- Jamf Nation Community
- Products
- Jamf Pro
- Re: How are you monitoring 13.3.1 (a) Rapid Securi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How are you monitoring 13.3.1 (a) Rapid Security Response?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 05:20 AM
Updated to 13.3.1 (a). Wanted to monitor via Smart Group but it doesn't look the fields populated after inventory check ins.
How are you monitoring?
The fields do populate for iOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 05:31 AM
What version of the Jamf server are you running? I think they just added the collection of those for macOS via declarative management in version 10.46.0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 05:34 AM
Ah ok. I'm on 10.45 and it gets updated this weekend.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 05:36 AM
Yep, so when you are on 10.46 those should get populated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:11 AM
Hijacking this thread to ask, how are you guys deploying this? Will it work with the existing mass action commands or software updates policy for intel devices?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:23 AM
Curious too. Was reading this: https://support.apple.com/guide/deployment/manage-rapid-security-responses-dep93ff7ea78/web
We Turn on “Install Security Responses & System Files” with a config profile. So I guess if users are on 13.3.1 and we send another Mass action command, this will scoop up the 13.3.1 (a) update?
Will test but please share your experience @Noonan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 07:36 AM
We had the config profile setting enabled for some time now. I sent out a mass action to a subset of devices, monitoring that right now, will keep you posted!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 07:38 AM
softwareupdate -l
Software Update Tool
Finding available software
Software Update found the following new or updated software:
* Label: macOS Security Response 13.3.1 (a)-22E772610a
Title: macOS Security Response 13.3.1 (a), Version: 13.3.1 (a), Size: 302500KiB, Recommended: YES, Action: restart,
Does look like this one requires a restart? "Action: restart,"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 08:22 AM
Yes, applying this RSR does require restarting the device, but the time is minimal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 09:16 AM
So I sent a mass action command for 13.3.1 with a deferral of 1 day and it behaved like a regular macOS update:
- Gave the normal prompt to install, try tonight, try later.
- Prompted for a password (Apple Silicon)
- Restarted the device (same speed as a normal restart)
Also noticed in jamf under the Operating System menu it stated it was downloading the RSR "Update in progress: MSU_UPDATE_22E772610a_patch_13.3.1_rsr"
I've got a separate Software Updates policy in jamf running for something else and it is installing the updates as well on our Intel devices.
Result of Software Update: 2023-05-02 20:49:59.608 softwareupdate[9666:70568] XType: Using static font registry.
Software Update Tool
Finding available software
Downloading macOS Security Response 13.3.1 (a)
Downloading: 0.10%
Downloading: 1.00%
Downloading: 1.90%
Downloading: 3.00%
Downloading: 3.90%
Downloading: 4.00%
Downloading: 6.90%
Downloading: 7.00%
Downloading: 8.90%
Downloading: 9.00%
Downloading: 9.90%
Downloading: 10.00%
Downloading: 16.00%
Downloading: 53.90%
Downloading: 54.90%
Downloading: 55.00%
Downloading: 60.00%
Downloading: 99.90%
Downloading: 100.00%
Downloaded: macOS Security Response 13.3.1 (a)- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:32 AM
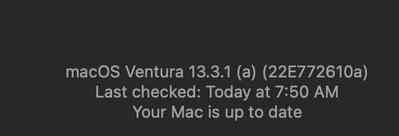
until JAMF updates.. use a smart group checking build version:
22E772610a
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 11:43 AM
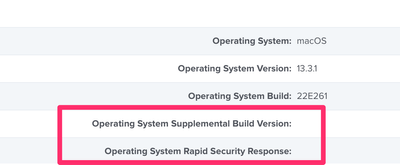
"Operating System Build" - like - "22E772610a" ?
Not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 11:49 AM
@mhasman Use the EA I posted in this thread - it looks like Jamf Pro 10.45 isn't always reportin the new build version properly
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 11:50 AM
Thank you! I'll try your EA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2023 06:36 AM - edited 05-02-2023 12:32 PM
@mvu For anyone not yet updated to 10.46 here is the EA I use to query the BuildVersion on the Mac (10.45 doesn't seem to properly report the build version after the RSR):
#!/bin/sh
# EA - Get macOS Build Numeric Portion
#
# Returns the numeric part of a macOS Build
# e.g. For Build 19H1030 returns 1030
result=""
rawBuildVersion=$(/usr/bin/sw_vers -buildVersion)
if [ -n "$rawBuildVersion" ]; then
# Return the value of rawBuildVersion starting at position 3
result=$(/bin/echo "${rawBuildVersion:3}")
fi
echo "<result>$result</result>"
exit 0Ignore the reference to the "numeric portion" since it's no longer correct with Apple adding alpha characters to distinguish RSR updates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:40 AM
I enabled the rapid security response for devices yesterday, but was not able to get Jamf to send a command to update the iPad. I was able to got into settings and install it. Normally I could send a remote command to start the update, but it did not work for the RSR for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:41 AM
Apple had issues rolling this out yesterday. Seemed to start working at night and today.
