How to set a self signed certificate to always trust.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-03-2020 08:41 AM
Hello, we where able to deploy a self signed certificate via JAMF configuration profile using the certificate manager.
Unfortunately the certificate is not set to trust. I can set it to trust via command line but I would need to find a way to deploy the certificate file to the macbook laptop then run a trust command via script. Unfortunately there seem to be no documented way to do this.
How can I achieve my goal. How can I deploy a self signed certificate and tell all our jamf computers to always trust that certificate.
- Labels:
-
Configuration Profiles
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-03-2020 08:49 AM
Can you not package it and have a post install script that installs it with trust settings?
Rich Trouton has a blog post here on how to add a cert to the System keychain with trust settings
The primary command is:
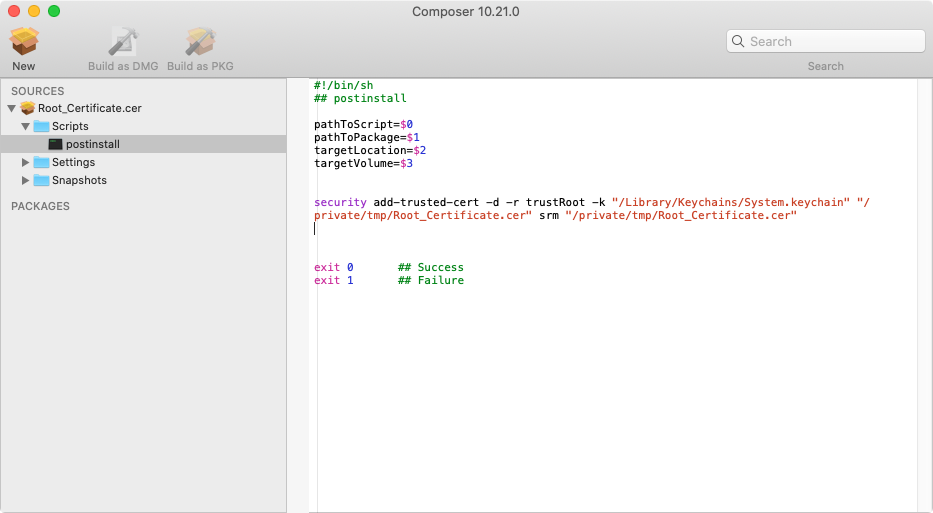
security add-trusted-cert -d -r trustRoot -k "/Library/Keychains/System.keychain" "/private/tmp/certs/certname.cer" srm "/private/tmp/certs/certname.cer"- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-03-2020 09:01 AM
@Tangentism thanks.you mean I should package the cer file to a PKG or DMG file using composer? I tried with PKG but the build failed to sign with composer. I might have done something wrong. And with DMG. I set it to cache but still don't know how to extract the file from cache. If I can find a way to deploy the cer file to the mac file system the rest would be easy as I can always write a script that uses the directory path where the cer file was deployed and get the keychain to add and trust it. So far I can not find a way to have the cer file deployed to the mac.
I am very new to the mac by the way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-03-2020 09:37 AM
No worries - we all begin as novices!
