- Jamf Nation Community
- Products
- Jamf Pro
- Re: Anyone else dealing with TweakBox?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Anyone else dealing with TweakBox?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
09-18-2017
02:41 PM
- last edited on
03-04-2025
02:42 AM
by
![]() kh-richa_mig
kh-richa_mig
I learned today that one of my students has found an "awesome" new tool — TweakBox (https://www.tweakboxapp.com) — that allows him to bypass JAMF Pro blocking the App Store on our iPads. While my Smart group identifying student iPads with unauthorized apps worked like a charm, I not looking forward to having to be constantly vigilant about other students using this tool. Has anyone else run into it? Any good ideas about how to stop it?
The things that have crossed my mind so far are the following (and none of them are all that appealing):
- one I could disallow the ability to install profiles (since TweakBox installs a profile), but I think that would also prevent me from adding or adjusting any profiles on the student iPads unless I pull them all in and turn off that profile setting manually.
- two I could use the app restrictions setting to white list the only acceptable apps on the student iPads. Unfortunately, that would radically change the culture of our school where we currently make well over 100 apps available to the students beyond the core 25 that install automatically.
- three I could see if it would work to blacklist TweakBox's site, but I am not confident about that. Anyone who has an "app store" full of hacked apps is going to have innumerable proxy addresses allowing access to its content
Anyway, I would love to hear any ideas and suggestions. And, if you have also encountered this fun little "tool," I would love to know what you are doing about it.