Did you try sending a MDM command today?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 06:43 AM
No I have to roll it back and try again. Working on that now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 08:28 AM
I got rolled back. I send the upgrade command from Jamf, and nothing happened on the iPad. A normal software update would prompt me for my password to install. This did nothing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 08:35 AM
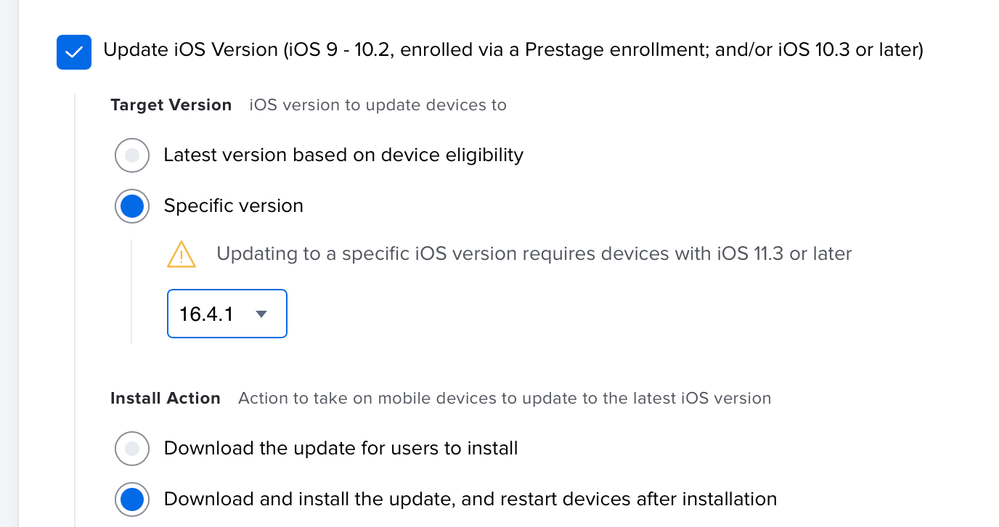
Which route did you try?
Latest version based on device eligibility or Specific version?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 12:54 PM
I did through latest and worked well. However, that'd be great if Jamf would include the (X) build to target it. Is it something possible under 10.46?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 12:57 PM
Agree, cuz "sw_vers -buildVersion" does show "a" at the end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 08:38 AM
Latest version based on device eligibility
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 08:41 AM
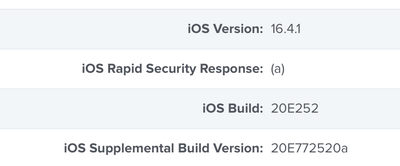
Can you try the Specific version 16.4.1 and see if the result is different?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 08:43 AM
I am getting this error: Connection to Apple Services is not available. Try again later.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-03-2023 10:44 AM
I am seeing this error now as well. Running 10.46.1. Were you able to resolve and if so how? Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 12:30 PM
RSR is part of the new Declarative Management so it better work without EA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-02-2023 12:34 PM
@Karl941 It should with JSS 10.46, but for those of us still running JSS 10.45 the EA seems to be necessary
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-16-2023 07:09 PM
My question s to make sure I am following correctly, once version 10.46 releases, we can also send mass builtin commands to update the machines and apply rapid response?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-16-2023 07:23 PM
I believe it only works for Macs with Apple silicon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-16-2023 07:37 PM
Thanks!
Question - is there plan for mass action to be made available where i can select specific version?
if not, how can I leverage the following script for 13.3.1a# Server connection information
URL=
username=
password=
# Determine Serial Number
serialNumber=$(system_profiler SPHardwareDataType | awk '/Serial Number/{print $4}')
initializeSoftwareUpdate(){
# create base64-encoded credentials
encodedCredentials=$( printf "${username}:${password}" | /usr/bin/iconv -t ISO-8859-1 | /usr/bin/base64 -i - )
# Generate new auth token
authToken=$( curl -X POST "${URL}/api/v1/auth/token" -H "accept: application/json" -H "Authorization: Basic ${encodedCredentials}" )
# parse authToken for token, omit expiration
token=$(/usr/bin/awk -F \" 'NR==2{print $4}' <<< "$authToken" | /usr/bin/xargs)
echo ${token}
# Determine Jamf Pro device id
deviceID=$(curl -s -H "Accept: text/xml" -H "Authorization: Bearer ${token}" ${URL}/JSSResource/computers/serialnumber/"$serialNumber" | xmllint --xpath '/computer/general/id/text()' -)
echo ${deviceID}
# Execute software update
curl -X POST "${URL}/api/v1/macos-managed-software-updates/send-updates" -H "accept: application/json" -H "Authorization: Bearer ${token}" -H "Content-Type: application/json" -d "{\"deviceIds\":[\"${deviceID}\"],\"maxDeferrals\":0,\"version\":\"12.6.1\",\"skipVersionVerification\":true,\"applyMajorUpdate\":true,\"updateAction\":\"DOWNLOAD_AND_INSTALL\",\"forceRestart\":true}"
# Invalidate existing token and generate new token
curl -X POST "${URL}/api/v1/auth/keep-alive" -H "accept: application/json" -H "Authorization: Bearer ${token}"
}
initializeSoftwareUpdate