How To Kernel Extension in High Sierra
Couldn't find an All in One Place regarding Kernel Extension information so here we go. Creating this thread so everyone can Chip In Best Practices. - Link to a thread like this if im wrong about not having a thread like this so we arent redundant
Kernel Extension List - https://docs.google.com/spreadsheets/d/1IWrbE8xiau4rU2mtXYji9vSPWDqb56luh0OhD5XS0AM/edit#gid=811130646
via gui you can do the following
I believe 10.13 & up you can locate them at /Library/StagedExtensions/Library/Extensions
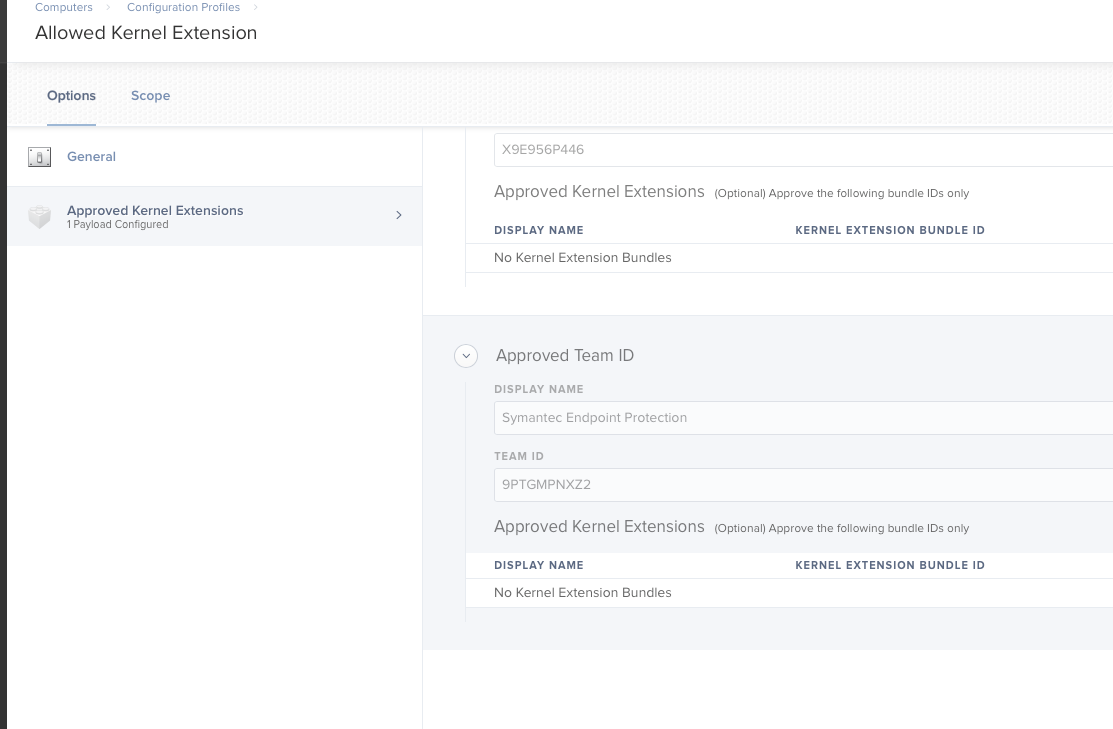
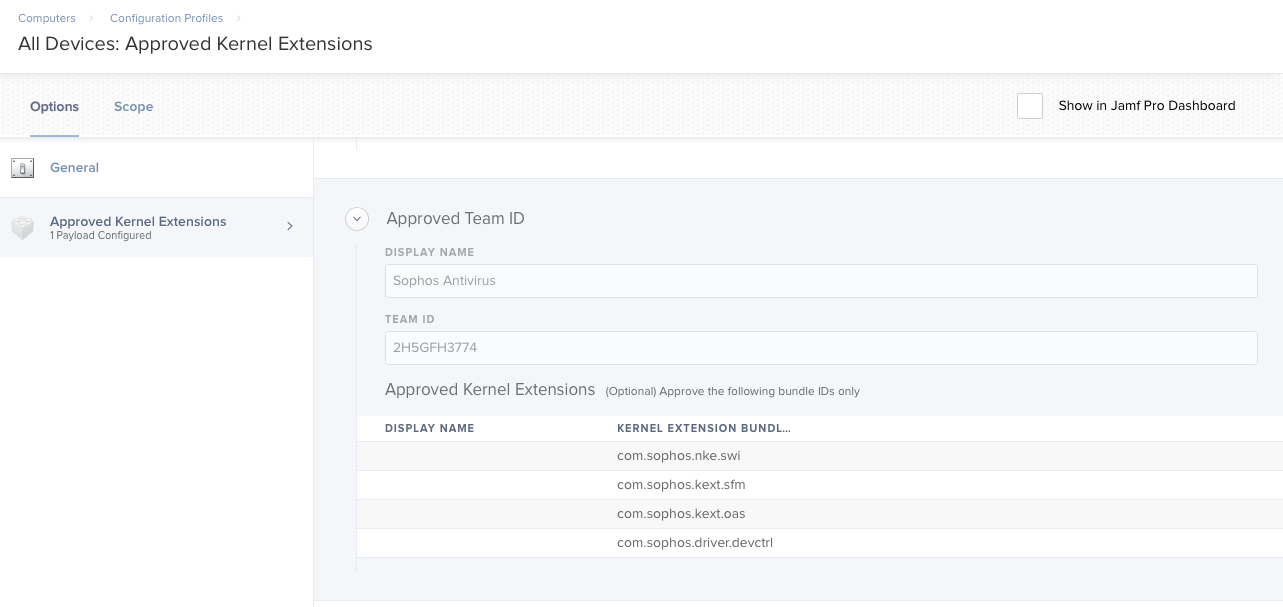
You can then find the BundleID by right clicking the kernel extension you want & select show package contents, then in contents directory you can open the .plist and view
for Team ID I only know this way - https://technology.siprep.org/getting-the-team-id-of-kernel-extensions-in-macos-10-13-and-higher/
In terminal run
sqlite3 /var/db/SystemPolicyConfiguration/KextPolicythen once in db run following command
SELECT * FROM kext_policy;it will produce the Team ID & associated KEXTS
What are methods / best practices you use?