Zoom Exploit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
07-08-2019
10:59 PM
- last edited on
03-04-2025
07:14 AM
by
![]() kh-richa_mig
kh-richa_mig
For those of you who wake up to Zoom Exploit news.
You can set ZoomOpener.app as a Restricted Software.
Kill Process
Restrict to exact process name
Kill Process.
I would not recommend turning on Send Email or Message to the user.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-09-2019 02:14 PM
Patch tonight, July 9, 2019:
https://twitter.com/zoom_us/status/1148689995219099649
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-09-2019 03:25 PM
new version with patch released https://support.zoom.us/hc/en-us/articles/201361963-New-Updates-for-Mac-OS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-09-2019 03:34 PM
When will Jamf update Patch Management to include the latest version? How are you guys rolling out the new update?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-09-2019 05:14 PM
@stevewood Good catch, I mucked it up when I was generalizing it. I've corrected it above and thanked my lucky stars i only ran it on my testers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-09-2019 05:44 PM
@danny.gutman For a quick deploy, I used the Extension Attribute @sdagley put together (https://www.jamf.com/jamf-nation/discussions/32561/zoom-exploit#responseChild187183), forced an inventory update on all machines 1/computer at recurring check-in, created a Smart Group keyed to the Extension Attribute set to "Yes", then created a policy scoped to that Smart Group that deploys the latest Zoom version 1/day at recurring check-in and then updates the inventory. I could do 1/computer, but I figure this way if someone somehow installs an old version of Zoom on a machine somehow, the policy wouldn't catch it.
Only annoying part: the Zoom pkg I downloaded automatically opens the Zoom app upon completion of the install/update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-09-2019 05:48 PM
Zoom's extremely non-standard installer also autolaunches the app when it's done but you can expand the package, modify the preinstall script, and flatten the package back down. You'll need an installer signing cert of your own if you want to sign the package again.
pkgutil --expand /path/to/Zoom.pkg /path/to/expandedFolder
Comment out line 455 of the preinstall script and save the file
# open "$APP_PATH"&
pkgutil --flatten /path/to/expandedFolder /path/to/newPackageUnsigned.pkg
Optional:
productsign --sign 'Developer ID Installer: YOUR ID HERE' /path/to/newPackageUnsigned.pkg /path/to/newPackage.pkg- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 03:28 AM
For those of you struggling with setting the default preferences on your Zoom deployments, you will want to bookmark this page Zoom Mass Deployment with Preconfigured Settings There is a Windows version out there too if you're interested.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 04:02 AM
@brysontyrrell Any insights if Jamf's Patch Management team can expedite an update to the definition for Zoom?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 05:09 AM
@iJake I didn't see those lines in the latest version of the ZoomInstallerIT.pkg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 06:44 AM
After deploying the new package, ZoomOpener is still there and is still running. Not sure if I'm expected to remove and reinstall it, because that would just be running the same script we were all trying to get working yesterday...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 06:50 AM
@hdsreid some of my users told me the same thing. After quitting and relaunching the app it seems to have killed it for some. I'm still waiting for feedback from others.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 07:08 AM
@jwojda I think we might have Tesla to thank for that...
(line 350 from the ZoomInstallerIT postinstall script)
#ZOOM-34627 requirement from Tesla for not opening zoom.us.app{
#launch zoomus app
#exec "$2/Contents/MacOS/ZoomPresence"
#ZOOM-34627 requirement from Tesla for not opening zoom.us.app}- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 07:40 AM
Here's all the related files I've found so far, anyone have anything I might have missed?
/Applications/zoom.us.app
/Library/Preferences/us.zoom.config.plist
~/Library/Application Support/zoom.us/Data/zoomus.db
~/Library/Preferences/us.zoom.config.plist
~/Library/Preferences/us.zoom.xos.plist
~/Library/Preferences/us.zoom.xos.plist
~/Library/Preferences/us.zoom.ringcentral.plist
~/.ringcentralopener
~/.zoomus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 07:48 AM
Der Flounder to the rescue!
https://derflounder.wordpress.com/2019/07/10/zoom-vulnerability-and-remediation-script/#more-10415
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 08:49 AM
here is what we used and so far it's working
Kill Zoom Proccess
#!/bin/bash
procList=("zoom.us"
"zOutlookPluginAgent")
for proc in "${procList[@]}"; do
runningProc=$(ps axc | grep -i "$proc" | awk '{print $1}')
if [[ $runningProc ]]; then
echo "Found running process $proc with PID: ${runningProc}. Killing it..."
kill $runningProc
else
echo "$proc not found running..."
fi
doneRemove Zoom Script
#! /bin/bash
echo Cleaning Zoom...
echo Cleaning Application Cached Files...
sudo rm -rf ~/Library/Application Support/zoom.us
echo Cleaning Application...
