- Jamf Nation Community
- Products
- Jamf Pro
- Re: Catalina Single Sign On
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Catalina Single Sign On
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-23-2019 12:16 PM
Has anyone setup Single Sign on with Catalina OS? I heard about it in during their last event. I am up to date with the Catalina Beta but cannot find anything to set it up. https://developer.apple.com/videos/play/wwdc2019/303/ towards the end of this video is where it is mentioned. We want to have the Mac users login to their computers the same way our PC (All PCs are joined to Azure) users do by using their email address and password. Any recommendations?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-23-2019 02:24 PM
Brent,
The Apple directions/test plan are in the Apple seed for IT program.
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-23-2019 03:50 PM
I’ve set it up. Works good. Some features are missing when compared to Enterprise Connect, but otherwise it works good and suits our needs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-23-2019 03:57 PM
Just to be clear, the Single Sign-On extension doesn't allow for logging in with email addresses, does it? That's a whole other thing we can't talk about yet, or at least I thought. SSO extension is basically just EC built in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-24-2019 05:23 AM
@ooshnoo So you are able to login to your Macs using email address and password? You dont happen to have a walk through of the setup or a link to the setup that you did, do you?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-24-2019 07:08 AM
It is using AD, not Azure AD. So email address is not used to login.
@bmichael Setup info is not public yet. You need to use AppleSeed to get access to the config profile to test it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-25-2019 01:55 PM
@patgmac If possible and willing, can you share your SSO config that you're using to test??
Thanks in advance ::sp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-25-2019 02:44 PM
@smpotter @bmichael You can piece together what you need to create the profile from the ExtensibleSingleSignOnKerberos developer documentation. Alternatively update to Jamf Pro 10.15 as they have added the Single Sign-On Extensions payload.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-26-2019 08:28 AM
I have it working but was curious about it displaying how many days left till password expires. Per the doc it states to configure "pwExpirationDays" which I did but on the device its still showing "Password doesn't expire"...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-26-2019 08:43 AM
@smpotter I'm not using that key, and it shows a countdown of days until expiration by default. Plus I don't even see that key listed in the doc. Are you sure you're not referring to: passwordNotificationDays
https://developer.apple.com/documentation/devicemanagement/extensiblesinglesignonkerberos/extensiondata
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-14-2019 10:23 PM
Is it similar to Enterprise Connect PKI? I mean: does it support login/SSO via SmartCards?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 03:51 AM
Anyone know is SAP can work with this new single sign on mode - we are running nomad and no AD
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 06:26 AM
@ooshnoo to clarify you have local users able to SSO into web applications for example? What IDP are you using? Have you got any instructions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 06:30 AM
@jlattke it basically replaces Enterprise Connect. It can do SSO with smartcards. Super simple set up as long as you're using AD not AzureAD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 07:50 AM
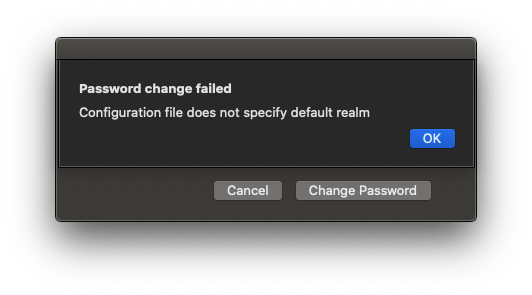
I have it mostly working, but get this error when I try to change the password.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 10:03 AM
@nvandam can you roughly describe how you set it up and what IDP you're using?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 10:10 AM
@petestanley , Here's the example .mobileconfig Apple has. Just change "example.com" to your domain. The upload that to Jamf and push to a 10.15 Mac. We are using AD.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>ExtensionData</key>
<dict>
<key>allowAutomaticLogin</key>
<true/>
<key>isDefaultRealm</key>
<false/>
<key>pwNotificationDays</key>
<integer>15</integer>
<key>requireUserPresence</key>
<false/>
<key>syncLocalPassword</key>
<true/>
<key>useSiteAutoDiscovery</key>
<true/>
</dict>
<key>ExtensionIdentifier</key>
<string>com.apple.AppSSOKerberos.KerberosExtension</string>
<key>Hosts</key>
<array>
<string>.example.com</string>
</array>
<key>PayloadDisplayName</key>
<string>Single Sign-on Extensions</string>
<key>PayloadEnabled</key>
<true/>
<key>PayloadIdentifier</key>
<string>com.apple.mdm.test.local.af517dc0-7353-0137-3524-3a008d11ab01.alacarte.single-sign-on-extension.79757090-7354-0137-3525-3a008d11ab01</string>
<key>PayloadType</key>
<string>com.apple.extensiblesso</string>
<key>PayloadUUID</key>
<string>79757090-7354-0137-3525-3a008d11ab01</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>Realm</key>
<string>EXAMPLE.COM</string>
<key>TeamIdentifier</key>
<string>apple</string>
<key>Type</key>
<string>Credential</string>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>Kerberos SSO</string>
<key>PayloadIdentifier</key>
<string>com.apple.mdm.RJLmpb.local.af517dc0-7353-0137-3524-3a008d11ab01.alacarte</string>
<key>PayloadOrganization</key>
<string>Apple</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>af517dc0-7353-0137-3524-3a008d11ab01</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-15-2019 10:25 AM
Thanks @nvandam!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2019 03:00 AM
@nvandam Thanks a lot for this, extremely useful.
