- Jamf Nation Community
- Products
- Jamf Protect
- Re: Faster re-install of Jamf Protect?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-29-2022 01:40 PM
We'll soon be deploying Jamf Protect to our endpoints and are using the built-in integration between Jamf Protect and Jamf Pro to do the initial PKG and config profile installs.
In our environment, most users are admins on their machines and one thing we discovered during testing was that someone could easily throw away the Jamf Protect app and be unprotected. To remedy this, we've created an EA that tracks the installed version of the Jamf Protect binary (or returns "Protect binary not found") and populates a smart group if the binary isn't present. A policy then re-installs Jamf Protect on any computer in that smart group.
The one downside we've noted to this approach is that the EA only gets updated once daily on inventory collection, so it's possible for a computer to go up to 24 hours without Jamf Protect. Any ideas on how to accelerate the re-install in this situation?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 03:03 PM - edited 07-01-2022 01:41 PM
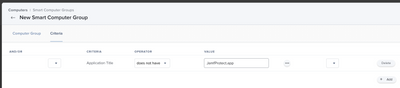
Create a Smart Computer Group targeting computers that do not have Jamf Protect installed. Scope your re-install policy to that. This is predicated upon last inventory update results.
Home Grown Solution (If Jamf Inventory Update isn't consistent or if you have an issue with what above smart group is reporting)
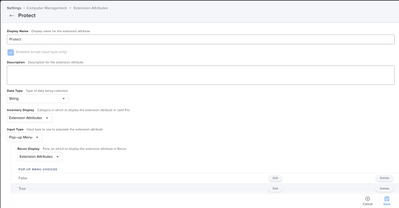
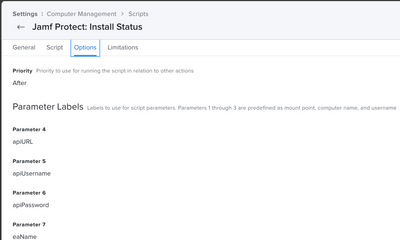
Step 1. Create an Extension Attribute Exactly as it is Depicted Below.
Display Name "Protect", Data Type "String", Inventory Display (Wherever you Want), Input Type "Pop-up Menu", Recon Display (Whatever you want), Pop-up Menu Choices "True" & "False".
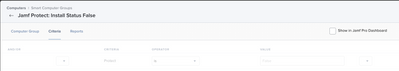
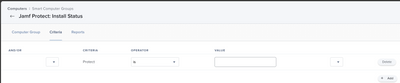
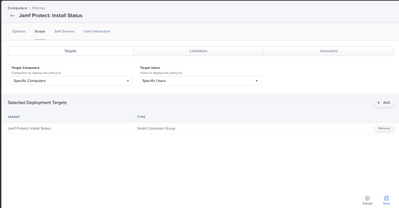
Step 2. Create two Smart Computer Groups Exactly as Depicted Below.
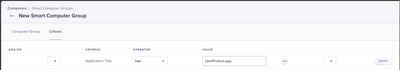
Smart Computer Group 1: Criteria: "Protect" (The Extension Attribute you just made), Operator "is", Value "False"
Smart Computer Group 2: Criteria: "Protect" (The Extension Attribute you just made), Operator "is", Value " " (EMPTY)
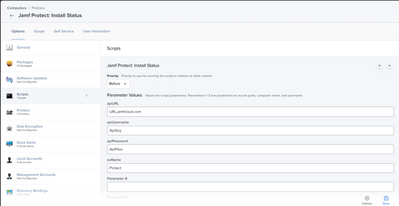
Step 3. Add the Following Script to your Jamf Pro Scripts Library & Modify the Parameter Values as Depicted Below.
This Script Runs a Check to see if the JamfProtect.app file exists, if it does, it writes True to the Extension attribute & is not included in the Smart Computer Group. If the JamfProtect.app file does not exist, it writes False to the Extension attribute & places the computer without Jamf Protect into the Smart Computer Group.