{
sudo rm -rf /Applications/zoom.us.app
sudo rm -rf ~/Applications/zoom.us.app
sudo kextunload -b zoom.us.ZoomAudioDevice
sudo rm -rf /System/Library/Extensions/ZoomAudioDevice.kext
sudo rm -rf ~/.zoomus/ZoomOpener.app/Contents/MacOS/ZoomOpener
} &> /dev/null
echo Cleaning Outlook Plugin...
{
sudo rm -rf /Users/$USER/Library/Containers/com.microsoft.Outlook/Data/Documents/ZoomOutlookPlugin
sudo rm -rf /Library/ScriptingAdditions/zOLPluginInjection.osax
sudo rm -rf /Applications/ZoomOutlookPlugin
sudo rm -rf /Users/Shared/ZoomOutlookPlugin
sudo rm -rf /Library/LaunchAgents/us.zoom.pluginagent.plist
} &> /dev/null
echo Removed Application...and run this script from Install and Update Zoom Script.
The only thing i modify is turn off the auto full screen and dual monitor.
#!/bin/sh
#####################################################################################################
#
# ABOUT THIS PROGRAM
#
# NAME
# ZoomInstall.sh -- Installs or updates Zoom
#
# SYNOPSIS
# sudo ZoomInstall.sh
#
####################################################################################################
#
# HISTORY
#
# Version: 1.0
#
# - Shannon Johnson, 28.9.2018
# (Adapted from the FirefoxInstall.sh script by Joe Farage, 18.03.2015)
#
####################################################################################################
# Script to download and install Zoom.
# Only works on Intel systems.
#
# Set preferences - set to anything besides "true" to disable
hdvideo="true"
ssodefault="true"
ssohost="psu.zoom.us"
# choose language (en-US, fr, de)
lang=""
# CHECK TO SEE IF A VALUE WAS PASSED IN PARAMETER 1 AND, IF SO, ASSIGN TO "lang"
if [ "$4" != "" ] && [ "$lang" == "" ]; then
lang=$4
else
lang="en-US"
fi
pkgfile="ZoomInstallerIT.pkg"
plistfile="us.zoom.config.plist"
logfile="/Library/Logs/ZoomInstallScript.log"
# Are we running on Intel?
if [ '`/usr/bin/uname -p`'="i386" -o '`/usr/bin/uname -p`'="x86_64" ]; then
## Get OS version and adjust for use with the URL string
OSvers_URL=$( sw_vers -productVersion | sed 's/[.]/_/g' )
## Set the User Agent string for use with curl
userAgent="Mozilla/5.0 (Macintosh; Intel Mac OS X ${OSvers_URL}) AppleWebKit/535.6.2 (KHTML, like Gecko) Version/5.2 Safari/535.6.2"
# Get the latest version of Reader available from Zoom page.
latestver=`/usr/bin/curl -s -A "$userAgent" https://zoom.us/download | grep 'ZoomInstallerIT.pkg' | awk -F'/' '{print $3}'`
echo "Latest Version is: $latestver"
# Get the version number of the currently-installed Zoom, if any.
if [ -e "/Applications/zoom.us.app" ]; then
currentinstalledver=`/usr/bin/defaults read /Applications/zoom.us.app/Contents/Info CFBundleShortVersionString`
echo "Current installed version is: $currentinstalledver"
if [ ${latestver} = ${currentinstalledver} ]; then
echo "Zoom is current. Exiting"
exit 0
fi
else
currentinstalledver="none"
echo "Zoom is not installed"
fi
url="https://zoom.us/client/${latestver}/ZoomInstallerIT.pkg"
echo "Latest version of the URL is: $url"