Thank you!
- Labels:
-
Configuration Profiles
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-20-2017 07:14 AM
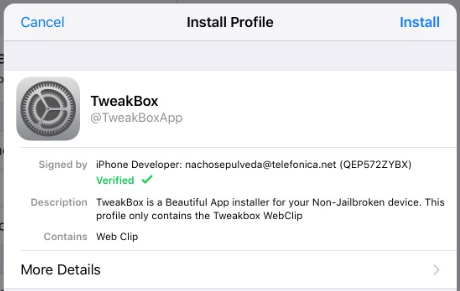
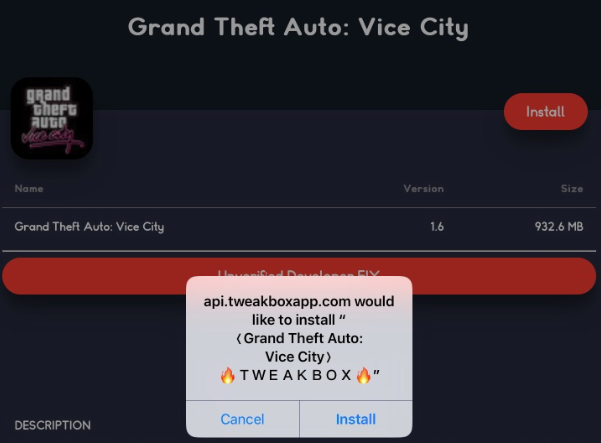
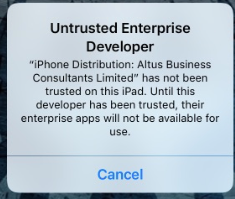
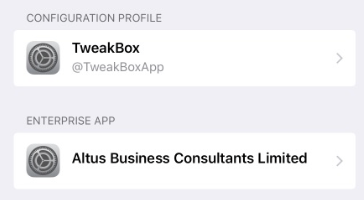
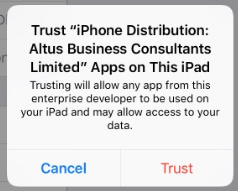
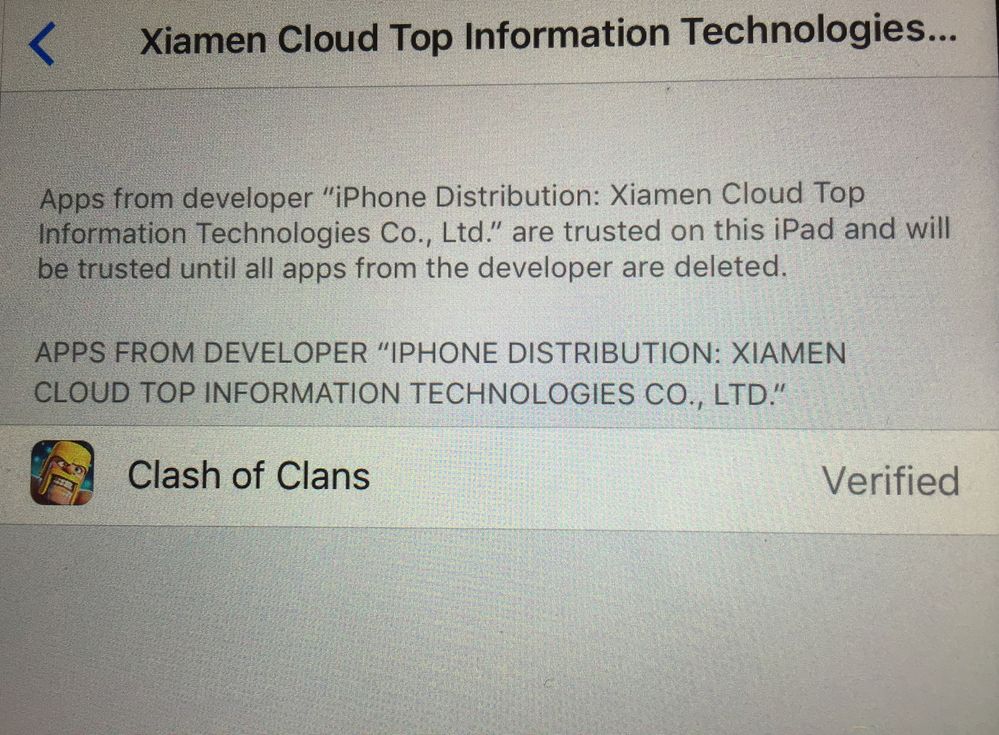
We just stumbled across this today. After initially installing the profile it gives you a web clip. The web clip allows you to browse their "app store" which consists of modified/hacked versions of real apps, which are then pushed to your device as "enterprise apps" by enterprise developers. You must then go in and "trust" the developer in order to be able to launch the app. The JSS picks up both the config profile and the installed app in inventory, which is nice. Is there a way in JSS to prevent users from trusting enterprise developers, or to setup a whitelist/blacklist?
Initial config profile installation prompt:
App install prompt:
Untrusted developer warning:
Installed config profile:
Enterprise developer name:
Developer trust prompt:
Installed app in JSS inventory:
Installed config profile in JSS inventory:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-27-2017 01:04 PM
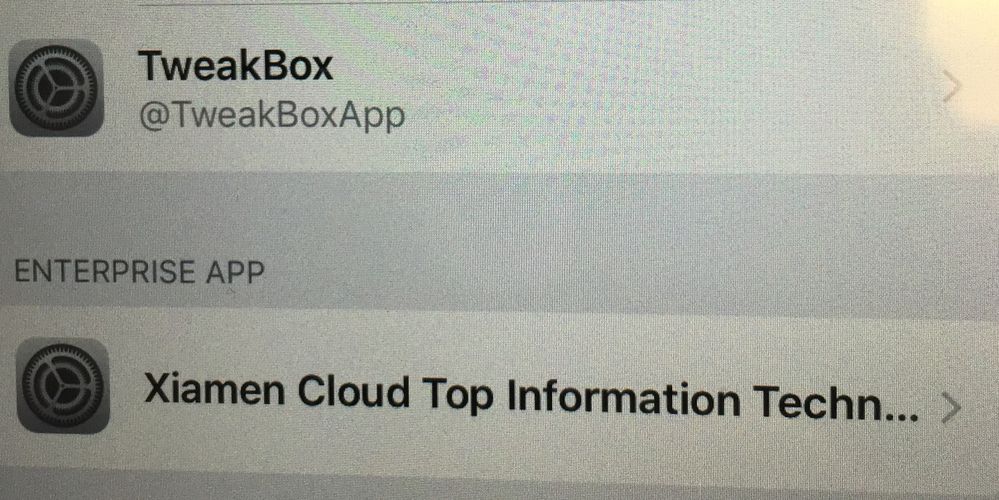
Funny, the ones I just located have an enterprise app with Xiamen Cloud Top Information Technologies Co., LTD--which sounds totally legit. The kids can remove the TweakBox profile but can't remove any of the apps they've verified. It helps me track them down, but I was wondering if there was any way I can search for that particular "Enterprise App"?
