- Jamf Nation Community
- Products
- Jamf Pro
- Netskope and Big Sur
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Netskope and Big Sur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2020 10:10 AM
Has anyone seen any issues with deploying Netskope on Big Sur with intel Macs? We have tried both with Kext and Network Extensions and the agent is greyed out and the configurations do not appear. Currently have a ticket with Jamf engineering. We are using the latest version of the deployment script but are having no success. Netskope keeps directing using to their support page for the answer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-21-2020 02:29 PM
Yes, we haven't seen a Netskope build yet that fully works on Big Sur. Our configurations appear but the client isn't functioning correctly, on Intel or M1. We have a case open with Netskope on this, it sounds like they are working on an updated build.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-28-2020 10:00 AM
From what our security folks have been telling me is Netskope's current client for Big Sur is a beta client at best. I am assuming it would be even worse for M1 Macs. At least Netskope is consistent with most other security tools for Macs, if you have issues you are on your own.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-28-2020 10:10 AM
I have a meeting with JAMF engineers on Thursday to see if they have any solutions to the issues. I will keep you guys updated to see if that solves anything. Netskope closed my ticket as they keep referring me to the support page where it talks about System Extensions instead of Kext.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-07-2021 07:18 AM
According to JAMF, they do not have the engineering to be able to diagnose the issue either. That its up to Netskope to resolve the issue with client currently.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-07-2021 09:35 AM
Well, why would Jamf give support for a software they hadn't develop? On the other hand, we are using Netskope and even we haven't tested it yet in M1 Macs, we've been successful in deploying version Netskope 81.0.0.530 in Big Sur (which uses System Extensions).
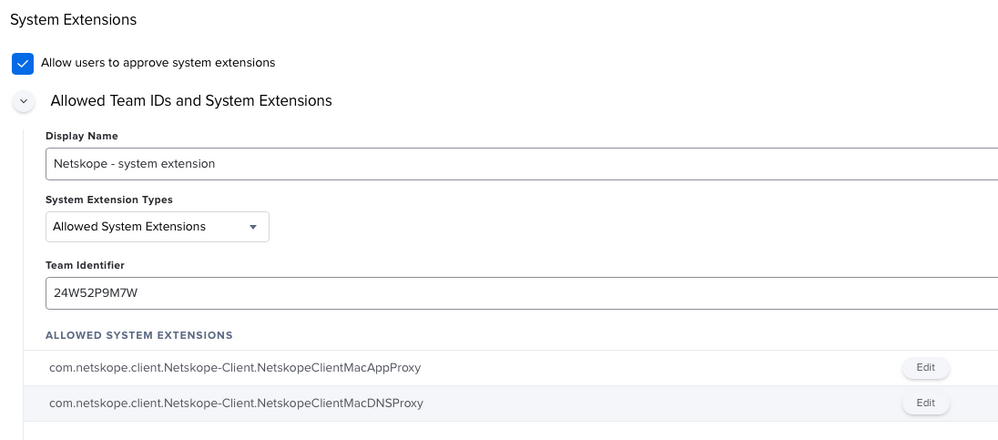
You should deploy a configuration profile allowing the system extensions BEFORE deploying Netskope.
System Extension Configuration Profile as follows:
System Extension Type: Allowed System Extension
Team Identifier: 24W52P9M7W
Allow System Extensions:
com.netskope.client.Netskope-Client.NetskopeClientMacAppProxy
com.netskope.client.Netskope-Client.NetskopeClientMacDNSProxy- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-07-2021 12:37 PM
Echoing what @Phantom5 said, make sure the system extension profile is there before running the Netskope installer.
Also, we had lots of issues with the DNS proxy until we deployed 81.0.1.534. Supposedly the fixes in 81.0.1 will not be auto-deployed until 82.x is released, but we're just installing overtop of the existing version and it is much happier.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-11-2021 01:47 PM
81.0.1.534 fixed all my issues as well. I have tested on an M1 and it works there as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2021 04:23 AM
HI, I am currently facing same issue. It creates a new network interface called VPN connector Also Admin users are able to deactivate by unticking the on the demand as well as admin users are able to delete the netskope client interface in networks. Are you seeing same expect behaviour ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2021 07:09 AM
@kmathern We also have quite a few issues with netskope in our environment. Everything is configured correctly, however the client on macOS is far from bullet proof. To remove the client without turning off the tamper protect you just delete 3 files and dump the daemon which terminal happily does with sudo. In my not so humble opinion NetSkope just another security client that decided to make a half backed macOS version and does not put the investment in it to make it work correctly on macOS.
