Catalina Single Sign On
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-23-2019 12:16 PM
Has anyone setup Single Sign on with Catalina OS? I heard about it in during their last event. I am up to date with the Catalina Beta but cannot find anything to set it up. https://developer.apple.com/videos/play/wwdc2019/303/ towards the end of this video is where it is mentioned. We want to have the Mac users login to their computers the same way our PC (All PCs are joined to Azure) users do by using their email address and password. Any recommendations?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-12-2019 03:07 PM
What is the value for host? Is that suppose an alias for the realm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-28-2019 08:40 AM
Have tried SSO see screenshot, still can't get it to auto load and fill in their AD credentials automatically. Have tried adding the etc/krb5.conf and no joy. Wondered what other people have done on here to get it to work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-02-2019 07:16 PM
@VladCabrera Hosts are the hosts that you want the extension to perform authentication for.
i.e. kerberos-site.mycompany.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-02-2019 07:47 PM
Most likely you want your hosts to be ".company.com", notice the period. That way it covers all addresses under company.com.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-11-2019 02:29 AM
Hi @nvandam,
I've exactly the same problem, have you find a solution?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-11-2019 05:06 AM
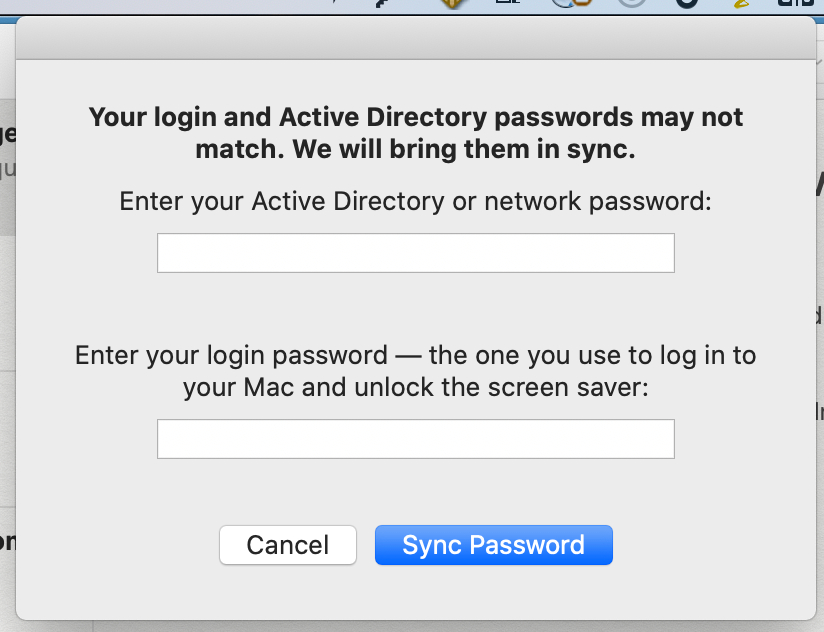
@bmichael thanks for creating this thread! I've combed through it and found some helpful information (kudos to @nvandam ) and got this up and running in our test environment. We mainly wanted it for syncing AD passwords with local accounts. Hoping to roll it out to about 650 MacBook Air users after a little more testing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-11-2019 06:17 AM
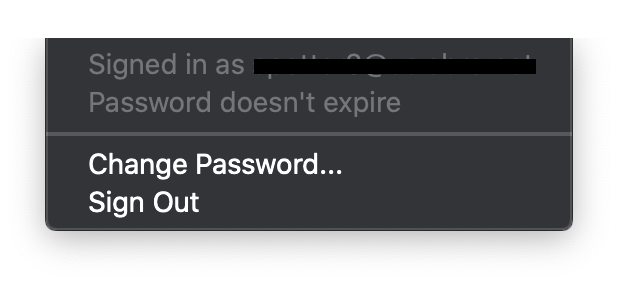
The only issue I'm seeing with the SSO is the fact that it states my password doesn't expire. Is anyone else seeing this behavior?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-11-2019 06:20 AM
When I would first deploy it it would report that my password never expires. Once I logged out and back in it would report accuratly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-16-2019 05:52 AM
I'm consistently getting "Password doesn't expire" plus when I navigate to internal sites that use SSO Safari just hangs on a blank screen. If I take out the leading "." in hosts, the menubar icon just says "Updating Updating" and Safari forwards to my company's SSO host (I'm assuming this is basically just what would happen without the plugin). Enterprise Connect with as many matching flags as are supported works great. I wondering if maybe I need a redirect style profile that points to some URL like https://sso.mycompany.com/somethingsomething.