I'm trying to establish whether we'd be able to use the Single Sign On Extensions in our lab environment and remove the bind to AD altogether. I'm assuming a user account would need to be created on the system first, and then the system would prompt to sync up the login and AD passwords once logged in?
Also, in my testing folks aren't prompted to enter their AD credentials until they open up Safari which has a company home page based on SSO. How can I get the user to be prompted without opening up a web browser?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2019 04:16 AM
@jazminepena While it's certainly not impossible I think something like NoMAD LoginAD or Jamf Connect would be more beneficial in a lab environment if you're wanting/working toward a no-bind setup. With the SSO extension you would need a local account logged into the machine from the get go.
The SSO extension should be prompting you as soon as the config profile is installed on the machine. At least that has been my experience with it thus far. Are you using the mobileconfig shown above or the provided payload in jamf Pro?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2019 05:32 AM
@mainelysteve Thanks. After some further testing, it does indeed seem to prompt after logging in.
I'm using the mobileconfig from earlier in the thread.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-17-2019 09:25 AM
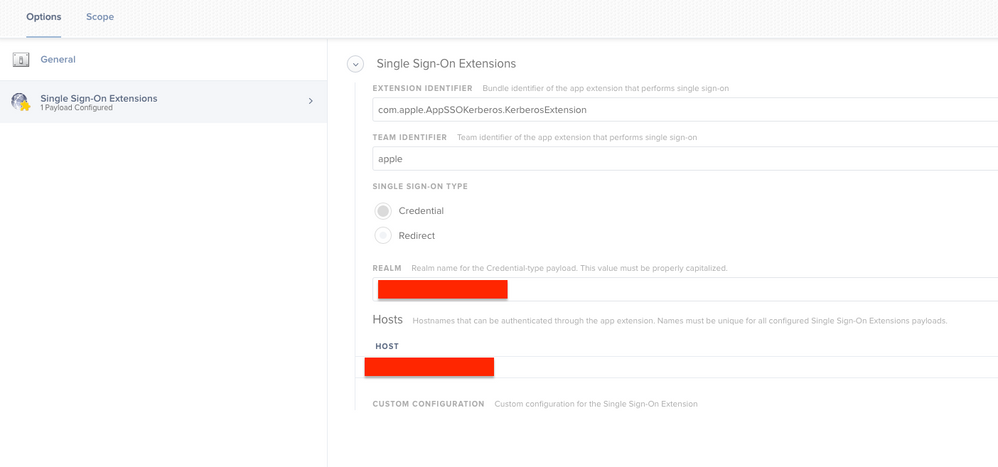
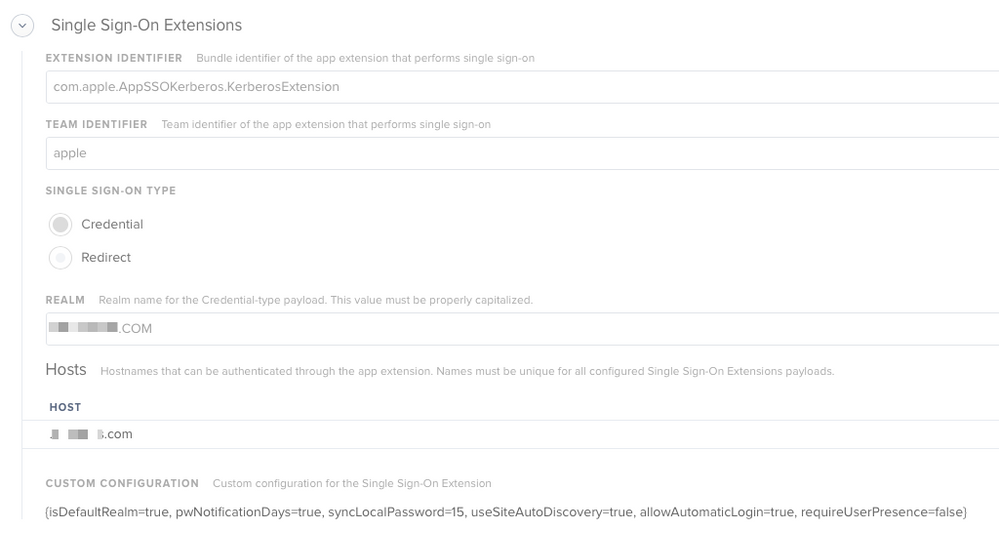
Has anyone figured out a way to pass your account credentials to the SSO extension when you're logged in with an AD mobile account? Screen shot attached of my current SSO profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-18-2019 12:51 AM
And does anyone know how I can set the option 'Sign-In Automatically' by default in the config profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2019 12:39 PM
@nvandam Did you figure out what was up with the "Configuration file does not specify default realm" error? I am also seeing that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2019 12:45 PM
@UbiquitousChris , I have not. :(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2019 01:09 PM
@nvandam We have the exact same issue in our environment. It wasn't happening in during the beta cycles, we were always able to change our passwords when we tried... but it started popping up around the GA release of 19A602.
Have you opened a FB or support ticket with Apple, have they given you any details?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2019 01:14 PM
@nvandam @UbiquitousChris Have you tried changing it to True
<key>isDefaultRealm</key>
<true/>- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2019 01:18 PM