In the deployment guide I got from NetSkope a few weeks ago it talks about deploying a Per-App VPN client. I dont recall seeing this in earlier versions of the guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-16-2021 09:36 AM
Update on my issues with Netskope or as we call it brokeskope as it breaks everything we try to do. With the client with the VPN installed, we no longer can update Big Sur, it blocks it. I can't use the command line softwareupdate to download new OS versions, it blocks that as well. At this point I got my CISO to agree to remove Netskope from all Macs until they can get us a client that works. Netskope has a ticket open with Apple and they claim that it's Apple doing the blocking and not them. Of course, Apple says it's a Netskope issue so we are stuck in a he said she said scenario. I have a meeting today with Netskope on this matter so I'll update this if there is any notable update from them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-17-2021 07:46 AM
I found out this is a known issue and the team is already working with Apple. We have observed an issue that the upgrade of macOS from versions 11.2.2 or below to versions 11.2.3 or higher is failing when Netskope Client is enabled.
We have already raised a ticket with Apple and Apple has acknowledged that this is a bug addressed in certain subversion of 11.2 and above.
Please use the following workaround to complete the upgrade.
If you are upgrading from macOS versions 11.2.3 and above to the latest version, configure the below processes as certificate pinned exceptions.
1) com.apple.mobilesoftwareupdate.updatebrainservice
2) com.apple.preferences.softwareupdate.remoteservice
3) com.apple.installer.osinstallersetupd
Steps to create a certificate pinned exception:
- From the Netskope tenant navigate to Settings > Security Cloud Platform > Steering configuration > Select the appropriate steering configuration
- Exceptions > Add Exceptions > Certificate pinned applications > +New custom > Select Platform (Mac)
- Enter com.apple.mobilesoftwareupdate.updatebrainservice, com.apple.preferences.softwareupdate.remoteservice under Native processes
- Click on Create
Please let me know if the user is able to upgrade or not after the creation of the certificate pinned exceptions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-06-2021 11:08 AM
still stuck with installation / config issues for my company. We have tried email and UPN methods, using either the v84 or v86 builds, to no practical success. We note the Netskope client does seem to install to our test Macs running Big Sur 11.4, but we also see no config info from the drop down "configuration" menu. The logs don't spell out what is blocking configuration clearly enough. Using a manual method (ie, no MDM) should work, even via our MDM, its no go. We have pre and post installation scripts, correctly chmod'd, and run the sequence via manifest list, which always installs seemingly correct. Its the config portion, somehow the client is not communicating as it should. Any insight would be hugely appreciated!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-08-2021 07:12 AM
@niteboater you may want to start your own thread as this one is kinda old.
We have Netskope v84, MacOS Big Sur 11.4 and UPN mode, no real issues less a poorly configured appliance. We are also domain binding using mobile accounts. Netskope is a beast and there is tons of server side configuration, and that is where most issues lie in my experience.
If it installed correctly you probably need to let whoever owns Netskope get with the vendor on the configuration. Assuming you have the right URL and Tenant as parameters for the script (that Netskope provides) there is not really anything else on the Mac that would go wrong. If you are running the installer manually and still having issues the problem is Netskope not the mac or JAMF. Either your Macs are not setup in a way Netskope can function (not likely) and Netskope needs to help with that. Or there is something wrong with Netskopes configuration. Unfortunately all roads here really point to reaching out to Netskope.
You guys are paying for support with the Netskope client, may as well use it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-15-2021 11:45 AM
thanks AJ - we brought in Netskope and a so-called "expert" and they were no help.
Did you find that you actually had to have the Netskope systemextensions loaded before installing the client? This part is less clear, but some here have said yes...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-11-2021 08:59 AM
Yes all that needs to be in place prior to installation other wise it won't work properly. I have it installing no problem but the issue is when you try to update the macOS with Netskope loaded. The macOS upgrade will fail when it tries to verify the macOS. Netskope says it's Apples fault and Apple claims that 11.2.3 fixes the issue but I've test it on the upgrade to 11.5 and it still does not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2021 04:38 AM
Hi Kmathern,
We had a similar issue our side.
it required updating the PAC File for Netskope to breakout to one of Apples Update Servers.
"api.apple-cloudkit.com", "updates.cdn-apple.com"
Let me know if this helped at all.
We found that user were not even getting prompted for the OS Update.
