- Jamf Nation Community
- Products
- Jamf Pro
- Netskope tenant automation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Netskope tenant automation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 10:44 AM
Hey everyone, I recently got passed handling our Netskope deployment. My predecessor claims that with the v71 client, due to us using Azure AD for our IDP we cannot auto populate the tenant information. Basically once the install finishes we get a popup where we have to input our company name.
I know there has to be a way around it, anyone have any familiarity with it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 10:48 AM
Have you gotten your hands on their Jamf deployment script? That has the logic for specifying the tenant and other variables.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 11:07 AM
I haven't yet. Think you can point me in that direction?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 11:08 AM
You will need someone with access to either send you the script from their site, or get yourself access to support.netskope.com.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 01:01 PM
Looks like their scripts are dependent on being AD bound? We will be using Jamf Connect more than likely in the near future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 01:21 PM
No, you don't have to be AD bound. There is a config option to use a profile for "email_from_pref". You would deploy a profile that captures the users email from Jamf using the $email variable, then you specify the location of that variable in the script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2020 03:12 PM
I did our deployment for Netskope. You will need to request for an account from netskope. Once you do that you can get the script and step by step directions to set it up. Below is the link to what I am talking about but you will need to setup an account with them first. Also be aware that the $email will only work once you have their AD connector setup first. It takes a long time for that thing to populate so get with your Netskope installation manager and ask them to get you what you need to get setup.
https://support.netskope.com/hc/en-us/articles/360025614873
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-08-2020 11:33 AM
@kmathern Did you successfully get their installer to work with the $Email parameter? I configured the profile, script, and policy with their support on the line. I can get it to install with a plist that I create local on my machine, but not with the pushed JAMF plist (I uploaded the same plist I used to install locally). I keep getting back "Email address not valid". The Ad importer has been completed and I checked the console and saw my account showed up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-11-2020 12:45 PM
I'm deploying out v72 to my environment now. However, we are bound to AD and I'm using the "peruserconfig" setting. Everything works smoothly for me.
I'm using the vendor's package setup in a policy with a "before" script that puts in all the tenant information. Then, I have an "after" script that runs and modifies the Uninstaller permission settings and moves the uninstaller to a hidden folder. This is to prevent people from uninstalling it - our users currently have Admin rights.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-11-2020 02:34 PM
I found the answer. The Netskope script does not know how to look for com.company.application.plist in the /Library/Managed Preferences. It can only look for application.plist. I have the fix for the script if I want to use the apple naming convention, but want to leave it as Netskope best practices for our deployment. I have asked them to update this to be able to look for com.company.application as it looks cleaner.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2020 10:05 AM
@kevin.dixon Mine does work via jamf deployment, but like I said it only worked after I found out we had to have the AD connector installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2020 10:13 AM
@kevin.dixon I do remember now that you mentioned it, that I worked with their support as well because the params in the script were not getting populated and therefore failing. Netskope support had me just hard code all the variables into the script. They said it's working for us we don't know why it's not working for you. So I will have to change the script itself if I ever need to change it. I don't see that happening so I left it as is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2020 01:39 PM
In the same boat deploying NetSkope client. There appears to be 3 choices:
Use installation parameters to tie the agent to a specific user on the local machine via their AD email address
This hard-codes the machine agent to the specific user. For multi-user machines this might be an issue when deploying policies.
Use params to enable IDP based enrollment so that user gets prompted to login (this is a one time login per user)
If you have multi-user machine this is pretty much the only option
Need Azure AD, OKTA, etc as your IDP
Use $email param from JAMF to tie the client to the email address defined in JAMF for the user
Require machine to be bound to AD. User account on machine must be the AD account. JAMF must be setup to pull in AD info for the user (AD Connector, JIM, etc).
Have asked for feature enhancement to support Kerberos auth so that you can use info form Enterprise Connect / JAMF connect to automate this task.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2020 02:34 PM
We don't use Enterprise Connect, we use NoMAD, but you should be able to grab the AD UPN information from EC I would think. That's how we got around the Netskope crap script. We changed their script to attempt to pull UPN from the NoMAD plist first, then from AD using their dscl call. If unable to grab the UPN from either we do not attempt the install.
