- Jamf Nation Community
- Products
- Jamf Pro
- Re: Approving Pulse Secure 9.1.9 System Extension
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Approving Pulse Secure 9.1.9 System Extension
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-16-2020 07:37 PM
We have deployed Pulse Secure 9.1.9 into production and my macOS 10.15.x Catalina Macs are now prompting users to...
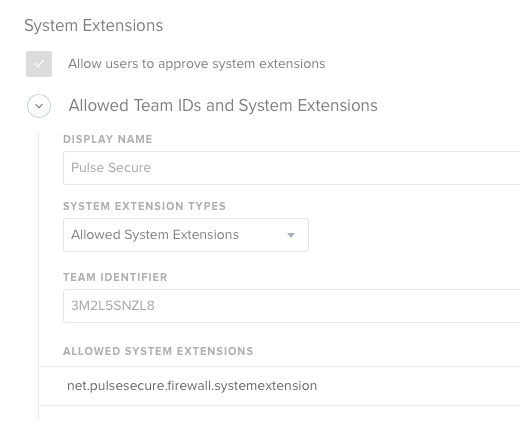
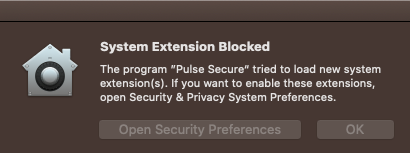
1 Approve the System Extension in System Prefs Security & Privacy Pane (this pop-up is similar to older Kernel Extensions).
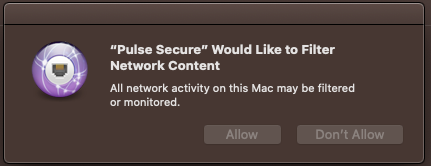
2 Approve "Filter Network Content" (this is a new pop-up warning).
These warnings tend to scare my users and the users usually click the wrong buttons (or ignore the messages).
To proactively mitigate this issue, I have created a Jamf MDM profile with a System Extension Approval payload. However, my Catalina users are still getting the pop-up warnings when Pulse Secure 9.1.9 is launched for the first time. I assume the same issue will apply for Big Sur too (Which I don't have in production yet but I see similar behavior in my test environment).
In some cases, the System Extension appears to be approved, but the second "Filter Network Content" warning is not approved.
I have read all the applicable Pulse Secure support KBs on this matter. I think I'm doing this correctly.
Is anyone else wrestling with this issue in Catalina (or Big Sur)?
(See attached screenshots).
- Labels:
-
Configuration Profiles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 01:39 AM
What does sudo systemextensionsctl list output before you manually approve it?
The first warning is a web content filter approval. Currently Jamf Pro does not have a config profile payload for this yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 01:49 AM
We have the same issue.
Pulse told me that the "filter network content" is an option for Big Sur, and can be turned off via Mdm (Jamf), but I can't find it
Sometimes this pop up comes back every second, very annoying
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 07:08 AM
BTW: These Pulse Secure docs outline the behavior and expectations of 9.1.9 and system extensions.
https://kb.pulsesecure.net/articles/Pulse_Secure_Article/KB44631/?kA13Z000000fzPf
https://kb.pulsesecure.net/articles/Pulse_Secure_Article/KB44592
https://kb.pulsesecure.net/articles/Pulse_Secure_Article/KB44608/?kA13Z000000fzNj
"...Pulse uses the 'Content-filter-provider' entitlement to filter the traffic. The 'Content Filtering' notification will only show once. Pulse cannot avoid / bypass the 'Content Filtering' prompt. However, customers can whitelist the Pulse Secure system extension. To whitelist the Pulse Secure extension, see the Pulse Secure TeamID and bundle ID using systemextensionsctl list. This can be done on any MDM provider; Jamf being one of them."
My biggest question is: What if an end-user clicks "Don't Allow" - How does IT troubleshoot and revert this setting? Where does it live? Are there CLI tools to remediate this setting?