echo "`date`: Download URL: $url" >> ${logfile}
# Compare the two versions, if they are different or Zoom is not present then download and install the new version.
if [ "${currentinstalledver}" != "${latestver}" ]; then
# Construct the plist file for preferences
echo "<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>nogoogle</key>
<string>1</string>
<key>nofacebook</key>
<string>1</string>
<key>ZDisableVideo</key>
<true/>
<key>ZAutoJoinVoip</key>
<true/>
<key>ZDualMonitorOn</key>
<false/>" >> /tmp/${plistfile}
if [ "${ssohost}" != "" ]; then
echo "
<key>ZAutoSSOLogin</key>
<true/>
<key>ZSSOHost</key>
<string>$ssohost</string>" >> /tmp/${plistfile}
fi
echo "<key>ZAutoFullScreenWhenViewShare</key>
<false/>
<key>ZAutoFitWhenViewShare</key>
<false/>" >> /tmp/${plistfile}
if [ "${hdvideo}" == "true" ]; then
echo "<key>ZUse720PByDefault</key>
<true/>" >> /tmp/${plistfile}
else
echo "<key>ZUse720PByDefault</key>
<false/>" >> /tmp/${plistfile}
fi
echo "<key>ZRemoteControlAllApp</key>
<true/>
</dict>
</plist>" >> /tmp/${plistfile}
# Download and install new version
/bin/echo "`date`: Current Zoom version: ${currentinstalledver}" >> ${logfile}
/bin/echo "`date`: Available Zoom version: ${latestver}" >> ${logfile}
/bin/echo "`date`: Downloading newer version." >> ${logfile}
/usr/bin/curl -L -o /tmp/${pkgfile} ${url}
/bin/echo "`date`: Installing PKG..." >> ${logfile}
/usr/sbin/installer -allowUntrusted -pkg /tmp/${pkgfile} -target /
/bin/sleep 10
/bin/echo "`date`: Deleting downloaded PKG." >> ${logfile}
/bin/rm /tmp/${pkgfile}
#double check to see if the new version got updated
newlyinstalledver=`/usr/bin/defaults read /Applications/zoom.us.app/Contents/Info CFBundleShortVersionString`
if [ "${latestver}" = "${newlyinstalledver}" ]; then
/bin/echo "`date`: SUCCESS: Zoom has been updated to version ${newlyinstalledver}" >> ${logfile}
# /Library/Application Support/JAMF/bin/jamfHelper.app/Contents/MacOS/jamfHelper -windowType hud -title "Zoom Installed" -description "Zoom has been updated." &
else
/bin/echo "`date`: ERROR: Zoom update unsuccessful, version remains at ${currentinstalledver}." >> ${logfile}
/bin/echo "--" >> ${logfile}
exit 1
fi
# If Zoom is up to date already, just log it and exit.
else
/bin/echo "`date`: Zoom is already up to date, running ${currentinstalledver}." >> ${logfile}
/bin/echo "--" >> ${logfile}
fi
else
/bin/echo "`date`: ERROR: This script is for Intel Macs only." >> ${logfile}
fi
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 09:20 AM
Thanks for the EA, @sdagley. I changed a line when found to report back the installed version:
#!/bin/bash
# https://www.jamf.com/jamf-nation/discussions/32561/zoom-exploit#responseChild187183
zoomFound="No"
for USER_HOME in /Users/*; do
USER_UID=$(basename "${USER_HOME}")
if [[ -d "${USER_HOME}/.zoomus/ZoomOpener.app" ]]; then
zoomFound="`/usr/bin/defaults read ${USER_HOME}/.zoomus/ZoomOpener.app/Contents/Info.plist CFBundleShortVersionString`"
fi
done
echo "<result>${zoomFound}</result>"
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 09:44 AM
@dan-snelson I am told a patch definition update for Zoom will be out shortly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 10:21 AM
@danny.gutman "When will Jamf update Patch Management to include the latest version? How are you guys rolling out the new update?"
Also wondering about this, do most of you just wait for patch definition updates? Is @adam.ashworth's workflow a good way to do this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 11:00 AM
@Garci4, honestly just wanted to roll it out already, can't wait for Jamf to update Patch Management.
I just created a smart group targeting all Macs not having the latest version, and scoped that to a policy that includes the latest ZoomITInstaller package. Worked fine for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 11:29 AM
Hey folks!