You can also verify if the UPN is accepted by Netskope before attempting install:
curl -s "https://<netskopetenanturl>/api/v1/userconfig?token=0cfe04c4237cc33dc7f383af5ddbe2e3&email="${UPN}"&configtype=agent" | grep success
If that returns successful then you can continue on and install the Netskope agent.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2020 05:58 AM
Hi @mlambert
So this broke my heart for the longest time.
1st thing is the machine must have the correct username under the user and location tab in JAMF
Then you deploy a config profile to create a plist which contains the email
{email=$EMAIL}
Then you get the script from Netskope and fill in the variables such as tenant and user the plist to fill the UPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2020 09:36 AM
@taz231190 YEP. not a great process. Also I was never able to get it to install 100% of the time. We were seeing 10% failure rates.
I never got the timing to work with a profile in my enrollment workflow. I had to created the file with the email address at the required location, kinda faking it out.
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-16-2020 06:47 AM
Agreed, would providing option to use signed in username or kerberos id be that much of a hard item for them to support?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-13-2020 03:43 PM
Bump!!
Anyone have Netskope working with Big Sur? The docs say 78 should work but I am seeing PPPC notifications????
Thanks
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-13-2020 04:19 PM
@gachowski I'm still waiting for them to respond to my ticket asking for guidance on how to configure for Big Sur. Their documentation is very vague.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-13-2020 04:37 PM
Thank you sometimes it's good to know you are not the only one!!! I'll open a ticket too!!
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2020 10:15 AM
If you are trying to get Netskope to deploy without AD joining the Mac (i.e. using preference_email in Parameter 7), note that Netskope's instructions are wrong. In the video that walks you through setting up the policy, script, configuration, etc. it tells you to enter the plist file name without the extension into Parameter 6 when adding the script to the policy, which is the same way you enter the preference domain in the configuration. However, within the policy when defining the name of the plist in Parameter 6 you MUST include the .plist extension. If you don't, the script will exit with an error trying to find the plist file and then deploy Netskope in IDP mode as a fallback. This is the script result:
Script result: Installation is configured with preference_email Param1 / Param2 [COMPUTER NAME] Param3 [USERNAME] All Logged in user names: [USERNAME] Logged in user name: [USERNAME] User name is [USERNAME] length [#] User name is [USERNAME] length [#] Going to remove IdP config file Tenant url is [TENANT].goskope.com restAPIToken is [API_TOKEN] email pref file path /Library/Managed Preferences/template /Library/Managed Preferences/template not found, exiting installation process
As you can see in the script result, it takes the entire value in Parameter 6 and looks for it within Managed Preferences. This is where the plist file you uploaded in the configuration is stored. So by changing the value to template.plist (or whatever you named your plist) will get the script to find the file correctly.
After I changed the value and appended .plist in the script parameters for the policy, it deployed perfectly without us having the AD connector installed. We really didn't want to have to add the AD connector just to deploy Netskope.
I've contacted our organization's Technical Success Manager at Netskope to let them know to update their documentation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2020 11:21 AM
I can confirm that we also specify with the .plist. I don't remember if I read their docs close enough to try without .plist. ;-)
Been using this setting for a while now.
The problem I have, is if the email does not exist in netskope (for various reasons), it falls back to IDP mode and displays a window asking for tenant and can't be closed by the user. I'm trying to get them to fix this before pushing any updates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2020 11:36 AM
@patgmac Are you seeing the prompt when the Netskope tenant doesn't recognize the email, or when no email exists to be written to the .plist in the Managed Preferences folder? The latter was my problem.