Apples docs dont mention any local CLI/GUI tools to manually revert via script etc (see https://support.apple.com/guide/mdm/web-content-filter-payload-settings-mdmc77c9609/web)
Can a content filter profile be built manually outside of Jamf (i.e.; Apple Configurator etc)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-17-2020 07:10 AM
admin1@test ~ % systemextensionsctl list
1 extension(s)
--- com.apple.system_extension.network_extension
enabled active teamID bundleID (version) name [state]
* * 3M2L5SNZL8 net.pulsesecure.firewall.systemextension (1.0/1) PulseSecureFirewallSysExt [activated enabled](I forgot to add this to my original post sorry)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-02-2020 03:08 AM
Hey,
I've been encountering similar issues with Pulse Secure 9.1.8r2 and 9.1.9 on Catalina with the additional popups even if the system extension profile is on place. Even the attempts to make the web content filter suppressed has caused issues.
I had two mobileconfig files via #Pulsesecure discussion to try out (Without signing and signed) but ended up having more issues with the application i.e. not being able to connect to the VPN points at all. The issue appeared both on Catalina and Big Sur.
I have open case with Pulse Case to follow this at the moment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-04-2020 10:55 AM
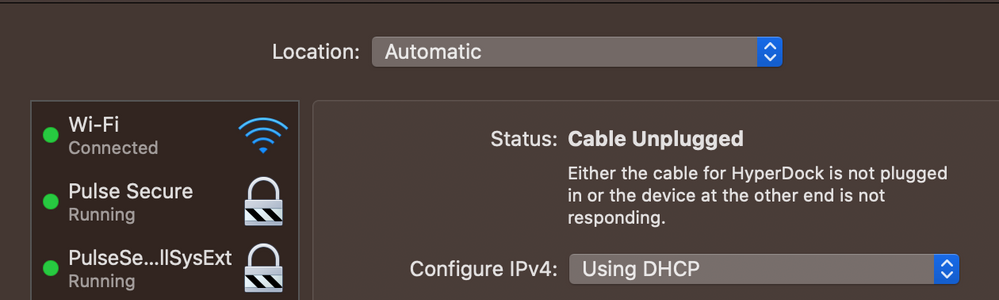
Anyone else on Catalina or Big Sur seeing multiple Pulse Secure 9.1.9 objects in the macOS Network Pref Pane? We are seeing...
-Pulse Secure:
A network interface that can be manually removed via minus button. It returns on certain Macs, but not on others. Macs can still connect to VPN without it.
-PulseSecureFilewallSystExt:
A (Network Content Filter) System Extension that can NOT be removed. Always active. Some Macs see this, others do not. Macs can still connect to VPN without it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-04-2020 12:44 PM
Is there any reason why you can't just use "Allowed Team Identifiers" instead of specifying individual extensions? Just curious if that's been tried at all, or if users would still get the approval prompts regardless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-06-2020 10:11 AM
I figured out why I was seeing (2) objects in the Network preference pane:
The 'PulseSecureFilewallSystExt' only appears if I enable a Network Content Filter profile in Jamf Pro 10.26.0 (I got the profile settings from the payload via Slack that were originally designed by a Pulse Secure support engineer). As soon as I removed the profile the 'PulseSecureFilewallSystExt' disappears.
These new extension types will appear in /Library/Preferences/com.apple.networkextension.plist.
Guess I need to wrap my head around exactly what the new Network Content Filter profiles are doing - I was simply trying to suppress the purple Network Content Filter notification pop-up ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-06-2020 10:16 AM
@timlarsen I have tried both a TeamID and an explicit extension names, too. I will do more testing soon. For now I'm waiting for Pulse Secure to release 9.1R10 because we are seeing crashing and other issues with 9.1R9. Thus wrangling the new annoying pop-ups has slipped in priority.
BTW: Pulse Secure Secure was recently acquired by another company (Ivanti) and my sales and support reps were both 'let go' last week (See https://www.pulsesecure.net/press-releases/pulse-secure-to-be-acquired-by-ivanti/).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2020 06:41 AM
Oh Geez, watching this closely, just rolled out 9.1.8 build 3999 have all (kexts,PPPC) etc in place all good so far on 10.15.7
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-09-2020 07:09 AM
Starting with Pulse Secure 9.1.8+ macOS 10.15 Catalina and macOS 11 Big Sur will not use legacy KETXs, but rather the new SEXTs (System Extensions). And they are more dynamic and load only under certain circumstances - depending on server-side configs like HostChecker, IPv4 Enforcement, and other factors (according to PS support call). So your mileage may vary in terms of what you are seeing (or not seeing) on your Macs in terms of the Network Pref Pane, the purple Network Content Filter pop-up, etc (and what type of profiles you are pushing from Jamf of course).