The zoom.us 4.4.53932.0709 update for Patch Management is now updated in the zoom.us Software Title.
Thanks!
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 11:33 AM
Has anyone tested deploying the new IT installer package over the old version? Does it disable the web server portion and clean up properly? Or are you deploying that update with a script to make sure that gets nuked properly?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 11:41 AM
@danny.gutman When you pushed out the new package, did it uninstall the previous version, removing all the components?
And did it transfer over and personalized settings the users may have?
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 11:43 AM
Begin forwarded message: From: Jamf Pro Beta Server noreply@churchofjesuschrist.org Subject: zoom.us v4.4.53932.0709 is available Date: July 10, 2019 at 12:27:44 PM MDT Updates for zoom.us are available. Title: zoom.us Version: 4.4.53932.0709 Publisher: Zoom Video Communications, Inc.
Thanks @brysontyrrell, et al.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 12:59 PM
@hdsreid @AVmcclint @Bret_P - in my testing today, the web opener is not removed if JAMF updates Zoom in the background with the program open, which is the usual install method in my environment.
After a relaunch, the new version is correct but the web opener is still there, and so still presumably vulnerable. This is the case even the user isn't signed in to Zoom but Zoom is running. Only after closing Zoom completely, did the installer remove the web opener when run via a JAMF policy.
I'm sure some will add a script to their Zoom update policy to force close the app, but the reason why that is not ideal is that, even more than just potentially forcing it closed during a meeting someone is attending, if the user is the meeting organizer, then the meeting is immediately ended for all attendees. Instead, we're using a version of Rich Trouton's script to first mitigate the issue everywhere, and only installing the update via policy after we verify with an extension attribute that the Web Opener doesn't exist in any profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 03:21 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-10-2019 03:38 PM
Zoom has done a new update with the patch, here you can have the new zoom version:
https://zoom.us/download
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 12:55 AM
Interesting…
https://techcrunch.com/2019/07/10/apple-silent-update-zoom-app/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 02:16 AM
How can we check, if this silent apple update was installed on the client? Does anybody know the correct version? (XProtect/Gatekeeper/MRTConfigData version)
(Most of our managed Macs receive their updates from our internal reposado Software Update server. Today I saw a new entry for MRTConfigData with version 1.45)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 03:24 AM
@hansjoerg.watzl to search if the latest update of MRTConfigData has been installed to Mac computers you can use Advanced Computer Searches with simple criteria Packages Installed By Installer.app/SWU and the value com.apple.pkg.MRTConfigData_10_14.16U4071
If you would like to get the correct version of MRTConfigData I suggest to use below command:
defaults read /System/Library/CoreServices/MRT.app/Contents/Info.plist CFBundleShortVersionStringThere is also a blog of @ClassicII which can help you to track the versions of macOS and Core Apps: macOS System Status & Version Info
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 04:05 AM
@lukasz.molenda Thanks, I had to enter the following defaults command to get the version:
defaults read /System/Library/CoreServices/MRT.app/Contents/Info.plist CFBundleShortVersionString
But it lists me only version 1.42 and not the current one (1.45).
I tried a manual software update in system preferences before and the log shows a new MRTConfigData version, but it seems, it was not installed.
