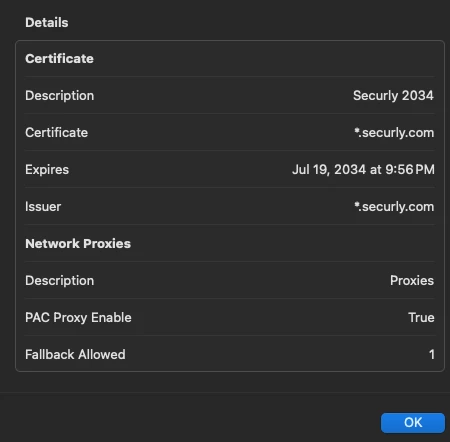
I am having an issue that I think is somehow related to Safari and our proxy. We have had several reports of users traveling off-network and having issues with captive portals. The Captive Network Assistant.app window appears but it's blank and says: "The webpage couldn't be loaded". If I open Chrome or Firefox, and go to https://captive.apple.com then the Captive Portal appears and I can do whatever I need to access the WiFi SSID. If open Safari, I am unable to get to https://captive.apple.com. Has anyone run across this issue? I'm assuming the Captive Network Assistant is using Safari to try to show the Captive Portal...
Question
Captive Portal Issues
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.