IM able to block (approve) the main System Extension pop-up (behaves just like the KEXT in terms of how Jamf profiles work). But I still cant suppress the Network Content Filter pop-up.
BTW: I was told PS 9.1R10 will drop this week.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2021 12:50 PM
Did you have any luck on this one. Still trying to get this to install without getting the Filter Network Content pop-up. Also running into this with Carbon Black. I have followed the instructions and even though everything seems to be approved via Configuration Profile, I am still getting a pop-up asking me for permission to Filter Network Content.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 06:58 AM
@mherbster Im still in the same boat regarding the Filter Network Content pop-up on both 9.1R9 and 9.1R10 (R10 is worse actually - I have a HostChecker timeout issue on Big Sur Macs on 9.1R10 (see https://kb.pulsesecure.net/articles/Pulse_Secure_Article/KB44643). We have an ongoing case with Pulse Secure support. They claim that 9.1R11 will be out Jan 25ish.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 08:32 AM
@dstranathan Are you seeing the host check process never complete on Big Sur 11.1? That's the issue I'm seeing with 9.1R10, and I believe it's a different issue that what's described in KB44643 as that looks to be a host checker crash rather than non-completion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 08:36 AM
I have 9.1.r9 working on Big Sur, unfortunately not via deployment but manual install, I guess a permission issue
to make use of 9.1.r10 the concentrator should be updated as well in order to make use of it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 08:50 AM
@sdagley Yes, HostChecker runs forever (never completes or possibly crashes - not sure) due to a clumsy bug involving how PS is parsing the Mac's OS version with macOS 11.1.
Typically I have been pretty happy with Pulse Secure as a SSL VPN solution. But the last few versions have been rough.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 08:58 AM
@dstranathan Oddly enough PS 9.1R7 does appear to work on macOS 11.1. My suspicion is 9.1r10 is built with the new libraries which return 11.1 as the OS version, as opposed to 9.1r7 using older libraries which would be reporting OS version 10.16.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-13-2021 11:06 AM
I'm still using 9.16 in BS (beta version) and with ho Host Checker, it's working fine thus far.
SImple setup, but luckily still functional.
I've read that a new BS version is possibly coming end of Jan ¯_(ツ)_/¯
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-27-2021 01:37 PM
I'm in the same boat as everyone. At least it is good to know we can bypass the first prompt to Allow Pulse Secure extension. What I found is that a user must have admin to approve system extension for Pulse Secure extension. It may be a problem if you do not allow admin in general. Additionally, has anyone tested whether you will need admin to allow the Content Filter prompt?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-27-2021 02:53 PM
Might be worth mentioning that Pulse Secure 9.1R11 will be released any day now ("Week of Jan 25, 2021").
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-13-2021 02:13 PM
Pulse Secure 9.1R11 has now been released
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-22-2021 08:13 AM
User approval of System Extensions (part of PDC starting in Catalina) is required as per macOS design. Workaround. N/A.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-23-2021 03:32 PM
System Extensions can be approved automatically via Jamf MDM profile (same as older KEXTs). However, the Network Content Filter pop-up does not appear to be avoided. However, if you disable IPv4 Traffic Enforcement on your Pulse Secure appliance, then macOS Big Sur will not display the Network Content Filter pop-up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-07-2021 10:46 AM
Running macOS Catalina (10.15.7) with Pulse Secure 9.1.10 (5655), I have been able to get Pulse working without any prompts for the end user utilizing these settings:
Found a KB posted by Pulse which is what my config is based on: https://kb.pulsesecure.net/articles/Pulse_Secure_Article/KB44783
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 11:15 AM - edited 09-29-2021 11:33 AM
@mrinaldi Based on your attached screenshots, it looks like you didn't apply ALL of the recommended settings/values t hat are listed in the Pulse Secure support KB article.