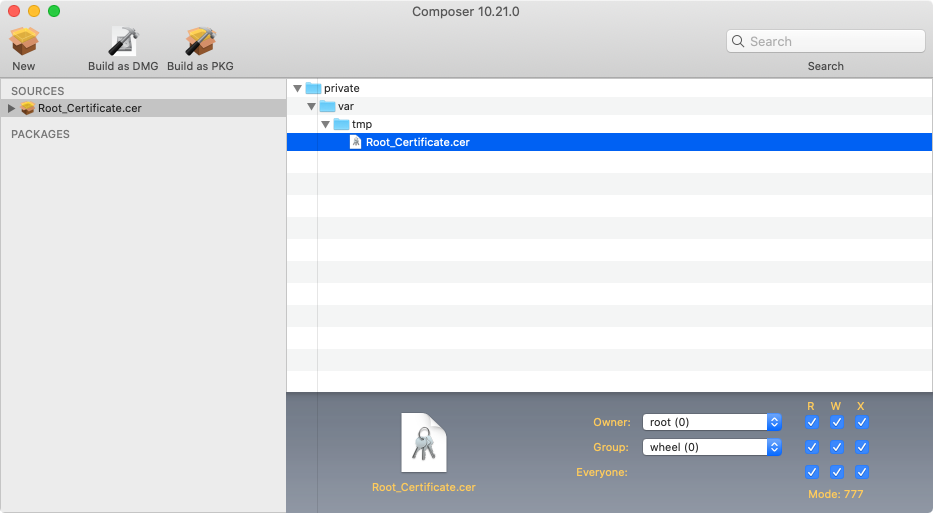
Copy the certificate to /private/var/tmp
Drop it into Composer
Check the permissions are appropriate
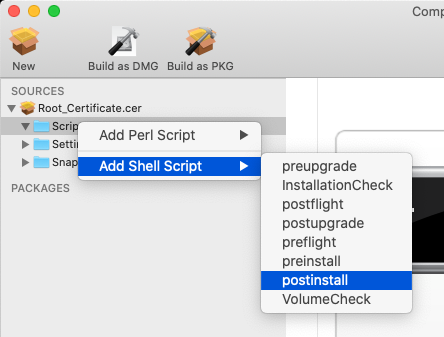
Expand the name of the package in the left hand column so the 'scripts' folder shows
Right click and 'add shell script' > postinstall
Add the previous shell command to the script, adapted to point at the certificate
Build as PKG
Add to policy so it gets delivered to all the machines scoped
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-03-2020 10:08 AM
Wow Thanks @Tangentism I am going to try that out now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-03-2020 10:21 AM
It's easier to just echo the cert out to a temp file, then run the command to import. Avoids all the packaging/distribution steps, and can be done in a simple shell script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2021 06:23 PM
Hello
Is it still working correctly? While performing, GUI pop up appears asking for a password to change trust settings. Is it possible to bypass GUI and use only Terminal?
Its working fine before Big-sur.
Only on Big-sur i am getting these pop ups.
and getting error logs in jamf pro logs>>>>
SecTrustSettingsSetTrustSettings: The authorization was denied since no user interaction was possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-09-2021 08:22 PM
In Big Sur, you cannot import a certificate to the system keychain without user approval, since malware can take advantage of that. If it can, the OS will prompt the user to authorize with their credentials. If it cannot, you get the message above and it silently fails.
You pretty much have to use configuration profiles pushed by MDM on Big Sur. We switched to that and it's working well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-06-2021 08:59 AM
