- Jamf Nation Community
- Products
- Jamf Pro
- Re: vshare.com - App Installations that Circumvent...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-20-2014 09:17 AM
http://www.vshare.com/iphone_en.html
A new website has popped up that our students are using to install apps outside of the App Store. I think it's using a combination of profiles and web clips to do this, but I don't have access to a compromised iPad today to investigate more thoroughly.
Is anyone familiar with this?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-20-2014 10:26 AM
I'm doing a little looking into this, and it looks like it installs a few provisioning profiles as well as the vshare app (as far as I can tell its an app not a webclip). You can then download and install them through that app. I can confirm that blocking the following sites seem to prevent the vshare app from working:
*.vshare.com
*.appvv.com
*.umeng.com
Not too sure how to block the install of the provisioning profile though, or block the vshare app from installing in the first place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-20-2014 10:26 AM
I'm doing a little looking into this, and it looks like it installs a few provisioning profiles as well as the vshare app (as far as I can tell its an app not a webclip). You can then download and install them through that app. I can confirm that blocking the following sites seem to prevent the vshare app from working:
*.vshare.com
*.appvv.com
*.umeng.com
Not too sure how to block the install of the provisioning profile though, or block the vshare app from installing in the first place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-20-2014 01:39 PM
Swell, I'll block those with our content filter. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2014 01:09 PM
Has anyone confirmed if the Vshare icon is an app or a webclip? We are blocking apps that aren't in self-service and want to make sure that they have to download the app first to start this loophole?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2014 01:33 PM
The share is NOT a web clip, its an app, and it is not installed via the app store, from what I can tell it gets installed with a provisioning profile. I'm not very familiar with provisioning profiles or their capabilities but I was able to install the share app and apps from the vshare app store on a DEP supervised iPad with the app store completely disabled (both add and remove apps disabled). The best way to block it if your using DEP supervised iPads is to use the Content Filtering config profile and block the above URLS. That should prevent it from being installed no matter what network they're connected to.
-Justin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2014 01:47 PM
I too experienced this in my district. It is indeed an App that you can scope a smart group for if you would like to as well. The smart group is how we tracked down each student device that had installed the app and started installing unapproved apps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2014 07:17 AM
Witt, how are you blocking apps that are not in Self Service? That sounds like a fantastic option for some of our locked-down iPads.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2014 09:18 AM
We have found that this app is pretty much malware. I have students who get this app and subsequently see ads and unsolicited pop-ups injected into Safari on sites that are known to be ad free. It also adds a plugin to Firefox and Chrome to affect them. An example of this behavior are ads that would show up at the bottom of the normally blank Google search page.
A closer inspection found a launch daemon added to load the Vshare app in the background. Once you disable it, kill the Vshare process, and remove the plugin from Firefox and Chrome,the machine no longer presents with these symptoms.
Howard Griffith--Endpoint Systems Engineer--Eastern Washington University
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-30-2015 12:34 PM
@brandonusher What does your smartgroup criteria look like? Is it based on a profile or the app itself? We are just seeing this on campus and I'd like to stop it sooner than later. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-30-2015 12:45 PM
@davidwbeaty The Smart Group was just criteria of "App Name has vshare2.1.4 or App Name has vShare"
I didn't get the bundle identifier, but that would make it a bit more specific so the name can't change as easy. If you get the identifier (should be like com.vshare.iphone or w/e they use) then the criteria could be "App Identifier is com.vshare.iphone"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-30-2015 12:46 PM
We have a smartgroup that just lists iPads with Provisioning Profiles. I just add new ones as I come across them:
drinkdate <----that's the vShare profile
shanghsa
kutiemie
nanjin
szsc
HiP
EPHiPStore
EPHiPStoreZumDistrib
I have a solid dozen more that are just long numeric numbers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 12:05 AM
Thanks so much @brandonusher and @lehmanp00 for reviving this old thread to help me out! I am going to test both types of smartgroup (and going to take the plunge and install vShare on an iPad to see what is going on) I will post if there is anything to add to your criteria. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 05:22 AM
With iOS 9, I have implemented a new Restriction allowed by the MDM Framework, by unchecking 'Allow trusting new enterprise app authors'. They can still install vShare (and it installs its own Provisioning Profile) but they cannot install any of the cracked apps because I don't allow them to get the Trust prompt.