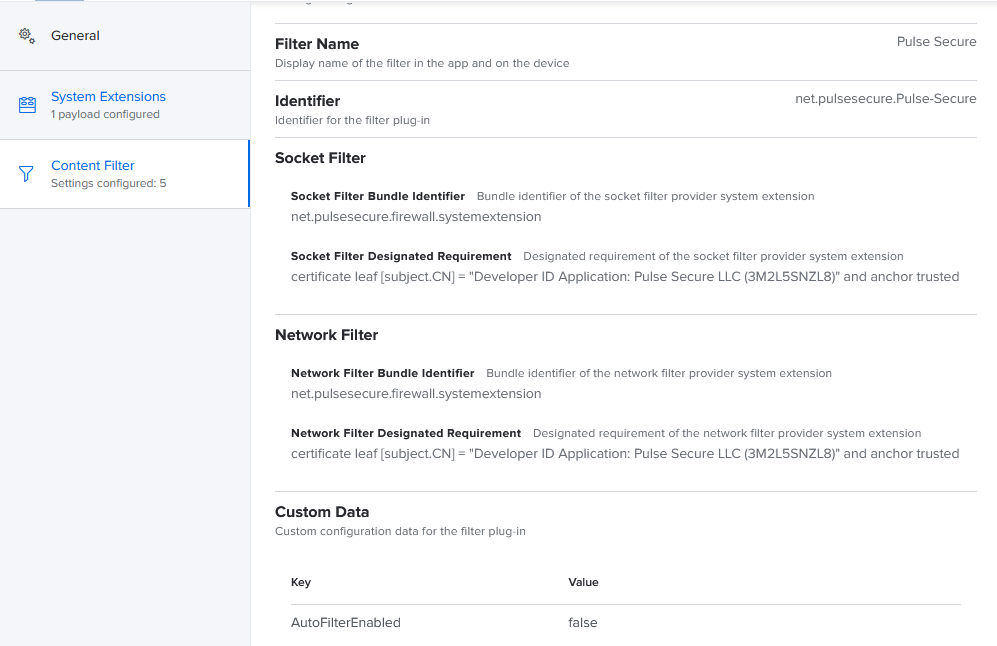
Are those setting simply missing in this screenshot due to cropping, or did you customize your profile differently than what Pulse Secure recommends? Example of some options that appear to be missing in your profile:
- payloadtype: com.apple.webbcontent-filter
- team-identifier: 3M2L5SNZL8
- FilterType: Plugin
- FilterGrade: firewall
- PluginBundleID: net.pulsesecure.Pulse-Secure
- FilterSockets: true
- FilterPackets: true
- FilterBrowsers: false
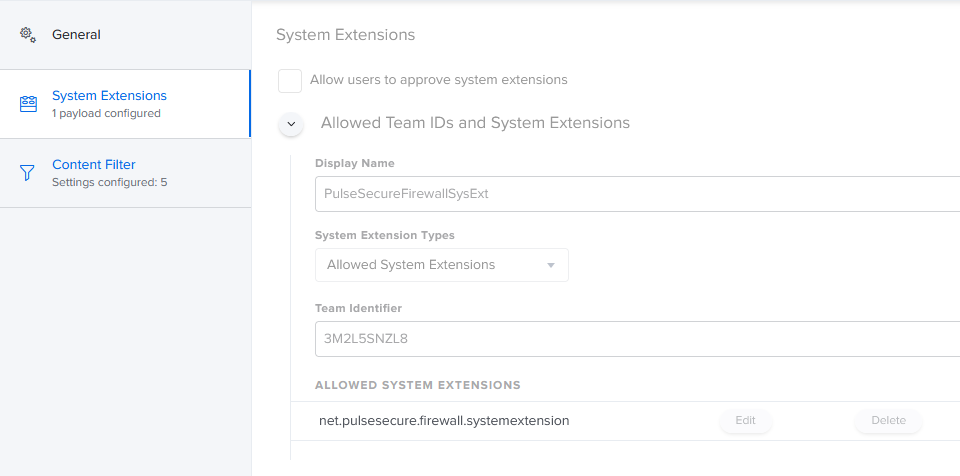
Here is an example of my prototype Content Filter profile (not in production yet)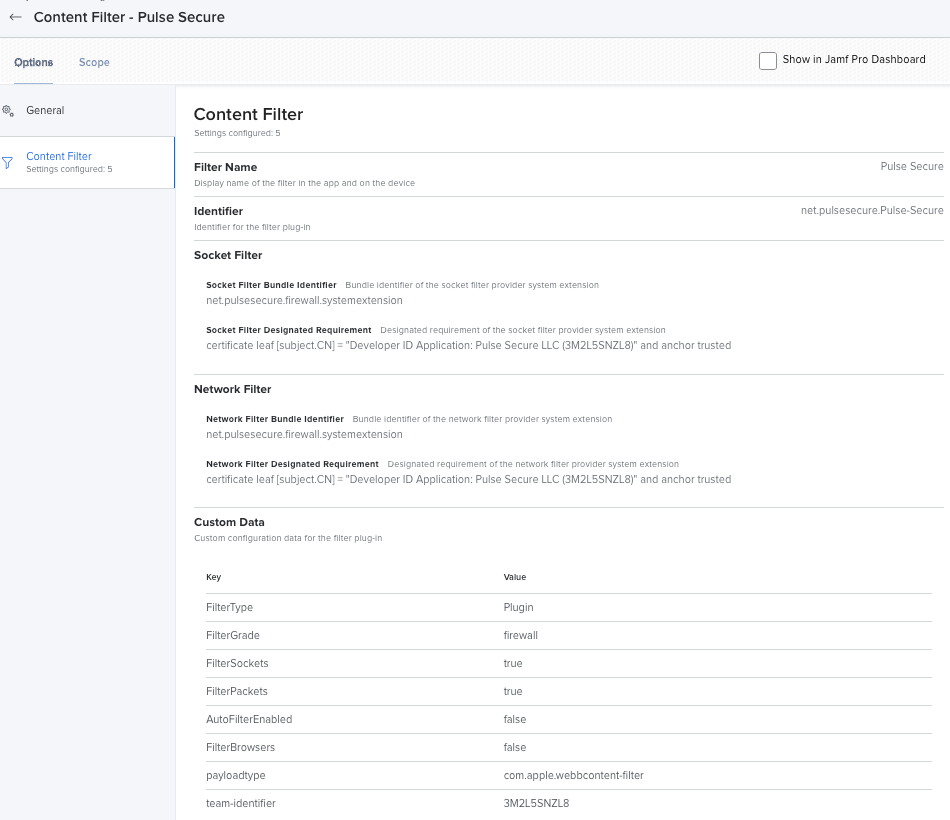
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-29-2021 11:59 AM
@dstranathan From what I can tell, those additional settings you mentioned are configured via the built-in fields within the Content Filter and System Extensions profile pages:
- payloadtype = automatically configured via Jamf. When configuring the "Content Filter" settings, it sets the payloadtype as "com.apple.webcontent-filter" automatically. Confirmed when looking at an export of the .mobileconfig of the Configuration Profile
- team-identifier = "Team Identifer" field within the "System Extensions" settings
- FilterType = automatically configured via Jamf. When configuring the "Content Filter" settings, it sets the Filter Type as "Plugin" automatically. Confirmed when looking at an export of the .mobileconfig of the Configuration Profile
- FilterGrade = "Filter Order" field within the "Content Filter" settings