tail /private/var/log/install.log
2019-07-11 11:29:49+02 UM00655 softwareupdate_notify_agent[1010]: AssertionMgr: Take com.apple.softwareupdate.NotifyAgentAssertion-BadgingCountChanged assertion with type BackgroundTask for pid 1010, id 0x85EB
2019-07-11 11:29:49+02 UM00655 softwareupdated[1012]: Scan (f=1, d=0) completed
2019-07-11 11:29:49+02 UM00655 softwareupdated[1012]: 1 updates found:
041-84505 | MRTConfigData 1.45
2019-07-11 11:29:49+02 UM00655 softwareupdated[1012]: Removing client SUUpdateServiceClient pid=7349, uid=0, installAuth=NO rights=(), transactions=0 (/usr/sbin/softwareupdate)
2019-07-11 11:29:49+02 UM00655 softwareupdate_notify_agent[1010]: SUAppStoreAgentNotifier: Setting badge count to 0:
2019-07-11 11:29:49+02 UM00655 softwareupdate_notify_agent[1010]: AssertionMgr: Cancel com.apple.softwareupdate.NotifyAgentAssertion-BadgingCountChanged assertion for pid 1010, id 0x85EB
2019-07-11 11:38:28+02 UM00655 installd[7506]: installd: Starting
2019-07-11 11:38:28+02 UM00655 installd[7506]: installd: uid=0, euid=0
2019-07-11 11:38:28+02 UM00655 system_installd[6921]: PackageKit: Install sandbox purging reclaimed 0 KB- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 04:53 AM
Might be a little raw but this would help to see the MRTConfigData from the install log for an extension attribute:
#!/bin/sh
result=$(grep 'MRTConfigData' /private/var/log/install.log | tail -1 | cut -f 3 | sed 's/ | MRTConfigData //')
echo "<result>$result</result>"
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 06:38 AM
edit: just saw @lukasz.molenda already posted this :)
also; from https://www.jamf.com/jamf-nation/feature-requests/5158/built-in-inventory-fields-for-os-x-macos-security-and-malware-protection-systems
defaults read /System/Library/CoreServices/MRT.app/Contents/version CFBundleShortVersionString
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 07:01 AM
so, created an extension attribute to monitor MRT version:
#!/bin/sh
SWU=`defaults read /System/Library/CoreServices/MRT.app/Contents/version CFBundleShortVersionString`
echo "<result>$SWU</result>"created an extension attribute to monitor for the hidden zoom install (thanks @sdagley :
#!/bin/sh
zoomFound="No"
for USER_HOME in /Users/*; do
USER_UID=$(basename "${USER_HOME}")
if [[ -d "${USER_HOME}/.zoomus/ZoomOpener.app" ]]; then
zoomFound="Yes"
fi
done
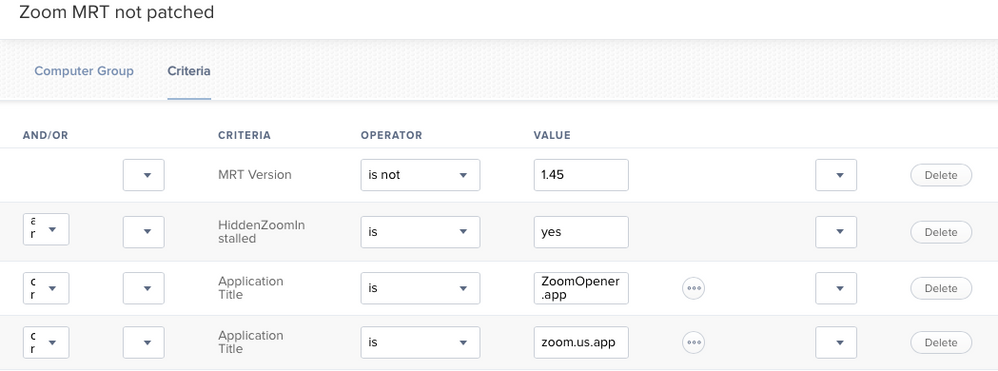
echo -e "<result>$zoomFound</result>"created a smart group to identified devices affected:
(edited to update smartgroup screenshot)
bobs your uncle?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 07:46 AM
@balexander667 The Value you'd want to use to indicate your HiddenZoomInstalled Extension Attribute found something is Yes (zoomFound is the variable used In the script, and it'll be either Yes or No)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 07:51 AM
@sdagley hah! duh, a lot of copying and pasting this morning :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 08:21 AM
@hansjoerg.watzl try the following command to force MRT
softwareupdate -ia --include-config-data
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 08:45 AM
@andrew.nicholas tnx, this did it!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 09:21 AM
Hello not sure if anyone saw this but Apple actually is removing the web server via silent update. Actually it is done through XProtect.
https://www.macrumors.com/2019/07/10/apple-update-remove-zoom-server/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 10:17 AM
@kmathern they deployed an update to MRT (malware removal tool). If a machine has ver. 1.45 of MRT, it is patched to prevent the web server issue. My machine received the update at 9:03am est today automatically pushed and silently from apple.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-11-2019 11:36 AM
Hey Guys, I put together a quick post to show you how to manually download only the MRTConfigData v1.45 update AND manually run it using the MRT Binary.
https://mrmacintosh.com/how-to-remediate-the-zoom-vulnerability-with-apple-malware-removal-tool/