- Jamf Nation Community
- Products
- Jamf Pro
- Re: Tomcat SSL Certificate Expiring in 20 days - w...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Tomcat SSL Certificate Expiring in 20 days - what to do?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 05:48 AM
We are receiving a "Tomcat SSL Certificate Expiring in 20 days" warning.
Apparently, we are using the built-in Certificate authority but since we updated this a long time ago, we aren't sure what to do.
Do we need to choose the first option, since we don't want our clients to lose their connection?
And if so, how and where do we obtain (download) this SSL Certificate Keystore for uploading into the JSS?
Your help is appreciated.
- Labels:
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 06:32 AM
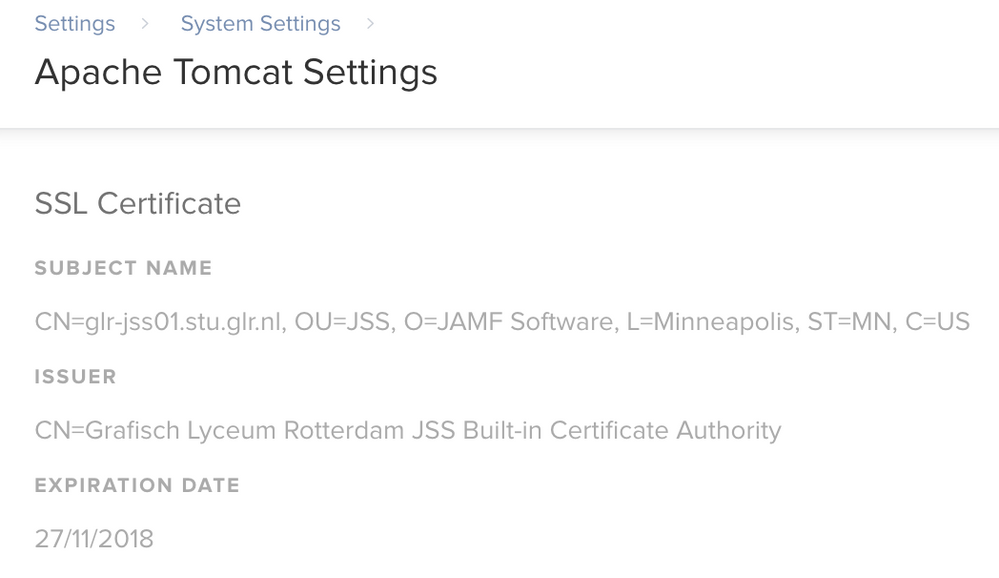
Creating or Uploading an SSL Certificate Log in to Jamf Pro. In the top-right corner of the page, click Settings Click System Settings. Click Apache Tomcat Settings Click Edit. Select Change the SSL certificate used for HTTPS and click Next. Follow the onscreen instructions to upload or create an SSL certificate. Restart Tomcat for the changes to take effect. For instructions on how to restart Tomcat, see the following Knowledge Base article: Starting and Stopping Tomcat
https://jamfnation.jamfsoftware.com/article.html?id=115
http://docs.jamf.com/10.8.0/jamf-pro/administrator-guide/SSL_Certificate.html
http://docs.jamf.com/10.8.0/jamf-pro/administrator-guide/About_This_Guide.html
hope this helps
Looking for a Jamf Managed Service Provider? Look no further than Rocketman
________________
Virtual MacAdmins Monthly Meetup - First Friday, Every Month
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 06:41 AM
You can just generate a built in certificate from the jamf pro's built in CA (the second option) in your second screenshot, but that's not really advised anymore. Mobile devices won't trust your Jamf server by default, and any modern browser will throw warnings when you try to navigate to your jamf server.
I'd strongly advise following the links @Hugonaut posted, and moving to a 3rd party SSL cert. It's a little scary to do, but if you contact Jamf support they have a 3rd party utility called Simple SSL along with documentation on how to use that. It makes generating and importing the SSL cert really easy. In the long run, the move is well worth it, so I'd suggest taking the time to do this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 07:59 AM
@DeployAdam If the built-in certificate is what has been used in the past and that is what exists on the already enrolled device, go ahead and renew that one.
To regenerate the tomcat certificates for "Built-in Certificate Authority" ONLY.
Let's go to Jamf Pro Settings > Apache Tomcat Settings: 1. Click Edit 2. Check "Change the SSL Certificate for HTTPS" and click Next 3. Check "Generate a certificate from the JSS's built-in CA and click Next 4. Click Done
Now we have to restart Tomcat: https://www.jamf.com/jamf-nation/articles/117/starting-and-stopping-tomcat
NOTE: What @float0n mentioned above is correct that Jamf recommends using a 3rd party/globally trusted SSL certificate vs the built in if possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 08:11 AM
Are going to stay with the built in certificate or move to a third party certificate?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 09:25 AM
Second moving to third party. We use DigiCert and they even coach you through doing a keystore if need be.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 11:30 AM
I deployed Let's Encrypt to secure our JAMF deploy. Happy to share the recipe.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-31-2022 01:58 AM
Hi,
I try to do that, but in vain. I have used that script at https://github.com/sean-rabbitt/letsEncryptJSS. I had to tweak it a little bit, though.
How did you do it?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 11:35 AM
Thank you all for your response
@ryan will the trust on the iMac clients automatically update themselves without a user accepting them? We have something like 2500 clients which need to keep working ;)
@blackholemac will change this in the near future
@Felipe.hernandez will migrate away from OS X Server for jamf Pro to a Linux environment, then we certainly will move away from the build-in CA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 11:37 AM
We’re you looking into a clustered environment? Because look at using ha proxy for a load balancer it’s free in a Linux box and then use easy encrypt for your ssl certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-06-2018 11:38 AM
Sorry l meant let’s encrypt ssl for the ssl certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-12-2018 01:02 AM
To all, still not bold enough to press the renew button...
will the trust on the iMac clients automatically update themselves without a user accepting them? We have something like 2500 clients which need to keep working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-12-2018 08:38 AM
@DeployAdam I can understand the fear involved.
I’ve actually been in your boat and the switch to a third party cert went off without a hitch.
Basically what you are doing is replacing the Tomcat cert on the server. Certs do expire at some point even if you are on a third party one.
I’m assuming you are on self signed now. As long as you are providing a cert that is fully trusted by your server and clients, it doesn’t matter which cert it is the trust will be there.
That is why you would choose a third party signed one that Tomcat and clients both trust. You are just adding an additional new unexpired cert to your existing key store.
You get to decide but you should be fine going third party signed. If you want to confirm, call jamf but you should be good.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-04-2019 09:01 AM
I'm in the same boat now and in the middle of device roll out.
If I want to proceed as is for now, can I select option 2: "Generate a certificate from the Jamf Pro's built-in CA" and address this properly when I have some downtime?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-09-2019 11:30 AM
We have an SSL through DigiCert that we are having issues renewing because of IP re-routing issue and new "SSL Police" rules.
We have a domain consolidation that we had to work with when we rebuilt our server and made sure we did not have to re-enroll all f our devices.
We are kinda stuck
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-08-2020 09:18 AM
@kdspatio , would love to see your recipe! I'd like to try LetsEncrypt before paying for a cert. Non-Profit, Edu here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-01-2020 01:55 AM
@kdspatio me too! We've deployed Lets Encrypt, but have some problems renewing it after 3 months...