My solution to avoid getting the Netskope configuration prompt was to have a Smart Group that checked for a non-Null email address which was used as a Scope Exclusion for our Netskope Configuration Profile. Then an EA was created to verify an email address is present in the .plist created by the Applications & Custom Settings payload of the that profile. A second Smart Group based on that EA is used as the Scope Target for the policy that deploys the Netskope agent. That ensures when the netskope agent is installed something is present for it to use as the configuration email address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2020 12:45 PM
@patgmac their docs are terrible anyway, very thin. They mention towards the end to add the plist, but that's literally the only thing they mention about the plist. They never say one has to be created to begin with or added to a configuration, unless you sit through the 7 minute video where it finally gives you some context. And even then it's annoying that since it's a video you can't copy and paste things like the ID for the KEXT or the example command they give to create the template plist.
Anyway I'm just glad we got it working. It's one of the bigger reasons we switched to Jamf, with regards to endpoint management pain points we had in our specific environment. Now I just need to figure out if we want to use Okta SAML for self-service enrollment or the LDAP interface from Okta. Depends on if SAML populates the email field, which I think LDAP brings over attributes and SAML only brings their username. But in our case username = email, so if we can figure out a way to fill that attribute in we'd stick with SAML.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-28-2020 02:05 PM
@GaleForce You can bring in any LDAP attribute as an Extension Attribute. Just create an EA and choose "LDAP Attribute Mapping" from the Input Type popup. After the EA is created you'll see a text field on the EA page listing the LDAP Attribute Variable (e.g. $EXTENSIONATTRIBUTE_104).
Once you have that variable you can use it in a Configuration Profile Applications & Custom Settings payload to write the attribute to your plist. The payload for my com.myorg.netskopeconfig domain has {email=$EXTENSIONATTRIBUTE_104} as the plist data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2020 09:00 AM
has anyone had success getting the new System Extensions for Netskope whitelisted via Config Profile on v78 in Big Sur?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2020 10:07 AM
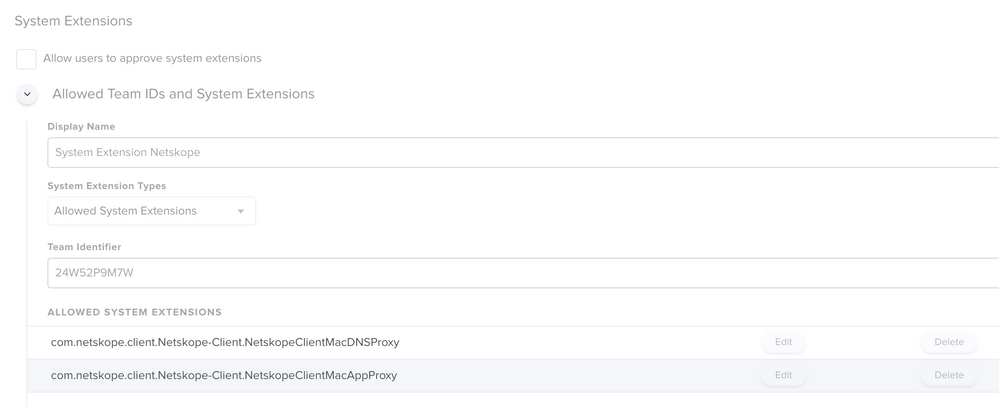
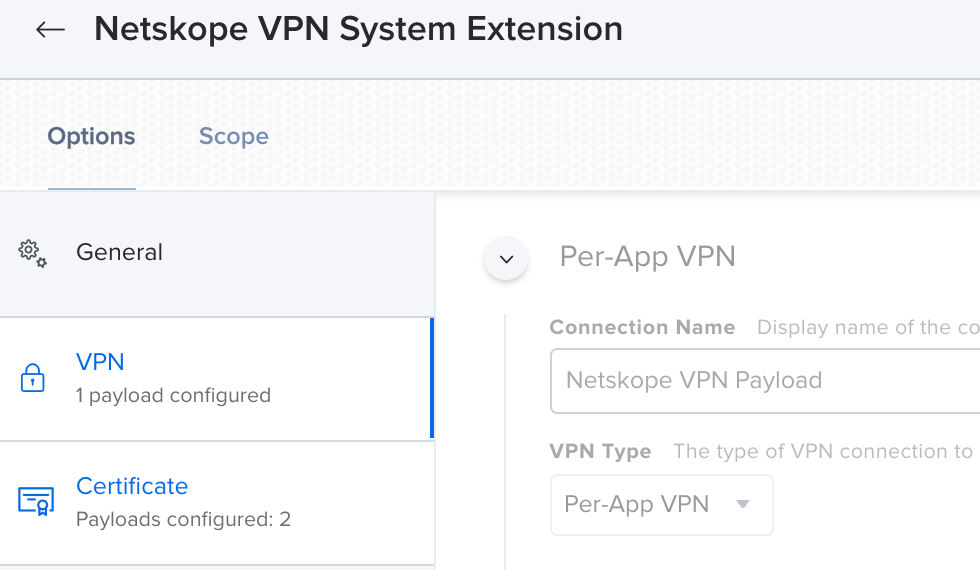
@mapurcel I haven't dealt with the Netskope System Extensions yet, but be aware that unlike Kernel Extensions you will need to provide both the Team Identifier and the System Extension bundle ID as Team Identifier alone is not sufficient for System Extensions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2020 10:57 AM
