- Jamf Nation Community
- Products
- Jamf Pro
- System Extensions blocked after upgrading to High ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
System Extensions blocked after upgrading to High Sierra 10.13.4
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 03:10 AM
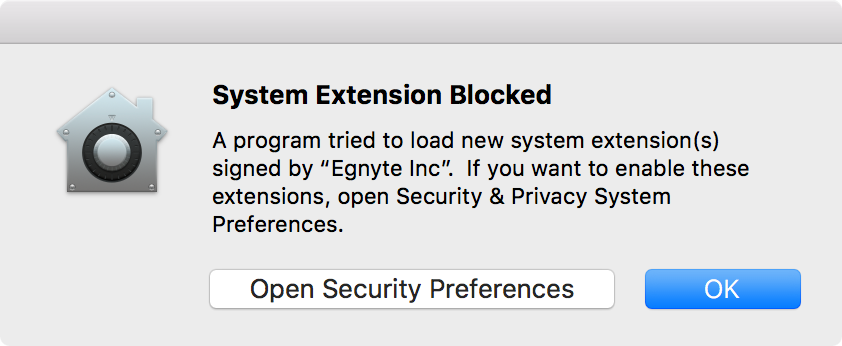
After upgrading both of my Macs to High Sierra 10.13.4, I was greeted by several alerts saying that an extension was blocked. OK. Fine. I knew this was coming. The problem for me was that when I went to the Security & Privacy preference pane, and clicked the Allow button, nothing happened. I tried logging out and logging back in, and rebooting. Neither worked. I then logged into a different admin account, and I was able to allow the extensions. I just wanted to pass this on in case anyone else runs into this issue. I haven't figured out exactly why my normal login account could not approve the extensions, but at least the solution was easy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 07:45 AM
We are seeing the same thing with System Center Endpoint Protection. The account needs to be changed over to another admin and allow the extension. Kind of a big deal.It looks like we'll be blocking this update until there is a permanent fix
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 07:50 AM
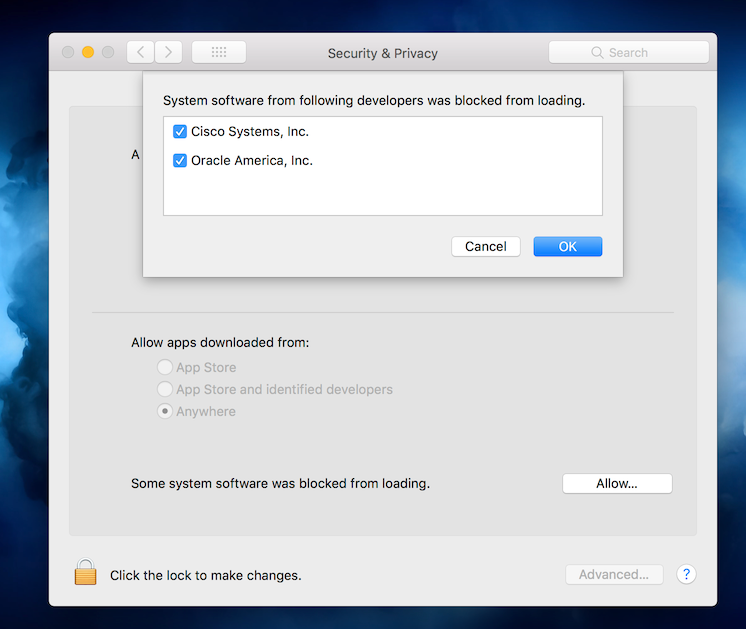
I saw this warning after a reboot for these (2) third-party resources
-Oracle (Java)
-Cisco (AMP)
This approval UI is only present in the Security & Privacy preferences pane for 30 minutes after the alert. Until the user approves the KEXT, future load attempts will cause the approval UI to reappear but will not trigger another user alert.
For clarification, is /usr/sbin/spctl the command to enable/disable them from command line?
Supposedly If a Mac is enrolled with an MDM solution, the new kernel extension authorization behavior is disabled. But on my test Macs (enrolled in Jamf - version 9.99) I was prompted (See screenshot above), which surprised me. Is this behavior expected on managed Macs? Should users be seeing this warning message?