EG: User was running 11.4.0 and was unable to get 11.5.2. - Just kept saying machine is up to date.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2021 05:03 AM - edited 08-26-2021 05:04 AM
In apples enterprise network guides it recommends bypassing 17.0.0.0/8 which is all assigned to apple. We have Netskope configured to bypass *.apple.com which works "most" of the time. I have had netskope filter the update servers 3 times in the past 2 months. I would not be shocked if the security team is not trying to close that apple domain bypass a bit without telling me.
Netskope is a beast and loves to get in to places you think you have it configured to stay out of. Our security team is having a lot of fun keeping netskope in line lol.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2021 08:07 AM
Thank you we have whitelisted a lot of things so I'll have my Security team check to see if these are included or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-01-2021 01:12 PM
My InfoSec team finally updated the domains and the apple IP scope into the whitelisting for Netskope and my issue with not being able to update is fixed. Not sure if we needed all the domains and the IP to make that happen, hindsight says we should have done it one at a time. But thanks again @VamoozE and @AJPinto for the suggestions. Funny thing is my VPP apps now update and install much better as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-28-2021 01:13 PM
I did a config policy for systemExtensions, you can see below that allows me to install the client however I still cannot get the new macOS updates to work with the netskope client installed and enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2021 08:09 AM
@kmathern I was on a call with netskope last week. Apparently they changed their recommendations and no longer want the DNS proxy extension to be in the configuration profile. They said it was found to cause issues, but did not give any details.
https://docs.netskope.com/en/deploy-netskope-client-with-jamf.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2021 08:15 AM
Thanks,
Karl Mathern
Senior IT Support Specialist – jamf Admin
I'd love to connect… Book time with me!! to make finding time easy.
karl.mathern@coalfire.com
COALFIRE | Coalfire.com| (P) 720-907-053011000 Westmoor Circle | Suite 450 | Westminster | Colorado 80021
[A screenshot of a video game Description automatically generated with medium confidence]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2021 10:13 AM
Yep, I got that link from a call Friday. To keep it simple our netskope implementation is not the best and I have been giving the support team heck and they got me with the vendor friday. Netskope is using an unsigned certificate and Big Sur dont like it. We are looking at other options now like having JAMF deploy the certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-11-2021 06:59 AM
Hey all!! Just wanted to hop in here and update everyone on a few things that have happened. First, I'll state: I'M A NETSKOPE EMPLOYEE 🙂 Now that that's out of the way, we've been GA for Big Sur for some time now. Obviously, this posting I'm responding to is a bit old; the client version is showing 80.x, and we're now on 88.x, so that speaks to the changes/progress version wise. From a JAMF/Big Sur perspective, hop on over to our support portal and check out these articles:
https://docs.netskope.com/en/deploy-netskope-client-with-jamf.html
https://support.netskope.com/hc/en-us/articles/4402657721111-Netskope-Client-on-macOS-11-Big-Sur
The first is specifically to JAMF deployment, per the name. The second is more around the client operation itself. It's no secret: the new architecture of system/network profiles vs kexts has presented some challenges for ALL VENDORS as we adopt to the new way/permissions required to operate successfully, and we've put a lot of time into researching/building/troubleshooting/etc. Most times when issues occur, it's not just one component...it's when two components are both using the network profiles to spin up tunnels (Anyconnect AND Netskope, for instance)...and most of that has been addressed as well. Be sure to follow best practices with VPN clients and interop with Netskope, which can be found on the support portal as well...just query your VPN client, and I can almost guarantee you'll find a config doc for it!
Lastly, please do join the Netskope Community: https://community.netskope.com/
The more members we have, the more that's shared and the stronger/better we all get together!!!
Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-11-2021 08:54 AM
Hi Mark,
I looked at the deployment videos and are you sure you want to set the script to After? I would think that the .plist file would need to be on the Macbook prior to the software installing. Also there is nothing in the videos stating how to setup the system extension for Big Sur and Catalina. you state how to do a KEXT but that is not enough for the two newest macOS's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-13-2022 08:28 AM
To quote Russell in the movie Up... "It's before!"