I'm sure the kids have installed a boatload of apps, and I can search for the main culprits, as well as the TweakBox profile. I've blocked it in our content filter for all student accounts, but I'm curious if I can search for the developer and catch the ones that install/remove the TweakBox profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-02-2017 06:38 AM
We had a similar issue last week as we deployed iPads for the first time to our HS students. We found that if we turned off "Allow trusting New Enterprise App Authors" in the restrictions, it removed the option in settings for them to trust the app. We even had a student in an administrators office say the next day "we used to be able to click trust in settings but now it's not there anymore".
The only issue would be if you wanted to push out an in house app, I don't know if it would allow it, but we don't have a need for that right now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-28-2018 11:00 AM
At our school board, we have that problem too.
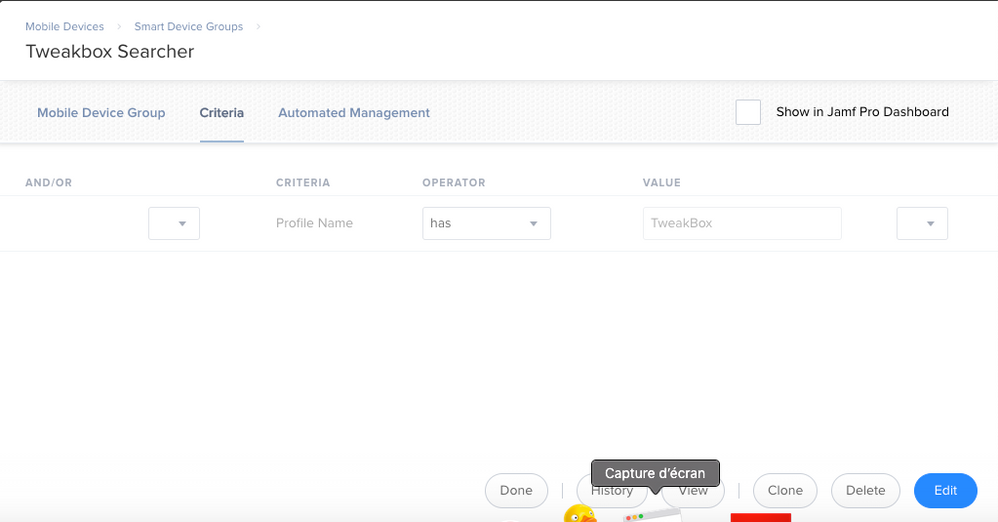
To find them over 5000 ipads, i made a SmartGroup with the following criteria:
Lucky for us, only 30 were detected. Some of them are in the list but are not validated with the jailbrake.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-28-2018 12:36 PM
When this started showing up in my school district, I blocked the ability to install Profiles which worked for about a year until another work around was created. I then created a smart group that sent an email notification when when an unauthorized profile was installed. Next step involved looking at the inventory on the iPad so I could create smart groups for the apps that were installed. If no app was installed (web clips), I would alert the network admin so that we could block the sites in our firewall. The iPads were then locked with a screen message telling the student that they were in violation of the district's technology agreement, and to visit the tech office. Since this is a behavior issue, administration was also alerted.
Making a big deal out of these types of hacks was quite successful as last school year I saw less than five iPads that were hacked.
I loved the challenge of dealing with students who were able to circumvent our management. Even though it was fun to crush their hopes and dreams, I would encourage these students to get involved in STEM classes and continue to try and hack the iPads.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-02-2018 09:01 PM
Blocking testing enterprise app authors and installing configuration profiles is how I blocked this on a test iPad.
@tomhastings The smart group you are using, does it detect all other configuration profiles NOT named “MDM Profile”? It is nice to identify just one, but there are many of these services out there.
Thanks