- Jamf Nation Community
- Products
- Jamf Pro
- iOS 802.1x Enterprise wireless
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
iOS 802.1x Enterprise wireless
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
07-25-2019
06:45 AM
- last edited on
03-04-2025
02:29 AM
by
![]() kh-richa_mig
kh-richa_mig
Hello,
We are investigating the possibility of joining our iPad estate to our 802.1x enterprise wifi, utilising Microsoft network policy servers and Meraki wireless.
Information about this topic looks to be sketchy. I've seen some rather old articles from 2012 using NDES, but nothing recent.
I've seen other old articles that mention utilising authentication via username and password, but we are looking at device based authentication in the same way as our Windows clients rather than user based.
I'd be grateful for any signpost, information, tit-bit that anyone has to offer as information looks to be scarce!
Thanks!
- Labels:
-
Configuration Profiles
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-26-2019 07:10 AM
You may need to contact Cisco/Meraki support. I use Aruba Clearpass and I needed to setup one of my Tomcat servers as an Endpoint Context Server to import known devices to Clearpass. Once they were known it was just a matter of setting the end point to say Endpoint = Corp = True and setting up a role / policy to allow access. I checked Cisco's site and it's not friendly, good luck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-26-2019 07:35 AM
If you find any more information - I'd be grateful. Using NPS and 802.1x in our environment, as I was told, requires a bind to AD in order to get the machine certificate to pass back to NPS for identification as a valid network device
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-26-2019 08:12 AM
https://social.technet.microsoft.com/Forums/ie/en-US/a47aff4e-83b0-4367-b632-5f445c54f028/how-to-enforce-certificatebased-authentication-in-nps?forum=winserverNAP
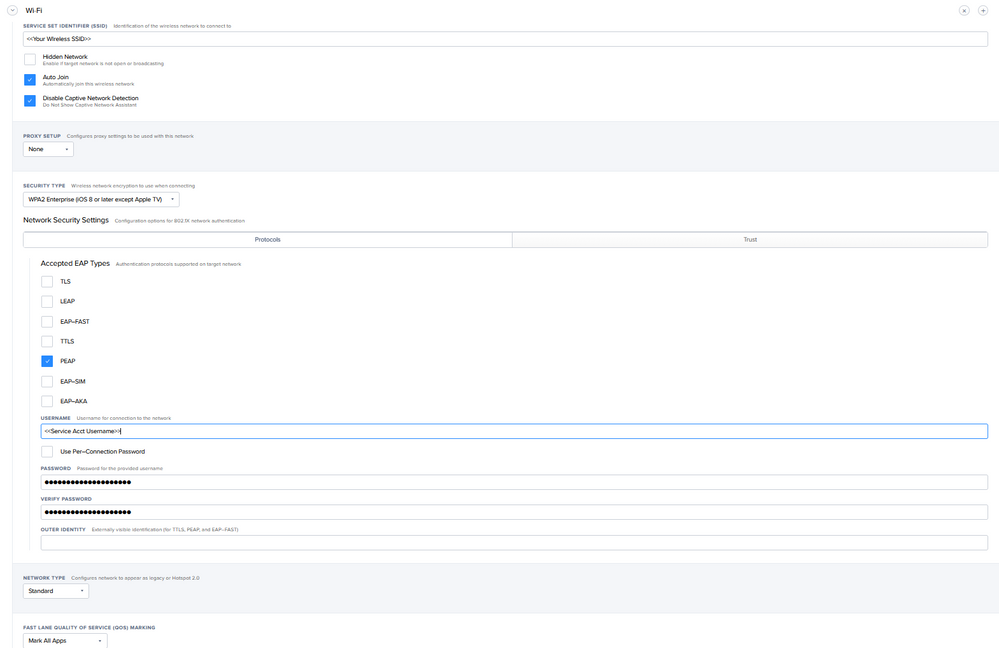
