- Jamf Nation Community
- Products
- Jamf Pro
- Re: AD Conntection (WiFi) befor Login
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2016 08:21 AM
Hello Jamf-Community,
Since a few days, we are use Casper Suite. We are useing a Active Directory but we have a problem with the AD Connection at the Login.
How I can conntect to the WiFi in the Login Screen? At the moment we need a Ethernet Connection to get all Policies. If the Macbook is not connected by Ethernet, he use the Mobile Account and after the login he connected to the Wifi. Befor we can start the enroll we need to fix this issue, that we get a Wifi Connection on the Login Screen. We use a WPA2 Enterprise Wifi, it is connected to our AD for a easy login.
Maybe everyone can help me to fix this issue?
Many Thanks
Christian
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2016 05:24 AM
We have custom solution at our shop in order to achieve something close to Windows machine authentication, rather than user authentication to ensure our computers are connected to our network at the login window.
This involves installing a DMG in a known location which contains a configuration profile which has our certs and an account with the username TESTUSER and the password TESTPASS. After install we have a script generate a random password (security find-generic-password), replace the TESTUSER with the computername from AD (dsconfigad) and TESTPASS with the randomly generated password, and then installs the profile. We've used this since 2014 with success.
If this sounds like something you'd be interested in @c.knipping let me know and I'll post it here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2016 08:42 AM
@c.knipping
its in the network payload but you have to scope it to the computer level.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2016 08:44 AM
@c.knipping hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-29-2016 06:58 PM
We used certificate based authentication for wireless and have no issues. We can login with our AD credentials and everything runs as if it was wired.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-30-2016 04:46 AM
We used certificate based authentication for wireless and have no issues. We can login with our AD credentials and everything runs as if it was wired.
Many Thanks, I try this option! If it work I send a Feedback next days.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-30-2016 10:40 AM
We've done this quite a few times for our customers. In every case there has been a different challenge. Certificate templates and permissions, incompatibilities with the authentication server etc.
The basic setup will require a profile to get an AD certificate and deploy a wireless profile using the certificate for authentication.
Ideally you'll get some input from the person looking after the CA server and the person looking after the wireless network and RADIUS service as there is often a bit of troubleshooting involved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-01-2016 05:48 PM
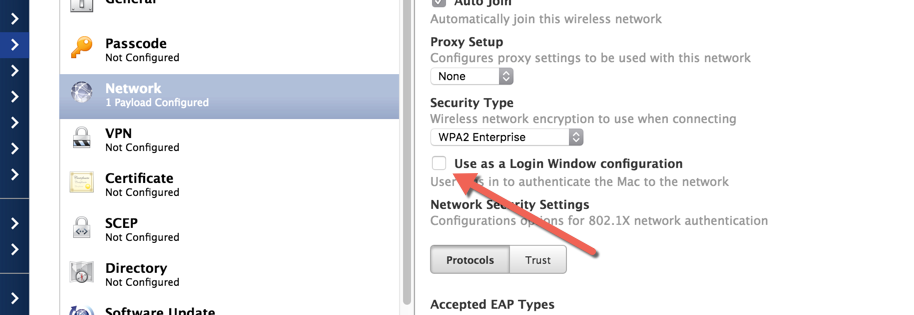
We have just been through this and solved this by having our CA certificate for our RADIUS on the profile and ticking the use login window configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2016 05:24 AM
We have custom solution at our shop in order to achieve something close to Windows machine authentication, rather than user authentication to ensure our computers are connected to our network at the login window.
This involves installing a DMG in a known location which contains a configuration profile which has our certs and an account with the username TESTUSER and the password TESTPASS. After install we have a script generate a random password (security find-generic-password), replace the TESTUSER with the computername from AD (dsconfigad) and TESTPASS with the randomly generated password, and then installs the profile. We've used this since 2014 with success.
If this sounds like something you'd be interested in @c.knipping let me know and I'll post it here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2016 08:37 AM
Yes, I would be interested in you posting your solution. Many thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2016 08:46 AM
@aporlebeke I'd be interested as well. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2016 09:15 AM
Below is the script we use. This is something my shop came up with and has worked successfully. Rarely, we'll have an issue where for whatever reason it doesn't properly enter the computer AD hostname and randomly generated password in the configuration profile, but we have a policy setup in Self Service so that we can run a script to uninstall the profile and remove the dmg, and then reinstalls the DMG and reruns the script. Again, happens VERY rarely but something we've developed a quick fix for.
I did not personally create the script OR the config profile. There are tools out there such that you could create a config profile that contains the certs and other information computers in your environment need to connect to Wifi. The script below requires TESTUSER and TESTPASS to be the entered username/password in the config profile.
#!/bin/bash
#####
# OSX Machine auth for 802.1x profile
# get AD machine user/pass and put into 802.1x profile template
# install the profile
#
# sed has it's own uses for '&' and '' in replacements
# and the randomly generated password sometimes has them
# So, trap and escape them before feeding into sed
#
# put the host name in 'host/computer name.YOURDOMAIN.com' format
##
# Originally by Dan P ~2012
# added traps and host name modification
# thp 7/16/14
#####
PASS=`sudo /usr/bin/security find-generic-password -s "/Active Directory/YOURDOMAIN" -w /Library/Keychains/System.keychain`
USER=`/usr/sbin/dsconfigad -show | awk '/Computer *Account/ { print $4 }'`
# trap '' and escape them
if [[ ${PASS} =~ '' ]]; then
PASS=$(echo "$PASS" | sed 's/\/\\/g')
fi
# trap '&' and escape them
if [[ ${PASS} =~ '&' ]]; then
PASS=$(echo "$PASS" | sed 's/&/\&/g')
fi
# format username as host name
USER=`echo $USER | tr -d '$'`
USER="host/${USER}.YOURDOMAIN.com"
# change template file
PROPATH='/path/to/config/profile/template'
PROFILE='name_of_config_profile.mobileconfig'
sed -i .bak 's/TESTPASS/'${PASS}'/' ${PROPATH}/${PROFILE}
sed -i .bak 's/TESTUSER/'${USER}'/' ${PROPATH}/${PROFILE}
/usr/bin/profiles -I -F ${PROPATH}/${PROFILE}
rm -f ${PROPATH}/${PROFILE}.bak
exitFix script that uninstalls profile and deletes the config template file. You'll need the profileIdentifier of the config profile that you want to delete:
#!/bin/bash
# Uninstalls faculty machine auth profile based on its profileIdentifier
sudo -u root profiles -R -p name.of.configprofile.profileIdentifier
# Deletes previously installed faculty machine auth profile
sudo rm -rf /path/to/config/profile/template/name_of_config_profile.mobileconfig
exit