- PluginBundleID = "Identifier" field within the "Content Filter" settings
- FilterSockets = automatically configured via Jamf. When configuring the "Socket Filter" settings, it sets the Filter Sockets to "true" automatically. Confirmed when looking at an export of the .mobileconfig of the Configuration Profile
- FilterPackets = automatically configured via Jamf. When configuring the "Network Filter" settings, it sets the Filter Packets to "true" automatically. Confirmed when looking at an export of the .mobileconfig of the Configuration Profile
- FilterBrowsers = since the Pulse article says to set this to "true" on the 2nd iteration, I saw in the Apple developer documentation that this is set to "true" by default, so I did omit this setting.
What I've laid out above is somewhat of a theory, but looking at an export of the Configuration Profile, it all does seem to match up based on what I could find.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 01:28 PM - edited 09-29-2021 02:56 PM
Thanks for the detailed answer - much appreciated!
Spitballing here:
Because the Pulse Secure Team ID in the System Extension's payload doesn't mean that the Content Filter's payload can see and reference the Team ID, correct?
I have my System Extension Approval payload (which contains the Team Identifier of '3M2L5SNZL8') and my Content Filter payload for Pulse Secure in (2) separate MDM profiles.
I'm wondering if I need to explicitly add the Pulse Secure Team Identifier (3M2L5SNZL8) to my Content Filter profile or not...?