A little bit more documentation on this would be lovely.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2019 11:29 AM
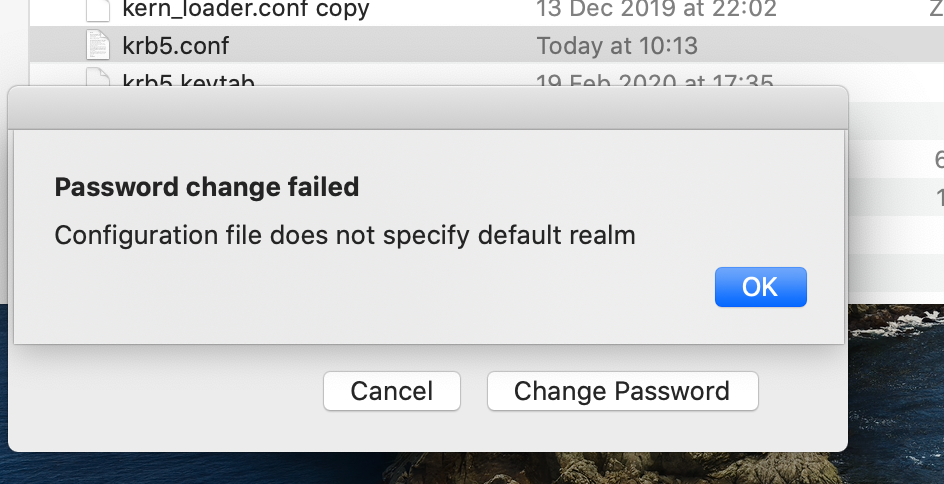
I added the krb5.conf file, and now, when I run a kinit, it's actually prompting for my domain password, and giving me Kerberos ticket. I ran a kdestroy and have been authenticating through some internal sites, but it will not give me a new Kerberos ticket. I used the plist by @petestanley above and only changed the host and realm. Any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-23-2019 05:04 AM
Hello everyone, I'm trying to manually install the SSO mobileconfig file posted by nvandam above, but I keep getting the following message: "The “Single Sign On Extension” payload can only be installed from a user-approved MDM server."
BTW, I'm using Profile Manager.
Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-23-2019 05:39 AM
It can not be installed manually. It's an MDM only like Approved Kernel Extensions or PPPC profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-08-2020 09:08 AM
I've got the Credential Plist to work in our environment, huge thanks to @nvandam and @UbiquitousChris for their screenshots.
Does anyone have a redirect plist example? I'd like to test a URL SSO profile but I'm struggling put the plist together.
TIA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-08-2020 11:09 AM
Gotta say, I'm sticking with Enterprise Connect and ignoring the SSO extension for now. The UX is better.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-19-2020 02:41 AM
Hi,
Does somebody knows how to enable Kerberos SSO Extension verbose logs ?
