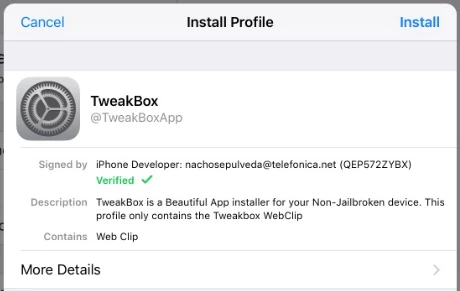
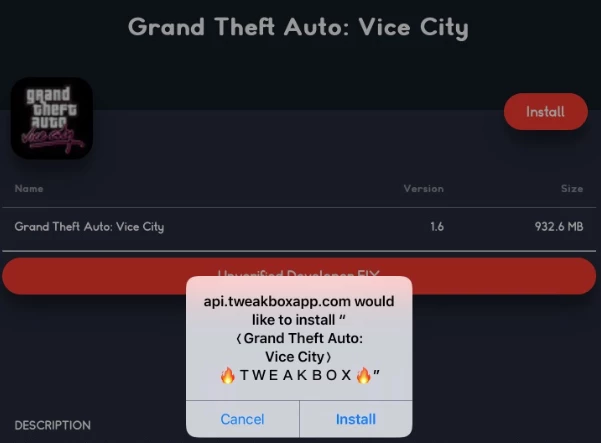
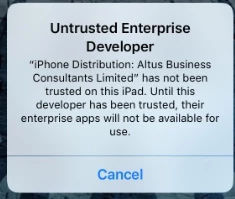
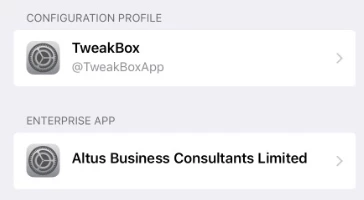
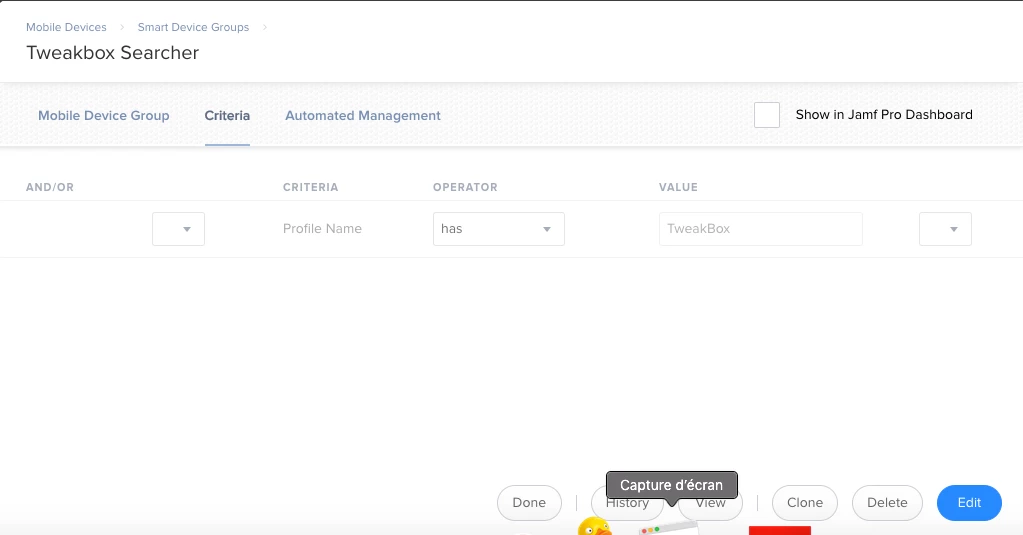
I learned today that one of my students has found an "awesome" new tool — TweakBox (https://www.tweakboxapp.com) — that allows him to bypass JAMF Pro blocking the App Store on our iPads. While my Smart group identifying student iPads with unauthorized apps worked like a charm, I not looking forward to having to be constantly vigilant about other students using this tool. Has anyone else run into it? Any good ideas about how to stop it?
The things that have crossed my mind so far are the following (and none of them are all that appealing):
- one I could disallow the ability to install profiles (since TweakBox installs a profile), but I think that would also prevent me from adding or adjusting any profiles on the student iPads unless I pull them all in and turn off that profile setting manually.
- two I could use the app restrictions setting to white list the only acceptable apps on the student iPads. Unfortunately, that would radically change the culture of our school where we currently make well over 100 apps available to the students beyond the core 25 that install automatically.
- three I could see if it would work to blacklist TweakBox's site, but I am not confident about that. Anyone who has an "app store" full of hacked apps is going to have innumerable proxy addresses allowing access to its content
Anyway, I would love to hear any ideas and suggestions. And, if you have also encountered this fun little "tool," I would love to know what you are doing about it.
Thank you!