In addition, by trying to find these out in the wild myself, I have determined the following Provisioning Profile names:
profile shanghsa is installed with vShare app
profile guotai is installed with vShare app
profile EPHiPStore is installed with HiPStore app
profile HiP is installed with various apps, like Floppy Cloud and Remote Files
profile com.tence is installed with Shou app
profile 1020 is installed with nds4ios app
profile pggk is installed with PPSSPP app
profile GBA4IOS is installed with GBA4IOS app
profile ZFLDistribution is installed with GBA4IOS app (different site)
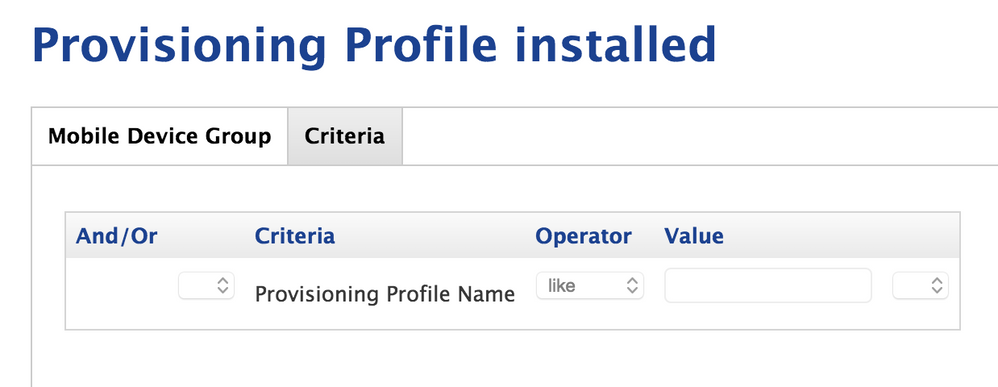
However, since there is no need for any of my students to have a Provisioning profile, my SG just reports on 'Provisioning Profile Name' LIKE "".
chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 05:50 AM
I didn't know we could put blank values in SG fields. That jumped my Prov. Profile SG up to 146 ipads.
Thanks cdenesha!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 08:59 AM
Out of curiosity, what are you doing once you identify iPads with "rogue" provisioning profiles? As I understand it, iOS is supposed to automatically manage them and as such, there is no interface to remove them. Restricting the installation of the profiles via the JSS only affects iOS 9+ and also will not remove any previously installed profiles before that policy was set. The profiles are also backed up in iCloud so the only way we've found to remove them is to wipe the device and set it up as a new iPad.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 09:28 AM
Install Xcode and you can remove the profiles that way.
Run Xcode, create a 'project'
Hook up the ipad, trust the computer
Look in the Window menu item in Xcode for a devices option
Select that iOS device
Right-click, show Provision Profiles
Highlight profile and remove.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 11:09 AM
I've seen very inconsistent results for deleting the app and having the associated Provisioning Profile go away as well.
We've implemented this just this year with grade 7 students, and this is their first year with an iPad, and they have been told up front not to do it.. so we just wipe and reset fresh, no iCloud Restore. Their homework should all be in Google Drive, and it emphasizes that we are not fooling around.
At my previous school I used Xcode like @lehmanp00 described.
chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 11:21 AM
@lehmanp00: Very interesting, I didn't know you could remove them via Xcode. I'll have to try it out.
@cdenesha: We're going on our 3rd year of iPads with this year being the middle school's all-grade rollout. We've asked/threatened/banned/pleaded but at the end of the day, we're still dealing with middle school students. :P
I'm not too familiar with how provisioning profiles work, aside from allowing the user to install non-App Store apps, what else can they do? Do they have the ability to push content to the device or manage settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-01-2015 12:42 PM
We have really good Administrative support for the program.
When you've written your own in-house (Enterprise) app that you want to deploy outside the App Store, you have to install your Provisioning Profile along with it. It is being abused out in the wild.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-24-2015 09:29 AM
Thanks for your suggestion about the Smartgroup that would sense provision profiles.
What criteria did you use to set this SG up exactly? I'm having trouble finding anything other than "Provision Profile Name". Unless that's the one.
If you could share how you have it configured - that would be much appreciated!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-28-2015 09:26 AM
@zsmith yes that is the one, and you leave the Value field blank.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2016 04:37 AM
Do you have any idea on vshare pro app. the latest version of vshare app. http://vshareprodownload.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2016 04:48 AM
Unchecking the "Allow trusting new enterprise app authors" restriction should put the kibosh on any of the rogue apps described here, providing the user is on iOS 9+
Unless I'm missing something, it looks like the "new" vShare is just a web clip. I don't think you can restrict creating new web clips short of blacklisting the original URL.