Looks like @RobertHammen clarifies some of these topics in his post https://goo.gl/oHWUQQ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 08:05 AM
As a temporary measure, I created a policy to ignore the 10.13.4 update.
Files and Processes -> Execute Command:
softwareupdate --ignore "macOS High Sierra 10.13.4 Update"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 08:16 AM
I did more testing, and I was able to allow the extensions on a test system. My case seems to be an isolated one, and not the norm.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 08:43 AM
@howie_isaacks Can you expand on how you did it? Is the allowance controlled via script/policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 09:30 AM
I agree with @dstranathan. It'd be great to know what you did @howie_isaacks. Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 09:50 AM
Sorry @dstranathan nothing that fancy. I simply upgraded one of my Mac VMs to 10.13.4, and then installed something that I knew would get blocked. My reason for starting this thread was partly a warning that users may not be able to allow the extensions. I wasn't sure at the time whether my personal situation was going to be seen with other people. I'm happy that's not going to be the case. I also wanted to let others know that logging in as another admin account was the solution if someone cannot get the extensions approved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 10:21 AM
A fun thing to know. If your trying to clear the message in Security & Privacy. You will not be able to click on the button from a remote session. You must do it at the computer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 10:27 AM
I saw this coming as part of the 10.13.4 beta, so I sent out an ignore command earlier in the week to block this update until I get our JSS upgraded to 10.2.2 so it can support MDM-based whitelisting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 10:30 AM
@ssmurphy We are seeing it on the machine as well when you attempt to do it via the currently logged in user. Switching accounts fixes it, but if you have a few thousand machines in your fleet that is a bit of a headache.
Going over some of the documentation regarding the change, I saw this:
For workflows that leverage mobile device management (MDM), all systems with a valid MDM profile installed will not require user approval to load any properly-signed kernel extension.
And Jamfs press release for 10.3 states this:
The 10.13.4 release of macOS introduces a new level of management capabilities for Mac, known as “User-Approved MDM." As the name suggests, this implies the user has willingly enrolled their Mac into management. New security-sensitive MDM controls now require User-Approved MDM. This is similar to how supervision works on iOS, but is not actually called supervision for the Mac. Existing Macs enrolled prior to 10.13.4 in MDM will automatically be considered "User Approved." Any DEP enrollments are also "User Approved." Automatically create User-Approved MDM enrollments through the new enrollment workflow in Jamf. This allows IT to remotely manage security-sensitive settings like User-Approved Secure Kernel Extension Loading. New profiles, like Approved Kernel Extensions, require a macOS enrollment to be User Approved.
Is anyone that is seeing these blocked kernel extensions running 10.3 yet? It looks like a config profile needs to created whitelisting the Team ID and Bundle ID in 10.3 per the aforementioned @RobertHammen post here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 10:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 11:08 AM
I've tested this on 10.2.2 and the 10.13.4 beta, and the whitelist worked as the native MDM payload for the kernel extension policy. I was not able to get it to work with a custom MDM payload on 9.101.4, so we're finally upgrading to 10.2.2 for this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 11:09 AM
Another nice thing in 10.3.0 is the Approved Profile reporting.
Note: When you view the results of an advanced search or a smart group, the inventory information returns "Unsupported OS Version" for computers with macOS 10.13.1 or earlier
I'm amazed that (not really) even after giving explicit instructions to our non-DEP clients, about 50% have not approved their Profile...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-30-2018 12:50 PM
If you don't have 10.3.0 and can't tell if the MDM profile is approved, you can always use kextstat to look for your critical kexts and nag the user if they aren't loaded.
With 10.3.0, I'll use that attribute to perform my own "conditional access" and deny access to all Self Service policies unless a user approves their MDM. I hate to use a carrot like a stick, but Apple leaves us few options since even DEP can't be forced.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2018 12:29 PM
After approving the extension for Google Drive File Stream, I had to quit and re-open the GDFS app before it would work normally.
If there aren't going to be programmatic means to handle these extension requests, I'm going to have to change strategy on a number of items.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2018 11:02 AM
I've also run into this kext approval after updating my iMac to 10.13.4. It was enrolled prior to update via DEP so I'm concerned that anyone updating is going to be running into this regardless of their MDM enrollment status/method.