I've been testing on Big Sur and Netskope v78 with the following profile and it doesn't appear to allow the System Extensions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-29-2020 05:52 PM
Ok I got it working sort of thank to @sdagley and @mapurcel I had tried System Extensions in an early build of NS and Big Sur and it didn't work so I tried again ... NS V78.3.0.523 and Big Sur beta 9. that said there is still a pops up that asks the user to allow the VPN/Proxy. However, if you don't interact with the pops ups and the machine reboot NS will phone home and download the current version you NS tenant is pushing our is V90
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2020 08:27 AM
@patgmac Are you seeing the prompt when the Netskope tenant doesn't recognize the email, or when no email exists to be written to the .plist in the Managed Preferences folder? The latter was my problem.
Could be either. I don't think I've seen that email field be blank, but I have had instances where the profile didn't install so it had the same result.
Everyone else trying to get this working with Big Sur....I put Netskope engineering in touch with someone at Apple to help them learn what needs to be done to get their product working in BS. That person at Apple built them a couple sample profiles. One for SysExt's, and one for AppProxy VPN, takes care of all the prompts/approvals. I'm not sure if Netskope has made these profiles available yet, but wouldn't hurt to ask. Or ping me on Slack and I'll send them to you. (@patgmac)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2020 08:31 AM
I believe we will need to deploy a Web Content Filter payload alongside the System Extension profile but Netskope hasn't provided details around that and that payload isn't available in Jamf yet so it has to be a custom configuration profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-30-2020 02:40 PM
I was able to test some more today and even if the user selects "don't allow" the VPN/Proxy" pop ups, NS will install them after a reboot. And the reboot is required for FileVault so :) on to the next Big Sur issue.
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-15-2021 06:51 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-15-2021 06:54 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-15-2021 07:06 AM
I do not recall. I believe it was from Netskope directly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-22-2021 02:49 PM
Looks like we still need a Web Content Filter payload in order to get past the "Netskope Client would like to add proxy configurations" prompt. Anyone hear from Netskope about the details required for that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-25-2021 12:49 AM
we dont deploy WCF for NS, only for Cisco AC for big sur and havent had issues so far.
only thing I needed to deploy aside from KEXT and SE was the VPN payload and the proper certs.