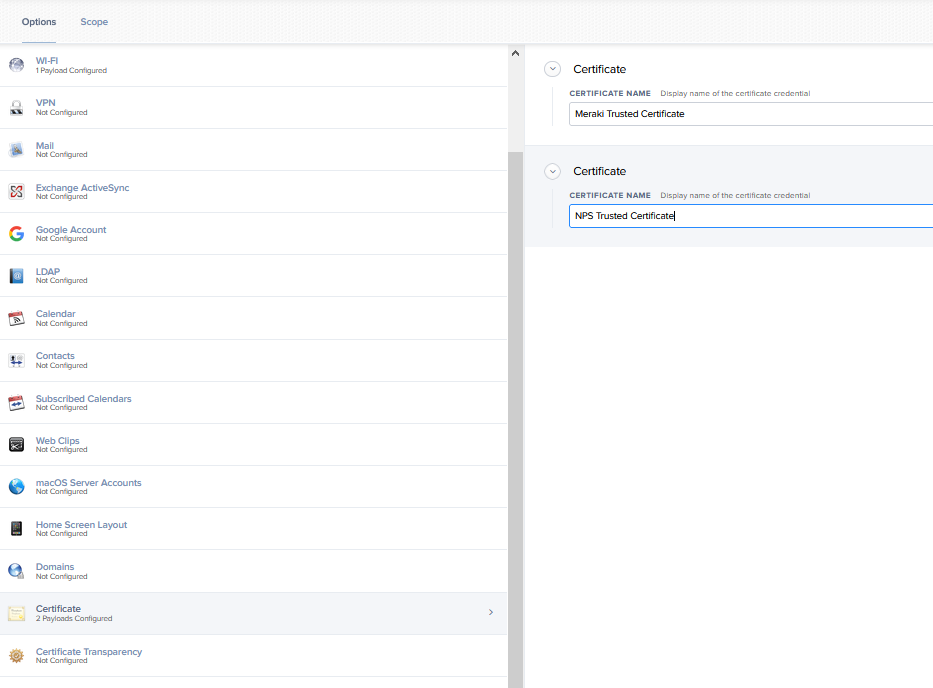
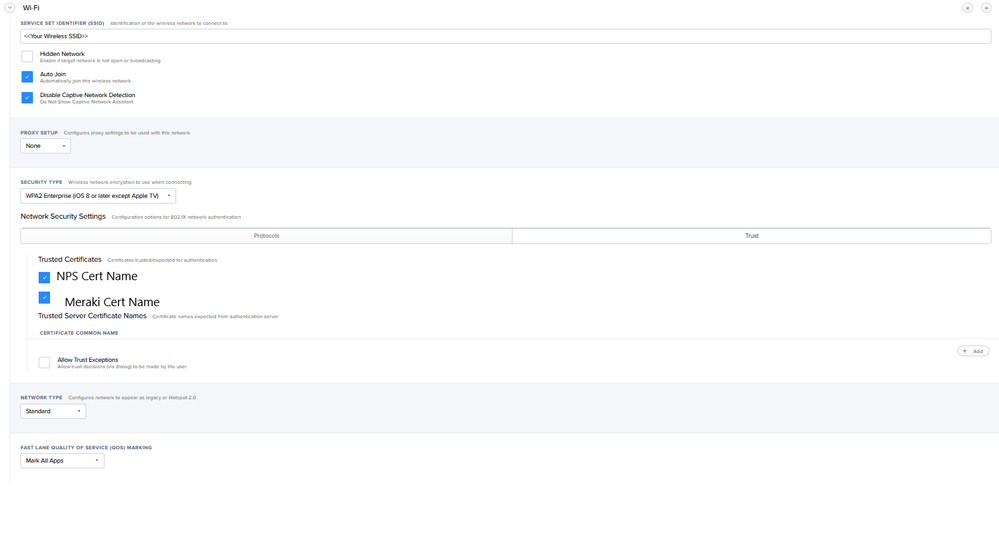
I'm looking at NPS and it seems like the best-ish way to do it would be to setup a wireless service account for your iPads. Then in JAMF create a wireless network payload that includes both the Meraki and NPS certificates.
It would still be using user and cert based authentication but it would get them online. We used a system similar to this for our classroom iPads for a while but have since gone to 1 to 1 iPads and users logging in as themselves.
EDIT- You will want to install this profile on the devices before deployment. Which means a single AP with an open SSID or PSK network will need to be created. I just had it in my office for setup then deactivated it when not in use. It's also possible to use a current users wireless logon to get network access, on reboot the iPad should switch to the profiled user account.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-26-2019 08:48 AM
I figured out a way to do 802.1x RADIUS authentication using public SMIME certificates and AD accounts: https://www.jamf.com/jamf-nation/discussions/29021/eap-tls--radius--public-certs-ipad-certificate-authentication
Basically I was able to have placeholder accounts in AD that I mapped a certificate to, and then used a configuration profile to say 'authenticate with this certificate'. Not super straightforward, and might not be scalable based on your security requirements, but it is possible :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-26-2019 02:30 PM
If you are deploying Certificate manually then you can do a configuration profile with WIFI / CERTificate payloads.
however, if you want to automate the process it gets very complicated. make sure LDAP is in place in case you want to deploy identity certificate. then AD CS Connector setup for Jamf to request certificate in your machine's behalf. then, there is attaching the user to the machine..etc. all the above requires no Binding to AD.