Hello,
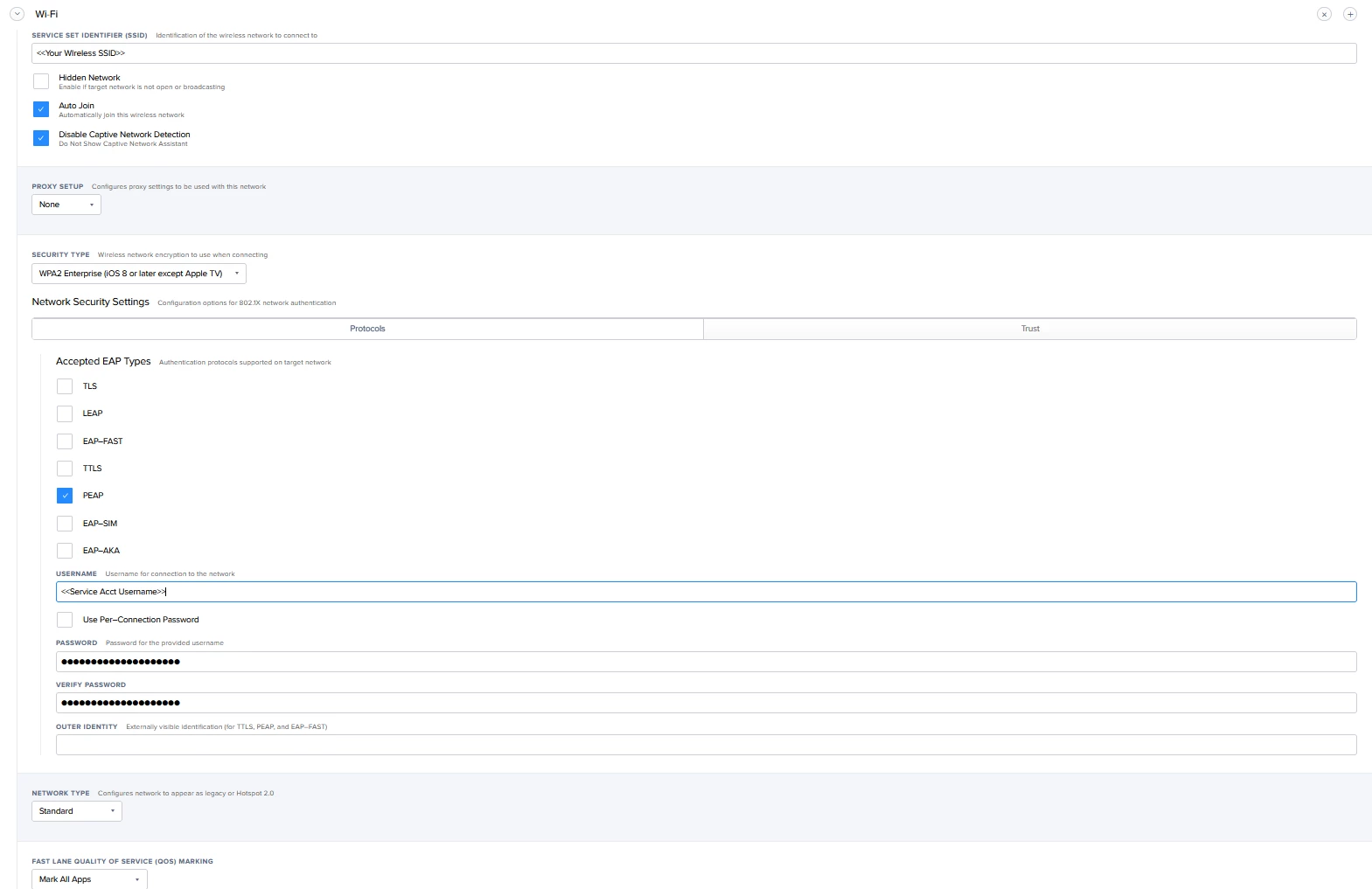
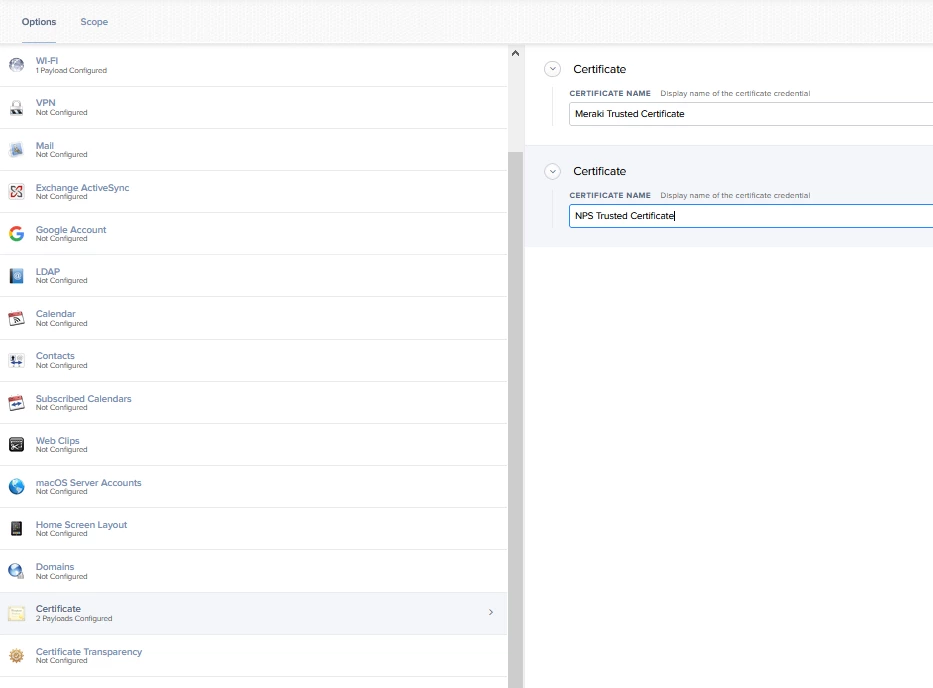
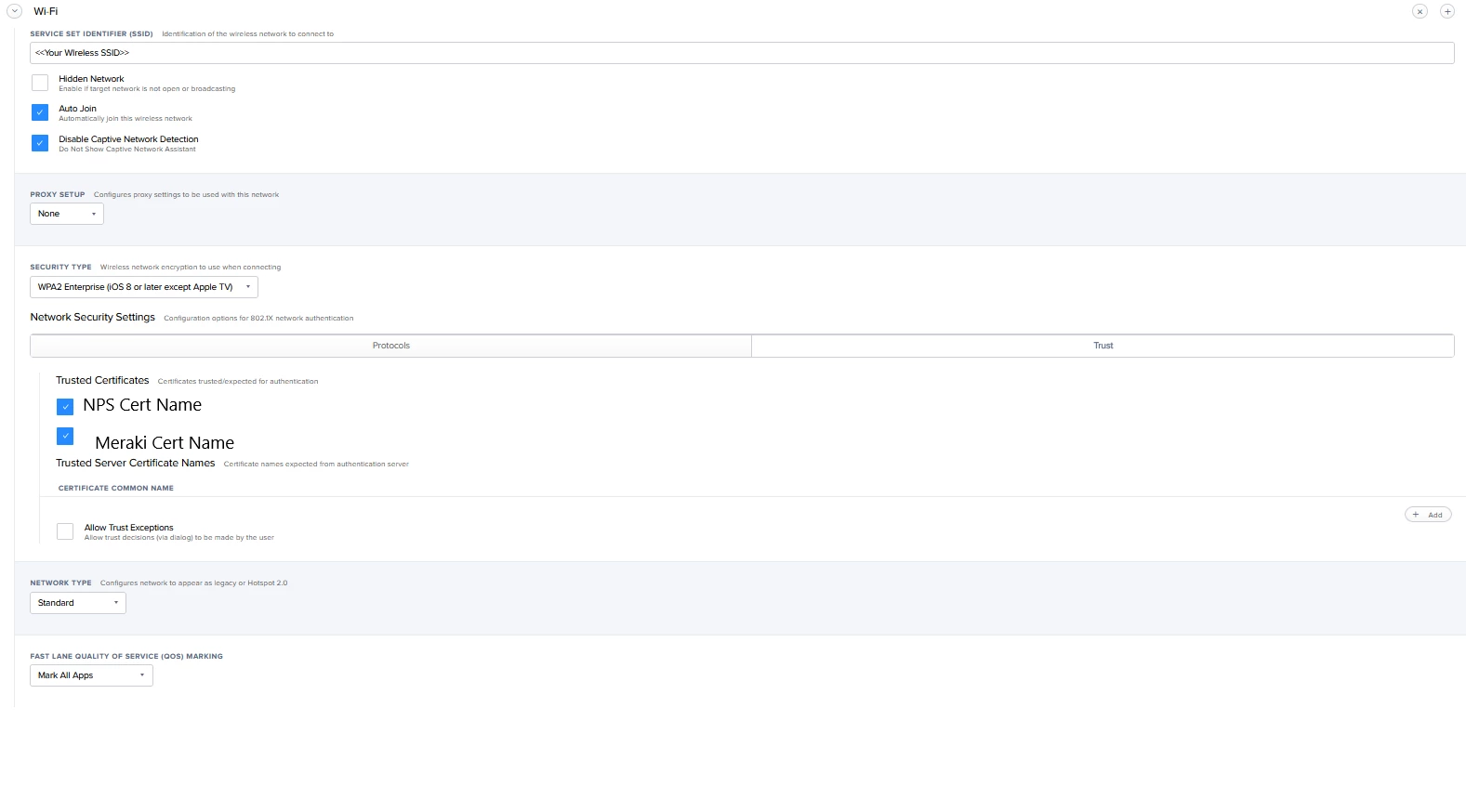
We are investigating the possibility of joining our iPad estate to our 802.1x enterprise wifi, utilising Microsoft network policy servers and Meraki wireless.
Information about this topic looks to be sketchy. I've seen some rather old articles from 2012 using NDES, but nothing recent.
I've seen other old articles that mention utilising authentication via username and password, but we are looking at device based authentication in the same way as our Windows clients rather than user based.
I'd be grateful for any signpost, information, tit-bit that anyone has to offer as information looks to be scarce!
Thanks!