But I go and look at what's in that folder referenced above and I see each system extension for every time I installed GPCS. I tried uninstalling it while having it opened, and they don't come out. I tried deleting them myself and I get this message:
It was almost 1AM so I called it a night. I'm at a total loss here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2020 12:53 PM
Curious if anyone has managed to stop this VPN prompt from coming back up?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-21-2020 01:30 PM
@aarron.tilley https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u000000HAW8 there are 4 config profiles linked on the article on their support site. I looked at the name of the network configuration (GlobalProtectDo) that the pop up was making and matched it to the one made by one of the config profile. (GlobalProtectSplitTunnelDomain) and that solved it for me so far. Hopefully that solves it for good.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-01-2020 02:46 PM
Thanks @strayer, that did solve it for me
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2020 04:00 PM
@strayer or @aaron.tilley I'm testing Global Protect with Big Sur beta & not having much luck... would you mind providing further details of the PA link above? I can't seem to get to the article. Thanks!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-03-2020 07:31 AM
@jonw I haven't actually used it with Big Sur yet, unfortunately Palo keeps those behind a login wall. There are 4 config profiles on that page that you can download and install, If you don't have a login I'd suggest you have someone on your network team to log in and get them for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-03-2020 11:21 AM
@strayer Thanks, that's what I figured. Seems like an odd bit of info to obscure though. I have a ticket in to our network team, hopefully I'll hear something soon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2020 06:59 AM
Has anyone found a way to install the system extensions by default on macOS Big Sur? When manually running the installer you can check the box, but it's unclear if they install by default on Big Sur. I'm not getting any prompts which suggests they are not, but perhaps they do install if the required MDM profiles are installed on the system?
PAN support are in the dark on this one and point me to KB articles that don't really apply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2020 08:17 AM
i use this script from the package and run after pkg install and it installs the SEXT
#!/bin/sh
out_dir="/Library/Logs/PaloAltoNetworks/GlobalProtect"
pan_info()
{
curtime=`date`
echo $curtime " " $1 >> ${out_dir}/PanGPInstall.log
}
pan_info "Install system extensions after installation"
sudo mkdir -p "/Library/Application Support/PaloAltoNetworks/GlobalProtect"
sudo touch "/Library/Application Support/PaloAltoNetworks/GlobalProtect/install_system_extensions.now"
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-07-2020 07:35 PM
With GlobalProtect 5.2.3 my experience on macOS Catalina 10.15.7 is that even if you don’t specifically set the flag for installing the System Extension with a Choices XML file or the flag file mentioned above it will still be installed the first time a connection is enabled (I do have a Configuration Profile deployed with the appropriate enablements for GlobalProtect). I have not tested this yet on Big Sur.
Update 2021-04-21: With GlobalProtect 5.2.5-84 and macOS Big Sur 11.2.3 on an M1 Mac it appears that you can't rely on automatic installation of the GlobalProtect System Extension on the first connection attempt.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-09-2020 01:26 PM
Thanks @jkryklywec, @sdagley. Time to start testing!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-10-2020 09:06 AM
@sdagley Right, but if the set up is that you can't log into the client because the connection is needed to verify that it's you, then it's a chicken and egg situation. Meanwhile the user gets prompted with asks to allow for extensions where the buttons are not clickable and in the case of standard users they can't allow for the extension in System Prefs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-10-2020 09:58 AM
@TechM If you deploy a Configuration Profile to approve the System Extension before GlobalProtect is installed then the user won't see that prompt.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-11-2020 10:07 AM
@sdagley I should have stated that this is the behavior with all the provided config profiles provided by Palo Alto that's on the KB behind the sign-in page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-11-2020 10:27 AM
@TechM Those Configuration Profiles are for enabling specific functions of the GP client that require payloads not yet directly supported as of Jamf Pro 10.25.1. You still need to create the Configuration Profile with the System Extension payload described in the Enable System and Network Extensions using jamf PRO KB article.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-12-2020 10:10 AM
@sdagley Yep. All those are in there. I worked with PA to provide feedback for that page. However, when they were given the feedback that the UI was not allowing those buttons to be actioned, they ignored the feedback. All those payloads plus the ones that have to be configured on the customer end were not even on their radar until we encouraged them to update their documentation and separate their macOS KB from their iOS/iPadOS KBs.
In our case, clients MUST log in to their GP client before making a VPN connection. There is no way for that connection to be made without that login. How is GP going to know where to connect to if it can't even authenticate to begin with?
Or am I missing something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-12-2020 10:36 AM
@TechM Are you using purely AD based logins? That's not really recommended. The more common approach is to have a local account on the Mac that is password synchronized with AD via a tool like Enterprise Connect or NoMAD (or Jamf Connect to use a Cloud IdP). That way a user can authenticate as admin on their Mac without an active network connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-13-2020 10:16 AM
@sdagley Yes, this is an AD environment. We know it's not recommended and have advised the business accordingly, As for being admins, not all business have their users set as admins for lots of reasons, regardless of active network connections.
My main gripe is the UI should at least be showing the buttons in the dialog so that some sort of dismissive action can be taken and to have PA acknowledge as much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-08-2021 12:05 PM
Hello All,
Our company just got this client and I'm looking for the workflow on how to deploy the global Protect .pkg with the .plst connection file, I appreciated any help and suggestions.
I try this script and cannot deploy the client.
!/bin/sh
sudo installer -pkg /private/var/tmp/GlobalProtectVPN/GlobalProtect.pkg -target /
In addition, this is an answer from Global Protect support on a support ticket:
"We do not currently qualify JAMF as a Mac management vendor. This is why our TAC does not have complete instructions for deploying GlobalProtect with JAMF. There is an existing feature request to support this and " company" has been added as a customer interested in this. However, there is not currently any timeline or commitment for it.
Have you worked with JAMF? I have no experience with it and my inquiries to other colleagues have yielded no additional information."