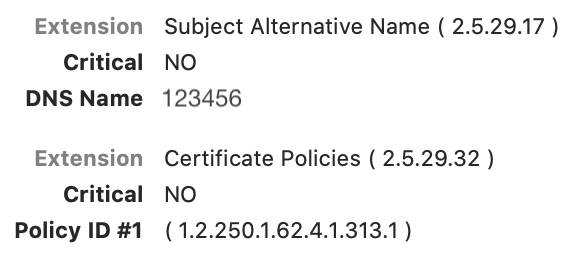
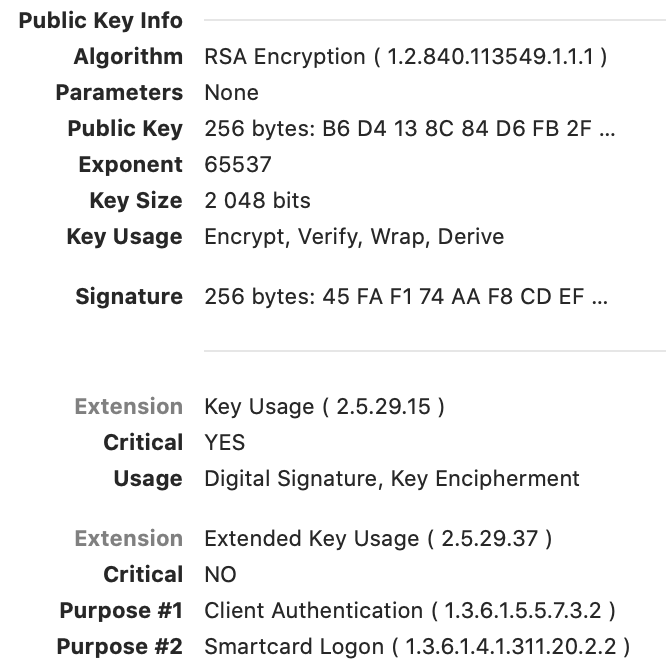
We use successfully Kerberos Extension with passwords but would like to switch to user certificates using Yubikey.
In Kerberos Extension chooser certificates doesn't list.
Note: certificates come from our PKI (same as smartcards) and have the following attributes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-21-2020 08:04 AM
@barcollege is that feature available in jamf NOW?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2020 02:23 AM
I have it working as well for our onprem AD.
though I see that the user has to login with his/her email address and not with the username.
is there a way to change it to username instead of email address??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2020 04:31 AM
Can I use this code for Redirect Extension in iOS?
var authController : ASAuthorizationController?
let authProvider = ASAuthorizationSingleSignOnProvider(identityProvider: URL(string: "https://example.com")!)
@IBAction func logInWithMSAL(_ sender: Any) {
if self.authProvider.canPerformAuthorization {
let request = self.authProvider.createRequest()
request.requestedOperation = ASAuthorization.OpenIDOperation.operationLogin
self.authController = ASAuthorizationController(authorizationRequests: [request])
self.authController?.delegate = self
self.authController?.presentationContextProvider = self
self.authController?.performRequests()
} else {
print("failed to perform authorization")
}
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2020 07:55 AM
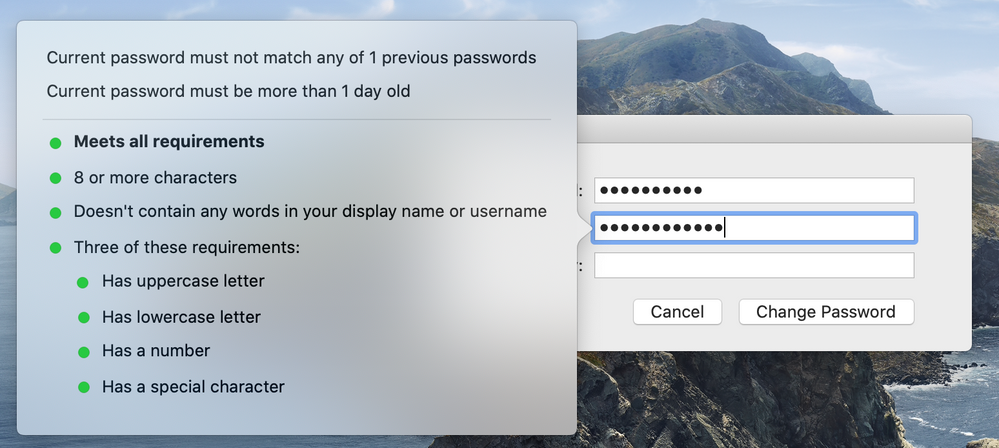
Hi all,
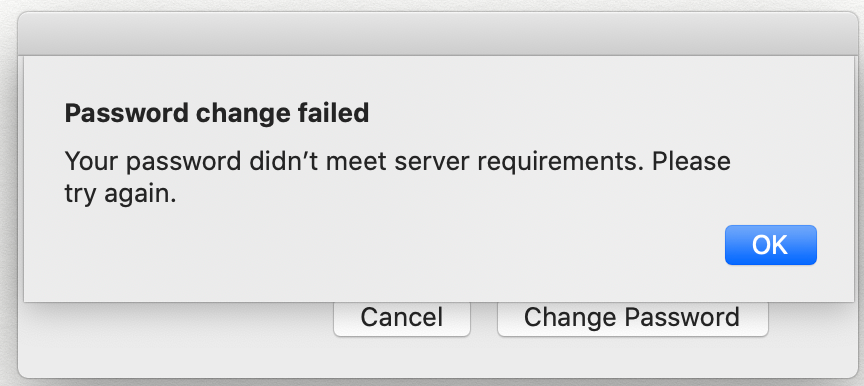
Great thread have this sort of working accept on password change I get the following error box even though I know I'meeting the password criteria which is min 8 characters, at least one upper case, a number and a symbol so a password like JamfPassword44! would be valid.