From their guide
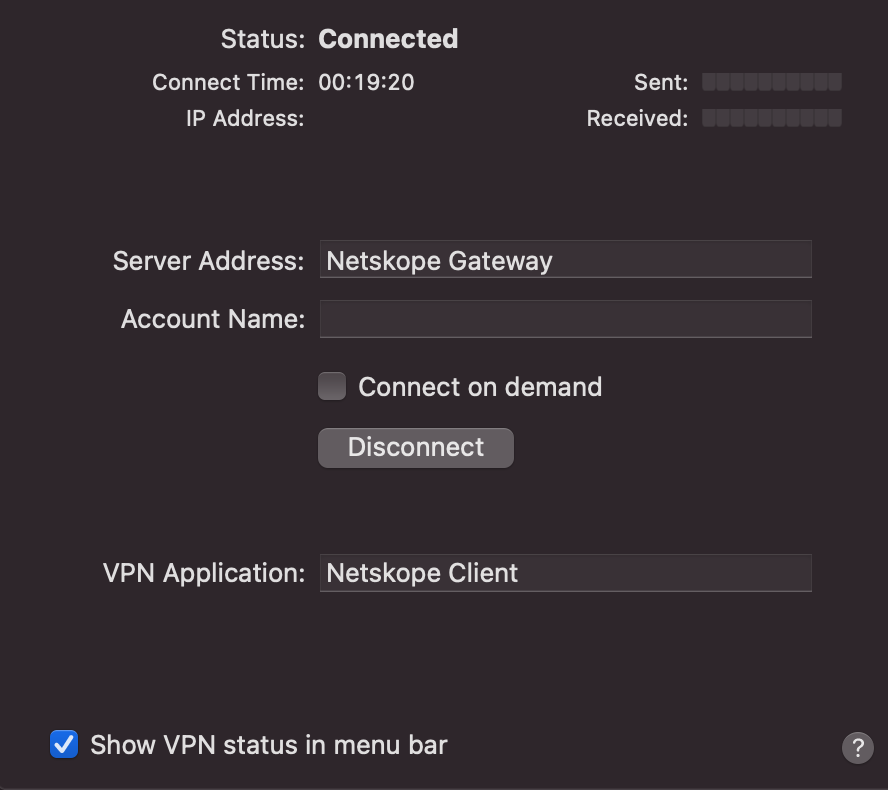
Configuration Profile for Auto Approval of VPN Payload (only for BigSur OS)
Go to Computers > Configuration Profiles > General
Click the Edit button. Under the Options section, select VPN and configure the following:
VPN Type : Select Per-App VPN
Per-App VPN Connection Type: Select Custom SSL
Identifier: Enter : com.netskope.client.Netskope-Client
Server: Enter Netskope Gateway i.e., gateway-<tenantURL>.
Provider Bundle Identifier: Enter com.netskope.client.Netskope-Client
Provider Type: Select App-Proxy
Select Include All Networks
Specify Provider Designated Requirement: Enter anchor apple generic and identifier "com.netskope.client.Netskope-Client" and (certificate leaf[field.1.2.840.113635.100.6.1.9] / exists / or certificate 1[field.1.2.840.113635.100.6.2.6] / exists / and certificate leaf[field.1.2.840.113635.100.6.1.13] / exists / and certificate leaf[subject.OU] = "24W52P9M7W")
Select Prohibit users from disabling on-demand VPN settings
Push Netskope Root and Tenant Certificates
Before you can push the root and tenant certificates, ensure that you do the following:
Download root and tenant certificates from Netskope MDM distribution page.
Login to Netskope WebUI with admin credentials.
Go to Settings > Security Cloud Platform > MDM Distribution. The certificate download options are displayed in the Certificate Setup section.
Convert the downloaded certificates to .cer format.
To push certificate via JAMF, login to JAMF admin console and do the following:
Go to Computer > Configuration Profile > New.
Under Options, give a name to this profile.
Select Certificate > Configure
Enter a name for the certificates.
Select Upload to upload the converted root and tenant certificates.
In the Scope tab, select the target computers.
Click the Save button.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-09-2021 03:37 AM
HI @ beeboo
How do I add VPN application : Netskope Client
I am trying to replicate the proxy setting that Netskope pushes to the computer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-10-2021 08:48 AM
@user-NOQkvCrTvc see my post above yours, those are the exact steps from their support portal.
it needs to be deployed as a config profile alongside the 2 certs from NS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-02-2021 12:40 PM
Hi all, sorry for bringing up an old conversation again but we have successfully pushed out Netskope v.86.0.8 and have gotten around to auto approving the extension/proxy prompt but I cannot seem to get the tenant id to autofill. We are using the JAMF provided script. Does anyone know if and where we can modify the script to auto-fill in the tenant ID? I don't have very much scripting knowledge so I do apologize if this question sounds dumb or does anyone know of another method within JAMF to accomplish this? Thanks in advance.