;^)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-06-2023 08:22 PM
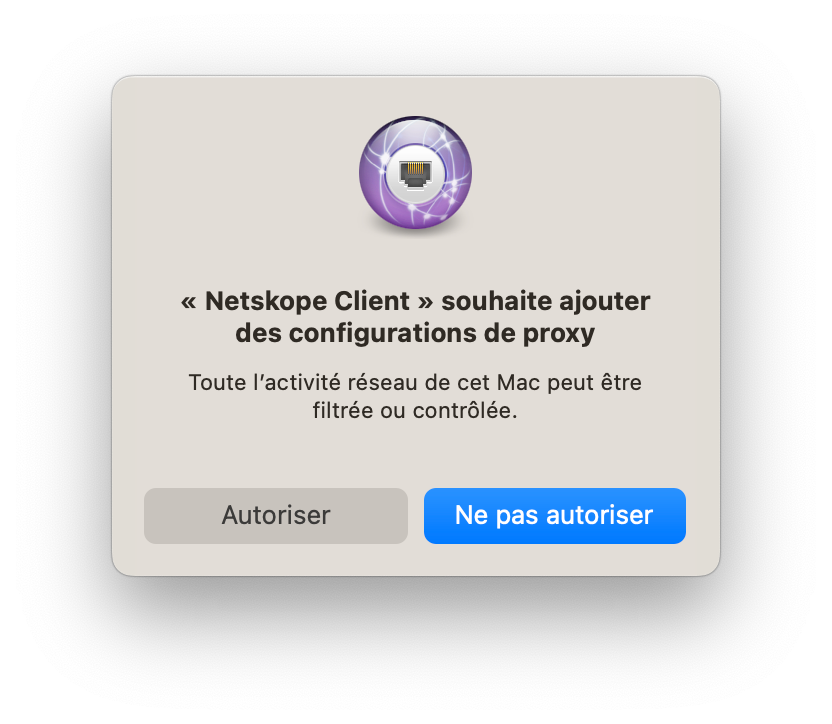
Hi Mark,
I noticed your guide has not been updated for the latest macOS versions and there seems to be no way to avoid the "Netskope Client would like to add proxy configurations" prompt to end users. Can we please have an updated document that is relevant to Ventura?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2022 08:52 AM - edited 07-13-2022 11:02 AM
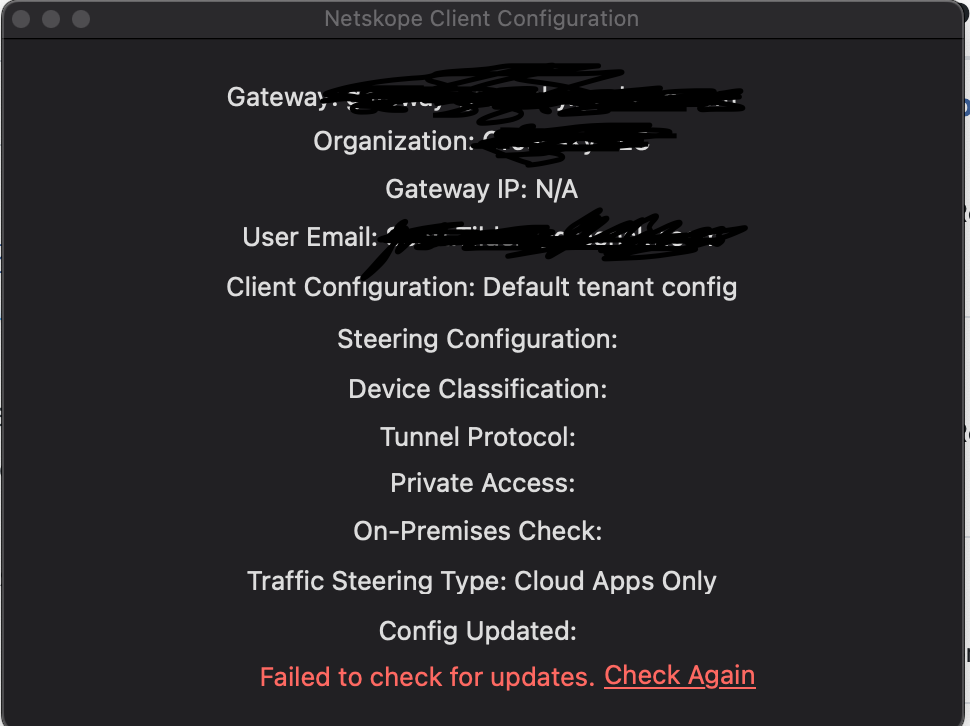
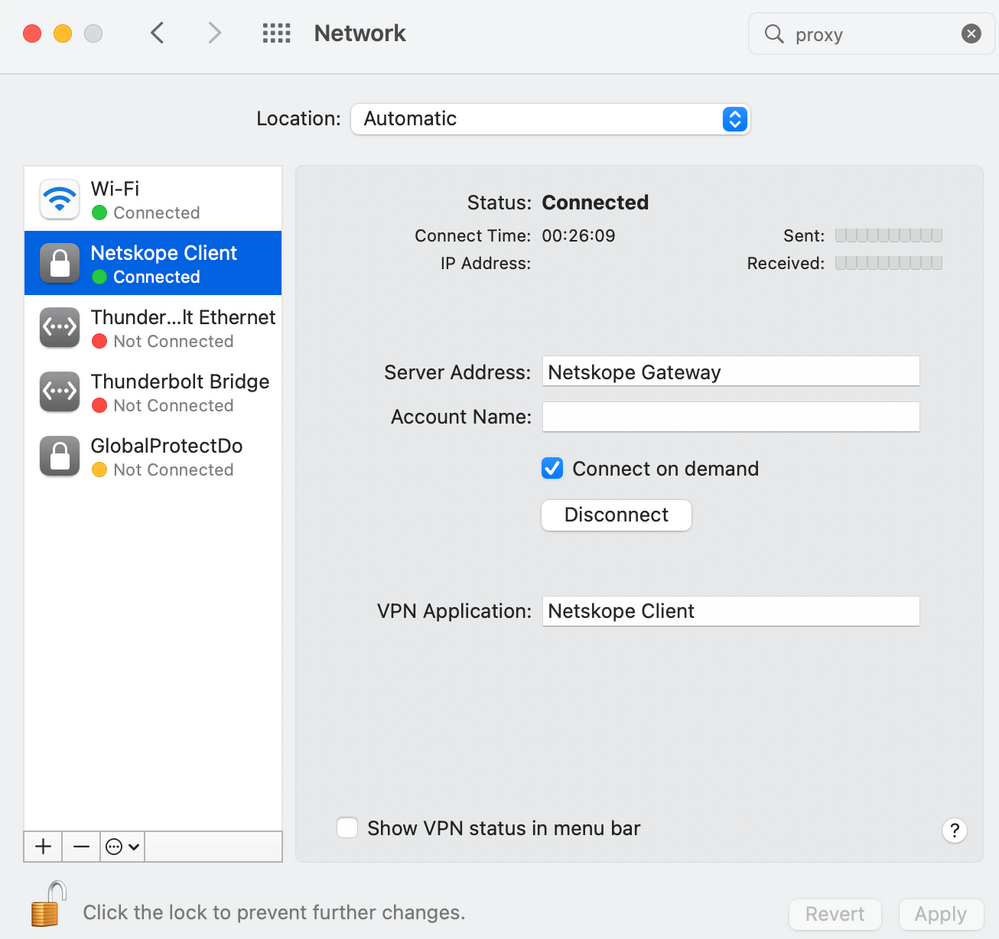
I've been working on deployment of the Netskope Client to macOS 11+ (Big Sur, Monterey, etc) recently.
We're installing v96.0.0.1009 currently, and using a combined Config Profile containing both Approved Kernel Extensions and System Extensions (to cover macOS 10.15+). We use a Smart Computer Group to identify those Macs where the config profile has been installed for scoping the client install Policy (which runs at Recurring Check-in, Once per computer). The install takes place in the background while no user is logged in.
So far this process is working OK for macOS 10.15 Catalina clients, with no prompts to the user at login. On macOS 11+ clients the user is prompted to allow "proxy configurations". This prompt is incessant and will continue to appear until Allow is clicked (no matter how many times you click 'Don't Allow'). Anybody else seeing this? Is there some way to avoid this by deploying the proxy configuration with the config profile? Below is what we see in Sys Prefs, and it is a VPN configuration (but referred to as 'proxy configuration' by the Netskope Client installer).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2023 01:14 AM
Hi @janthenat
I have the same question as you. Did you find the solution to this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2023 05:26 AM
Unfortunately, no... but that's because probably because I have not spent any time on it since that last post. I was really hoping someone else would solve it for me ;^)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2023 05:43 AM
Haha our job makes us become too lazy :P
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2023 05:55 AM
@leobrt @janthenat Do you have a VPN payload in your Netskope Configuration Profile? If not see the "Approve VPN Popup for App Proxy" section in this guide: https://docs.netskope.com/en/netskope-help/traffic-steering/netskope-client/netskope-client-deployme...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-19-2023 06:08 AM
How thank's @sdagley for this valuable information. I had completely omitted this line because it started with "VPN" lol
I will test this !