As I've been told the password failed if I log in with the previous password that tells me its incorrect
Now if I use the new password (the one that failed in the first screenshot) it works and I get the sync box:
So why am I getting the password failed when it works?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2020 12:25 PM
If anyone wants the document from Apple about all of this:
https://www.apple.com/business/docs/site/Kerberos_Single_Sign_on_Extension_User_Guide.pdf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-28-2020 09:49 PM
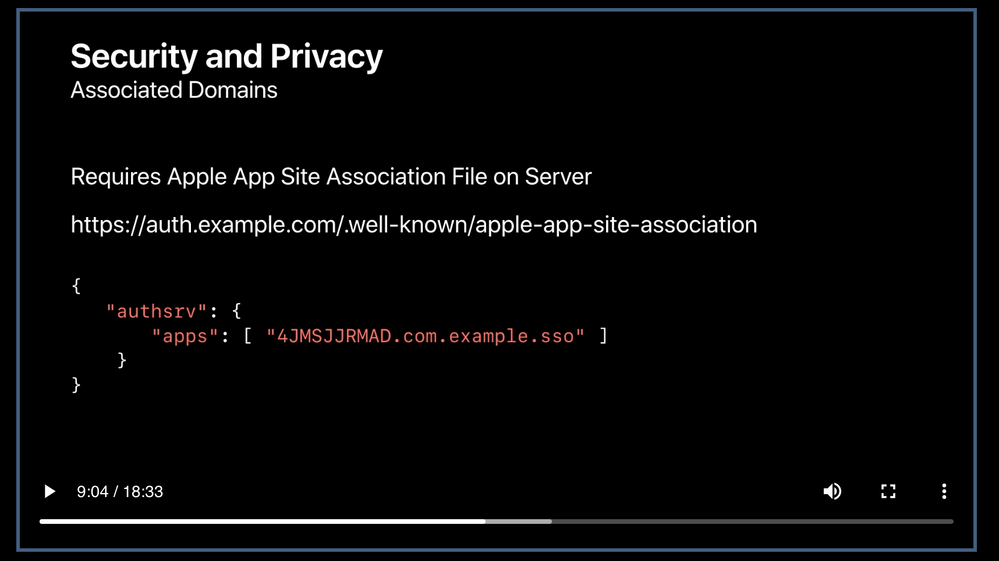
Where I will add the apple-app-site-association file for SSO extension?
In wwdc19 tech-talk videos they told to add a association file on server. My Question is that where I have to add this file "Identity provider" or "somewhere else"?
{
"authsrv": {
"apps": [TeamId.com.example.sso]
}
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-30-2020 01:34 AM
@andrew.nicholas thanks for sharing. I've got the green dots up and running
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-23-2020 10:49 PM
@jr139, did you roll it out to all Mac devices in your environment. How did you manage to deploy the krb5.conf file?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2020 02:23 AM
added the krb5.conf but still get the error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2020 04:48 AM
@jr139, did you roll it out to all Mac devices in your environment. How did you manage to deploy the krb5.conf file?
@Naveen_R We're still testing it internally in our department. We are going to get everyone on Catalina and roll it out this spring (hopefully).