Script:
#!/bin/bash
# ██████╗ ██████╗ ██████╗██╗ ██╗███████╗████████╗███╗ ███╗ █████╗ ███╗ ██╗
# ██╔══██╗██╔═══██╗██╔════╝██║ ██╔╝██╔════╝╚══██╔══╝████╗ ████║██╔══██╗████╗ ██║
# ██████╔╝██║ ██║██║ █████╔╝ █████╗ ██║ ██╔████╔██║███████║██╔██╗ ██║
# ██╔══██╗██║ ██║██║ ██╔═██╗ ██╔══╝ ██║ ██║╚██╔╝██║██╔══██║██║╚██╗██║
# ██║ ██║╚██████╔╝╚██████╗██║ ██╗███████╗ ██║ ██║ ╚═╝ ██║██║ ██║██║ ╚████║
# ╚═╝ ╚═╝ ╚═════╝ ╚═════╝╚═╝ ╚═╝╚══════╝ ╚═╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝ ╚═══╝
# Created by Hugonaut
# Script Parameters are set within the Policy this Script is Assigned to & are to be configured as follows
# Parameter 4: jss.example.org:8443·································(apiURL)
# Parameter 5: API Administrator Account····························(apiUsername)
# Parameter 6: API Administrator Password···························(apiPassword)
# Parameter 7: Display Name of Extension Attribute ·················(eaName)
########################## Jamf Policy -> Script Parameters ############################
apiURL=$4
apiUsername=$5
apiPassword=$6
eaName=$7
###################################### Get UDID ########################################
computerUDID=$(/usr/sbin/system_profiler SPHardwareDataType | /usr/bin/awk '/Hardware UUID:/ { print $3 }')
############################### Get Jamf Protect Value #################################
JamfProtectValue=$(if [ -e "/Applications/JamfProtect.app" ]
then
echo "True"
else
echo "False"
fi)
########################### Construct & Post Jamf Group EA #############################
apiData="<computer><extension_attributes><extension_attribute><name>${eaName}</name><value>${JamfProtectValue}</value></extension_attribute></extension_attributes></computer>"
apiPost=`curl -H "Content-Type: text/xml" -sfu ${apiUsername}:${apiPassword} ${apiURL}/JSSResource/computers/udid/${computerUDID} -d "${apiData}" -X PUT`
Parameter Values:
Step 4:
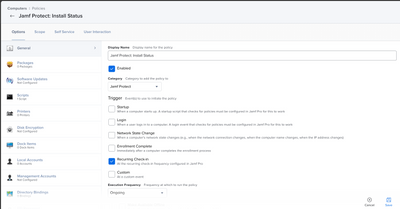
- Create a Policy with a Trigger of Recurring Check-in, an Execution Frequency of Ongoing.
- Add the script from Step 3 to the script payload of the policy, add your Jamf Pro Console URL, an administrator account or api account with access to your jamf pro console, the accounts password, and the name of the Extension Attribute created earlier.
- Scope to Smart Computer Group 2 (Empty Value) created in Step 2.
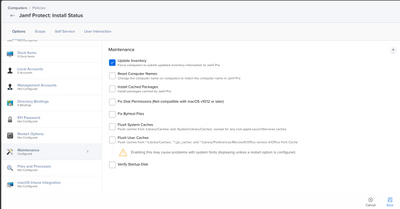
- Configure the "Maintenance" payload & Check Update Inventory.
For parameter "apiURL" - include https:// so it reads just "https://yourorg.jamfcloud.com"
What this will do is run that script on all computers with the empty field & determine if it is Installed or Not. Flagging it either True or False & removing it from scope for the policy. You'll end up with the Smart Computer Group 1 (false value group) - consisting of all the computers in your environment without Jamf Protect (in 15 Minutes, a lot less time than 24 hours.) You can also run this against computers that have reported Jamf Protect is installed as depicted below to doubly verify that its still installed / constant 15 minute monitoring.
Step 5: Add smart Computer Group 1 (False Value Group) to the scope of the policy you created that installs Jamf Protect & it will target those computers every recurring check-in instead of daily inventory record update.
Looking for a Jamf Managed Service Provider? Look no further than Rocketman
________________
Virtual MacAdmins Monthly Meetup - First Friday, Every Month
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2022 03:03 PM - edited 07-01-2022 01:41 PM
Create a Smart Computer Group targeting computers that do not have Jamf Protect installed. Scope your re-install policy to that. This is predicated upon last inventory update results.
Home Grown Solution (If Jamf Inventory Update isn't consistent or if you have an issue with what above smart group is reporting)
Step 1. Create an Extension Attribute Exactly as it is Depicted Below.
Display Name "Protect", Data Type "String", Inventory Display (Wherever you Want), Input Type "Pop-up Menu", Recon Display (Whatever you want), Pop-up Menu Choices "True" & "False".
Step 2. Create two Smart Computer Groups Exactly as Depicted Below.