We are currently on 9.101 and so can't use any configurations regarding kext but will begin playing with these in prep for our upgrade to 10.3 in a couple weeks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2018 12:37 PM
To summarize what others have said:
- The latest version of High Sierra won't automatically load any Kernel Extensions.
- A user has 30 minutes to accept the request, or the extension is not loaded.
- Restarting the Mac should bring up the prompt again.
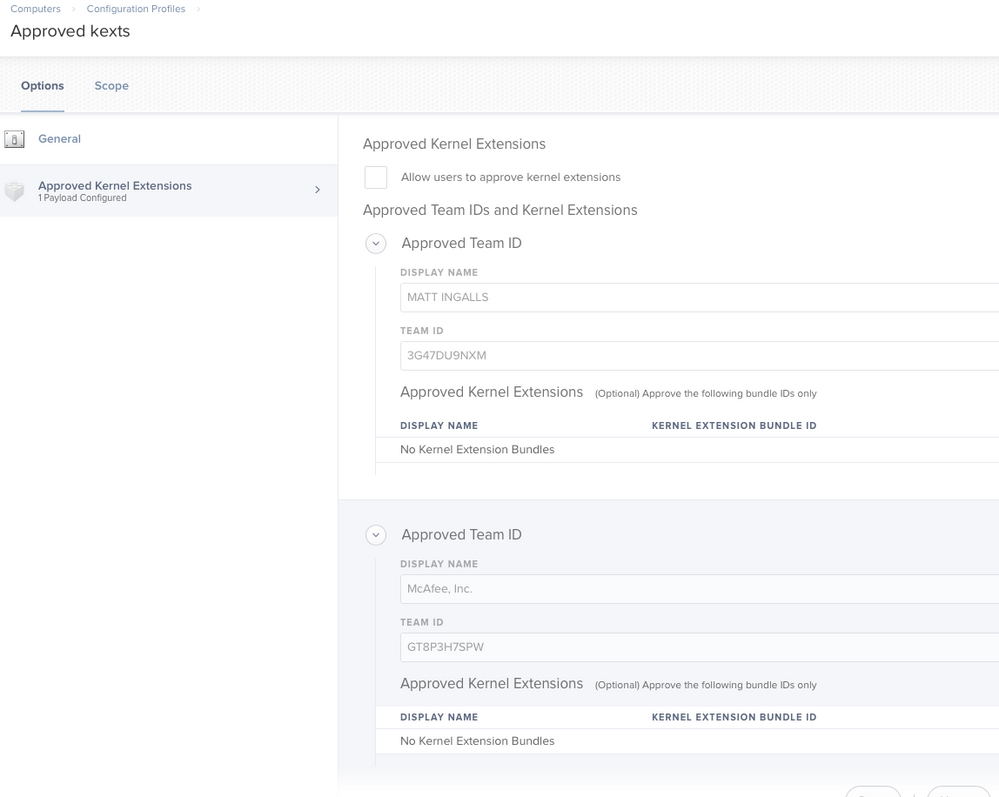
- To bypass this limitation without disabling SIP, a new configuration profile is needed.
- The configuration profile must include a whitelist of "Team" IDs (unique per Apple Developer account)
- To find the team ID, you need to run a sqlite3 on a computer that has the KEXT installed.
- The configuration profile payload was introduced in Jamf Pro 10.2+
To get the Team IDs, read the first half of this post by @grahamgilbert : Enabling Kernel Extensions in High Sierra. Stop reading at "csrutil" because you should be using a Configuration Profile if this is being deployed to more than a handful of systems.
It is NOT necessary to have DEP to use this feature. Using DEP gives you supervision (non-removable MDM) and bypasses the "user approval" for the MDM profile, but if your MDM is already approved (either manually, or because the system was grandfathered in during an upgrade), then just add the Configuration Profile from Jamf Pro and be on your merry way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-05-2018 10:32 AM
Here the link to see exactly how to get the team ID through Sqlite
https://pikeralpha.wordpress.com/2017/08/29/user-approved-kernel-extension-loading/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-05-2018 05:43 PM
Ditto. A bunch of users observing the message with Sophos (Central).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-06-2018 09:17 AM
After re-reading the release notes, it looks like Apple intentionally decided not to automatically approve kernel extensions on MDM enrolled systems:
•No longer disables User Approved Kernel Extension Loading on MDM-enrolled devices. For devices with DEP-initiated or User Approved MDM enrollment, administrators can use the Kernel Extension Policy payload.