We didn't have to do anything with the krb5 file. We simply rolled out the configuration profile with the extensible single sign on payload and changed the variables in the payload. We are most likely going to be blocking password change on the Mac side and directing everyone to a staff portal webpage to change their password. Since we have a variety of devices (both Mac and Windows) used by staff, we figured it would be easier to point them all to one location rather than have multiple sets of directions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-24-2020 08:12 AM
Is there a way on new Mac setup for this to Auto Login?
We set the Mac up using Jamf Connect Login which creates the user account with details via AD but we then would like the SSO Extension to autologin as one less user step is good :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-25-2020 06:44 AM
when messing with the kerb5 and other changes to the SSO Extension, you will need to run the following before the changes will take effect.
pkill -9 KerberosExtension- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-25-2020 07:14 AM
has anyone been able to add the pwchangeURL redirect and if so how?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-25-2020 09:23 AM
@ammonsc I just did, I added the following lines, and after pushing the updated configfile, when I go to change password it brought me to the page.
<key>pwChangeURL</key>
<string>https://your_url</string>- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-25-2020 11:28 AM
I have this mostly working in Catalina and basic Kerberos/SSO functionality is working.
We have an 802.1X password change script specified in our Enterprise Connect configuration that updates keychain passwords for things like WiFi and Outlook. I understand I need to create a LaunchAgent (as logged in user) with the trigger "com.apple.KerberosPlugin.ADPasswordChanged".
I've gotten this far with the LaunchAgent:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>KeepAlive</key>
<true/>
<key>Label</key>
<string>com.myorg.KerberosPasswordChange</string>
<key>RunAtLoad</key>
<true/>
<key>ProgramArguments</key>
<array>
<string>-notification</string>
<string>com.apple.KerberosPlugin.ADPasswordChanged</string>
<string>-action</string>
<string>/Library/Scripts/EnterpriseConnect/8021xpasschange.sh</string>
</array>
</dict>
</plist>Has anyone done this successfully with the Kerberos Single Sign-On Extension?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2020 06:58 AM
Has anyone had any luck getting their extension to fire? I believe I've got everything setup but it just doesn't trigger and I have no idea why.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2020 08:22 AM
@yuanyasmine I had to log out and log back in to get the extension to show up after deploying the configuration profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2020 01:09 PM
I've started working on getting the kerberos extension to replicate our current Enterprise Connect needs. I see in the documentation that there is supposed to be an example plist entry for something to watch for its distributed notifications, but it doesn't appear to be there. @jtrant I see you were working on one, did you have success with what you have here or has anyone else been able to get one set up successfully to run their password change script when the user changes it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2020 01:22 PM
@sheltond3 , no I wasn't able to get it to work.
I configured notification and action, and created a LaunchAgent running on my machine but it didn't fire. There's a "sample distributed notification" field but I can't figure out what that should be doing, or if it's even needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-02-2020 10:20 AM
thanks for getting back to me. I'm meeting with our Engineer rep from Apple on wednesday in person to work out some stuff with the Kerberos Extension and some other open tickets, i'll post here what we work out for the launchd and such.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-03-2020 04:32 AM
@jtrant I believe that "sample distributed notification" is the sample swift script above the sample shell script, since it looks like thats what handles the action and notification flags being passed. The real kicker is the line that says the developer tools needs to be installed to runs said swift script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-03-2020 08:29 AM
I was able to get the krb5.conf file working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2020 06:39 AM
Thank you, this makes much more sense, I had considered them as two separate items entirely. What concerns me is the requirement for developer tools as this is a no-go for most user laptops. I'll check with Apple since I have a case open and report back when I find out more details.
@jwojda , could you share your findings on the krb5.conf file?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2020 10:48 AM
So i realised my issue, the link I received for the documentation sent me back to a December 2019 version of the Kerberos User Guide doc, and the January 2020 version has the script and then below it has the launchd plist to use that script.
My problem that I have is that I really don't want to distribute the command line utilities to all my devices as it will now double our total enrollment package (we have a very light core apps load and everything else is done per user preference via self service). I'm racking my brain around how to use these notifications without having to deploy a swift script and using the CLT if at all possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2020 10:40 AM
I'm also still not able to get my password change script to fire even with using the sample scripts, launchd and steps for setup. Anyone having success with their password change scripts that can share with the class how they hacked around this new tool that in no way has feature parody to the tool it is supposed to replace?