Can we get an example of the config profile or a how to?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-22-2021 12:35 PM
@alexjdale Do you still need the script to trust it without asking the user to trust? I am looking to install a cert for a radius AP and want to ensure the user just needs to authenticate and not give permission to the cert to approve it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-19-2021 02:30 AM
stall hanging here... do you have an conf profile example for a MDM deployment to trust the certs ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-20-2021 01:06 AM
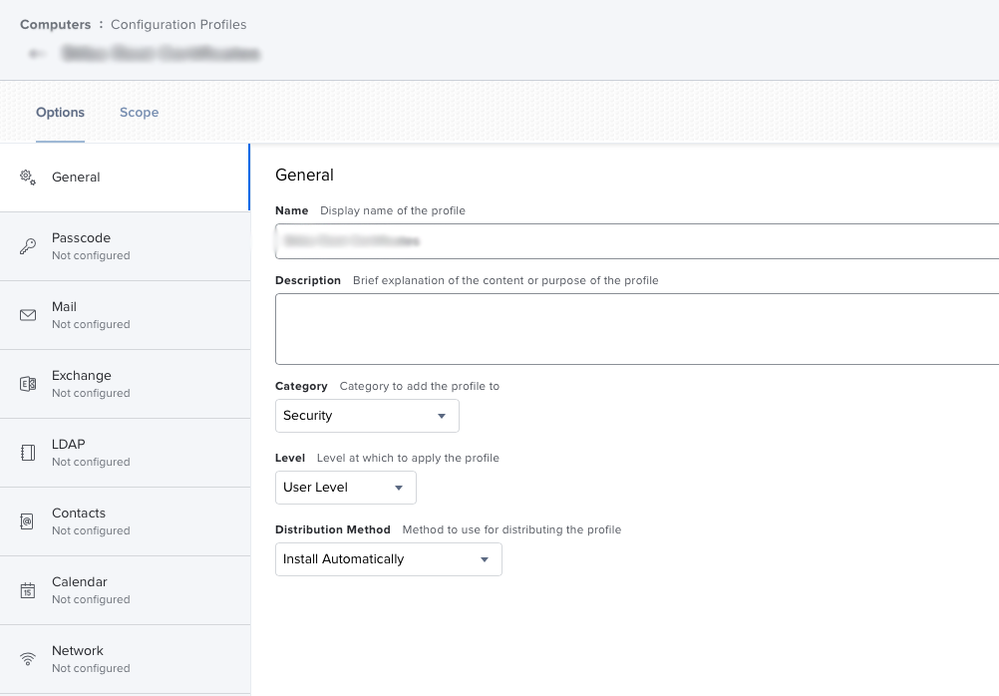
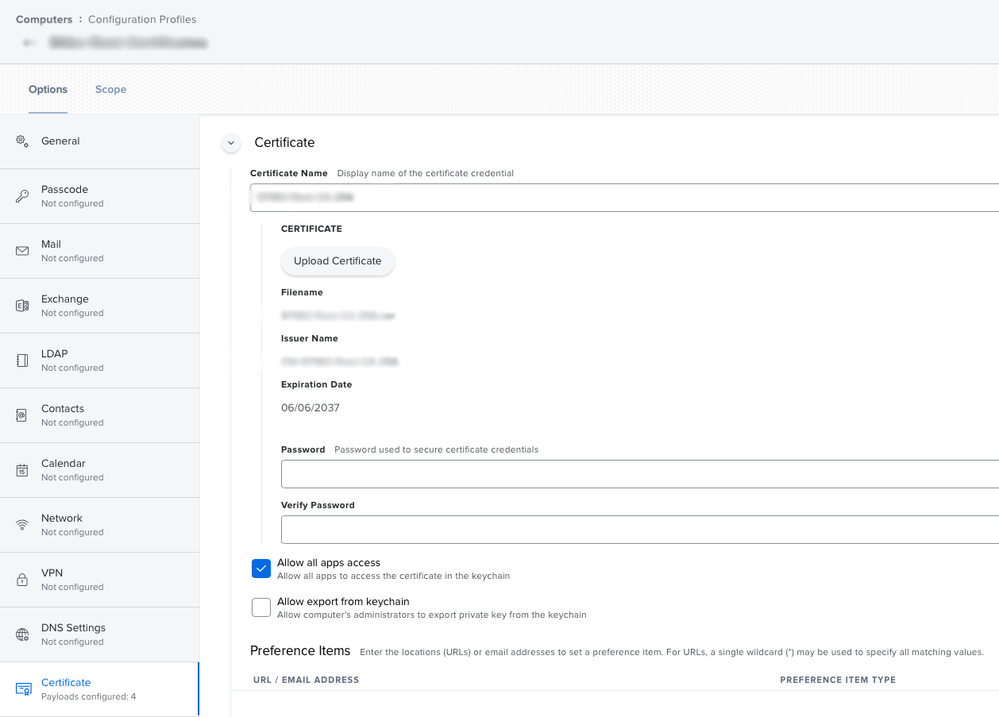
We're using the following configuration profile to install four certificates on Big Sur. The root certificate in the screenshot get's set to "Always Trust" for all purposes but two intermediate certificates issued by the root certificate plus a fourth don't. They get set to "Use System Defaults" which means that users still may get prompts to trust the certificates. Unfortunately I don't know enough about certificate chains to explain or rectify this so I'll manually trust these when configuring a new computer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-08-2021 03:38 AM
Hello. I also have the same issue like "kgam". Yesterday the system admin had changed a wildcard certificate. Today we have troubles to login in Skype for Business. I have no chance to enroll the certificate via
security add-trusted-cert -d -r trustRoot -k "/Library/Keychains/System.keychain" "/private/tmp/certs/....cer" srm "/private/tmp/certs/.....cer"
. With configuration profile i can enroll the certificate, but trusting is set to "Set System Defaults".
