We have a bunch of old non DEP Mac's that when we install HS 10.13.1, we are unable to kick off FileVault through any policy. It tell us it's going to do it but never does. The policy completes successfully and in the history we get: FileVault is Off.
Deferred enablement appears to be active for user 'someuser'.
<<<<Begin Policy>>>>
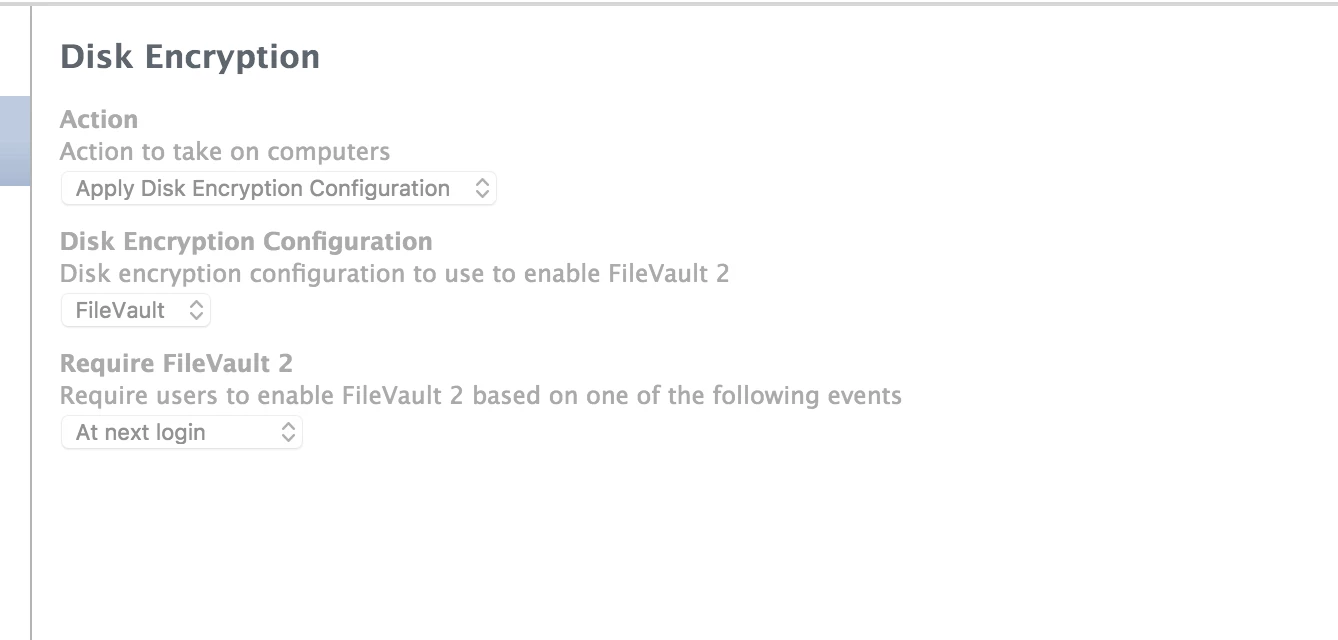
Disk Encryption
Action
Action to take on computers
<Apply Disk Encryption Configuration>
Disk Encryption Configuration
Disk encryption configuration to use to enable FileVault 2
<FileVault>
Require FileVault 2
Require users to enable FileVault 2 based on one of the following events
<At next login>
Thanks