Smart Computer Group 1: Criteria: "Protect" (The Extension Attribute you just made), Operator "is", Value "False"
Smart Computer Group 2: Criteria: "Protect" (The Extension Attribute you just made), Operator "is", Value " " (EMPTY)
Step 3. Add the Following Script to your Jamf Pro Scripts Library & Modify the Parameter Values as Depicted Below.
This Script Runs a Check to see if the JamfProtect.app file exists, if it does, it writes True to the Extension attribute & is not included in the Smart Computer Group. If the JamfProtect.app file does not exist, it writes False to the Extension attribute & places the computer without Jamf Protect into the Smart Computer Group.
Script:
#!/bin/bash
# ██████╗ ██████╗ ██████╗██╗ ██╗███████╗████████╗███╗ ███╗ █████╗ ███╗ ██╗
# ██╔══██╗██╔═══██╗██╔════╝██║ ██╔╝██╔════╝╚══██╔══╝████╗ ████║██╔══██╗████╗ ██║
# ██████╔╝██║ ██║██║ █████╔╝ █████╗ ██║ ██╔████╔██║███████║██╔██╗ ██║
# ██╔══██╗██║ ██║██║ ██╔═██╗ ██╔══╝ ██║ ██║╚██╔╝██║██╔══██║██║╚██╗██║
# ██║ ██║╚██████╔╝╚██████╗██║ ██╗███████╗ ██║ ██║ ╚═╝ ██║██║ ██║██║ ╚████║
# ╚═╝ ╚═╝ ╚═════╝ ╚═════╝╚═╝ ╚═╝╚══════╝ ╚═╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝ ╚═══╝
# Created by Hugonaut
# Script Parameters are set within the Policy this Script is Assigned to & are to be configured as follows
# Parameter 4: jss.example.org:8443·································(apiURL)
# Parameter 5: API Administrator Account····························(apiUsername)
# Parameter 6: API Administrator Password···························(apiPassword)
# Parameter 7: Display Name of Extension Attribute ·················(eaName)
########################## Jamf Policy -> Script Parameters ############################
apiURL=$4
apiUsername=$5
apiPassword=$6
eaName=$7
###################################### Get UDID ########################################
computerUDID=$(/usr/sbin/system_profiler SPHardwareDataType | /usr/bin/awk '/Hardware UUID:/ { print $3 }')
############################### Get Jamf Protect Value #################################
JamfProtectValue=$(if [ -e "/Applications/JamfProtect.app" ]
then
echo "True"
else
echo "False"
fi)
########################### Construct & Post Jamf Group EA #############################
apiData="<computer><extension_attributes><extension_attribute><name>${eaName}</name><value>${JamfProtectValue}</value></extension_attribute></extension_attributes></computer>"
apiPost=`curl -H "Content-Type: text/xml" -sfu ${apiUsername}:${apiPassword} ${apiURL}/JSSResource/computers/udid/${computerUDID} -d "${apiData}" -X PUT`
Parameter Values:
Step 4:
- Create a Policy with a Trigger of Recurring Check-in, an Execution Frequency of Ongoing.
- Add the script from Step 3 to the script payload of the policy, add your Jamf Pro Console URL, an administrator account or api account with access to your jamf pro console, the accounts password, and the name of the Extension Attribute created earlier.
- Scope to Smart Computer Group 2 (Empty Value) created in Step 2.
- Configure the "Maintenance" payload & Check Update Inventory.
For parameter "apiURL" - include https:// so it reads just "https://yourorg.jamfcloud.com"
What this will do is run that script on all computers with the empty field & determine if it is Installed or Not. Flagging it either True or False & removing it from scope for the policy. You'll end up with the Smart Computer Group 1 (false value group) - consisting of all the computers in your environment without Jamf Protect (in 15 Minutes, a lot less time than 24 hours.) You can also run this against computers that have reported Jamf Protect is installed as depicted below to doubly verify that its still installed / constant 15 minute monitoring.
Step 5: Add smart Computer Group 1 (False Value Group) to the scope of the policy you created that installs Jamf Protect & it will target those computers every recurring check-in instead of daily inventory record update.
Looking for a Jamf Managed Service Provider? Look no further than Rocketman
________________
Virtual MacAdmins Monthly Meetup - First Friday, Every Month
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-05-2022 07:28 AM
Thanks @Hugonaut! This will work nicely.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2022 08:20 AM
You're very welcome @dm8v - Happy to help!
Looking for a Jamf Managed Service Provider? Look no further than Rocketman
________________
Virtual MacAdmins Monthly Meetup - First Friday, Every Month
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-27-2022 01:50 PM
wow this is incredibly helpful, thanks mate