I also don't know, why macOS don't trust the certificate. We have also checked the requirements:
https://support.apple.com/en-us/HT210176
https://support.apple.com/en-us/HT211025
Do somebody have an idea?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-22-2021 07:10 AM
@ICS_Apple_Admin -- This is the exact issues I'm seeing- any luck?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-24-2021 12:28 AM
@Mac_User_- The whole certificate chain was not existing. We have put the Digicert Root certificate to the one certificate. Nevertheless we have to always trust the certificate - and this doesn't work.
I have written a documentation for the users to manually put in the skype4b server urls.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-25-2021 07:56 AM
@ICS_Apple_Admin -- I was able to fix this issue by manually trusting the cert in Keychain Access then exporting it as trusted, adding it to config profile. Successfully pushed out as trusted!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-25-2021 07:59 AM
Hi Mac_User_ it might be trusted for you - but please try from another Mac...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-25-2021 08:00 AM
I mean it might be trusted for your Mac already.. and user account
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-25-2021 08:02 AM
haha I appreciate looking out. I definitely tested on several macs. A few straight out of the box, worked flawlessly. I think it helped that I exported the cert from keychain of local managed account.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2021 03:23 AM
This...doesn't make a lot of sense. Did something else with your deployment change? Importing a PEM or CER to the keychain and then performing an export to the same doesn't change anything about the public key of the cert. Whether or not a cert is trusted or not isn't determined within the metadata of the certificate itself.
I'm in the same boat as the string and did try what was suggested. It made no difference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2021 06:31 AM
hah @Scotticus26 - I was as surprised as you. I wish I remember which random rabbit hole I read to try that. I had been scanning mac admin slack, reddit, and jamf nation. I never said I could explain why it worked, didn't work for other certs - except for the specific one I needed to deploy for VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2021 06:32 AM
Get Outlook for iOS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2021 06:32 AM
Not trying to mislead anyone - I don't claim to be an expert. Just tried something in desperation and somehow it's worked so I shared my experience. I apologize if it's not helpful to anyone else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2022 07:22 AM
Ok.. weird because I have done this trick, it has worked on my Mac, on which I got the trusted certificate, but not on other Mac. Still hoping to find a way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2022 06:45 AM
so just for a sanity check, when pushing a cert from a config profile, checking the Allow all apps access box is the same as going into keychain and changing the trust from default to always trust??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-12-2022 10:26 AM
Not from my experience, no.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-21-2022 02:41 PM
So I was running in to the same issue. The script would import the cert but it would not trust it. After a couple days on and off working on this. I finally realized that I was using the wrong -r command. I was using trustRoot as suggested above. But the cert I was using was not issued by another cert. So I had to change the –r command to trustAsRoot. example below. Hopefully this helps some of you.
Security add-trusted-cert -d -r trustAsRoot -k /Library/keychains/system.keychain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2022 07:24 AM
Great it worked for you. I guess it depends on the certificate chain we need to deploy..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-08-2022 04:23 AM - edited 11-08-2022 04:24 AM
Hi all!
I guess there is no further information from Apple for this "Issue"?
Devices with Monteray or Ventura won't fix the prompt upcoming, CPU Architecture also doesn't matter...
It is painful with our 5-6 Certs trusting manually.
Hope there will be an enterprise-friendly solution as soon as possible.
Greetings!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-08-2023 11:46 AM
Any updates on this issue anyone?