@jmariani , I hadn't played with it during the betas, so I can't confirm it ever worked for us. I do not have a ticket open for that right now, no. But I can.
@ammonsc , I have tried changing that and rebooted and still nothing. I wasn't sure if I had it setup incorrectly because it says that capitalization matters, which I think I have it right, but honestly it may be wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-21-2019 01:39 PM
@ammonsc Yup. Heres a screenshot of our config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2019 06:07 AM
Just checking if others have this working properly? I am using the posted sample PLIST and changing the domain and realm. I can log in to an AD account fine, but (1) the extension is showing my password never expires, which is not true and (2) it is not sync my password with my local account. If I log out, I have to use my original local password and not my AD password to log back in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2019 06:46 AM
Which JAMF-PRO version are you using to view the Signal sign-on Extensions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2019 08:17 AM
@Vanegas , I believe it was introduced in 10.15.0. The payload settings are at like the bottom of the list in config profile creation view.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2019 09:12 AM
I'm guessing one of the options missing with this is the password-sync feature, checking if AD and local account passwords are different.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2019 10:21 AM
After looking at the configuration profile this seems very familiar to Apple Enterprise Connect. Am I correct to assume that there is not yet a way to use this with an off premise provider like okta?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-23-2019 01:31 AM
@sdamiano I think that is where Jamf Connect comes in.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-23-2019 08:39 AM
@nvandam I figured something out. If you add the following lines to /etc/krb5.conf, the extension will function again.
[libdefaults]
default_realm = YOUR.REALM.HERE- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-24-2019 11:55 AM
I have the same issue.. I;m working with my local apple tech team, but haven't figured out anything...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-24-2019 11:55 AM
@UbiquitousChris I looked for that /etc/krb5.conf I actually dont have that file... I have a krb5.keytab and that's it in that location
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-24-2019 12:05 PM
@jimderlatka I didn't have it either. I had to create it manually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-24-2019 12:16 PM
@UbiquitousChris wow that worked 100% working now.. thanks