http://www.vshare.com/iphone_en.html
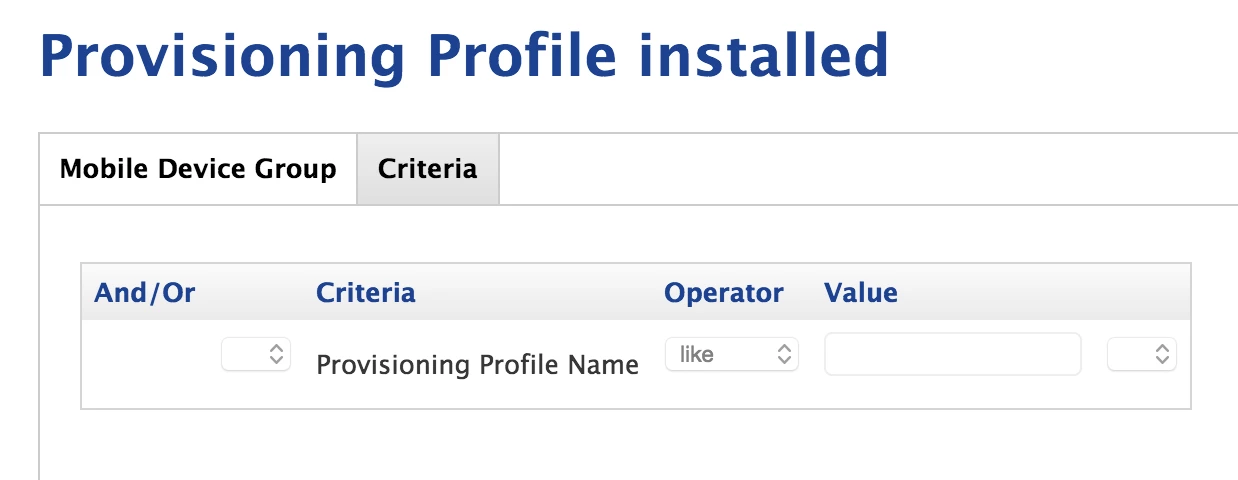
A new website has popped up that our students are using to install apps outside of the App Store. I think it's using a combination of profiles and web clips to do this, but I don't have access to a compromised iPad today to investigate more thoroughly.
Is anyone familiar with this?