As @bradtchapman noted, it is time to start using the configuration profiles AND time to upgrade Jamf servers to 10 to do this (we are upgrading next weekend).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-08-2018 12:28 PM
Thanks for the post @bradtchapman I followed the steps and I have five extensions that are now automatically approved. If I could give you a million likes for this, I would!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-08-2018 01:02 PM
@howie_isaacks : you're welcome! Glad to be of service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-09-2018 08:24 AM
Hey guys-
Been quite some time since I've been round these parts. I've moved over to Carbon Black and we're helping customers through this one. If you use a Cb product, feel free to reach out to me and I'll see what I can do. This one's taken some of us by a bit of surprise as well and I know some of y'all deal with our kexts.
<first initial><lastname> @ carbon black <dot> c0m
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-09-2018 11:51 AM
@BradChapman. Nice to see your post here. We will have to upgrade to JAMFPRO 10 I see with this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-09-2018 11:58 AM
Cool! today we got our official GO within our organisation to move over to Carbon Black Defense :) So moving out from pilot phase to all clients (in batches) and yeah we saw on the 10.13.4 pilot users the CBD Sensor got stucks "Bypass" because of the KEXT not approved.
So, created a configuration profile, and couple of secs later it all went fine and the sensor went active again :)
ps. please share to add the feature to run a full scan on a client via CBD, would be awesome!
Cheers,
Thijs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-10-2018 06:34 AM
I used the instructions here to get the Team ID, then I built a Config profile specifically for pre-approving kexts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-04-2018 11:29 AM
here is the apple article about this
https://developer.apple.com/library/content/technotes/tn2459/_index.html
I have had to do this for Cisco, Carbon black, and Now Forescout Secure Conenctor.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-18-2018 05:45 AM
To tag on to what @AVmcclint stated, you can just download this python script to list the Team ID's if you don't want to do completely manually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-25-2018 01:08 PM
I am not on Jamf 10 yet. Question is can I create a custom config profile manually and deploy it via policy/script to my 10.13 clients?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-31-2018 03:54 AM
@wmateo You can in theory do it in J9.9 by creating a custom setting in Config profiles and import a pre-made kext list (By using Franton's script https://www.jamf.com/jamf-nation/discussions/26583/kextpocalyse-2-the-remediation-blog-post-by-our-own-franton).
If you want to add them manually you'll need to upgrade to Jamf 10 which provides you with the "Approved Kernel Extensions" option.
Keep in mind that the approved kext list needs to be installed before the apps that require them so might need some re-arrangement in in smart groups and policy's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-03-2018 01:16 PM
I have a bundle_id without a team_id.
Using @AVmcclint 's post on this thread, as well as @donmontalvo's post for quidance, I get the following result:
6HB5Y2QTA3 | com.hp.kext.io.enabler.compound | Hewlett Packard | (blah blah blah...)
| com.ni.Fantom.nxtFwdl | 1 | Legacy Developer: N1 | 1
It's for the LEGO Mindstorm NXT software, which is old.
JAMF requires a team_id be input, and I cannot leave it blank. Does anyone have any thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-03-2018 04:01 PM
@costes try: SKTKK2QZ74
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-07-2018 10:26 AM
@scottb How'd you come across SKTKK2QZ74? I'll throw it on some test units
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-07-2018 03:40 PM
@costes Pulled from an install. I also verified it on the google doc. Once I reimage a Mac in my downtime, I'll test it too for kicks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-08-2018 11:27 PM
Somebody is nice enough to compile this into one spreadsheet. Link of known Team IDs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-09-2018 03:36 AM
@khey Thanks for this, bookmarked!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-10-2018 01:31 PM
@scottb and @khey thank you for the resources.
I entered SKTKK2QZ74 as my missing Team_ID in my Config Profile and redeployed to affected devices.
HOWEVER I am getting the same symptom now as @howie_isaacks original post. I'll still get the pop up in regards to the specific KEXT for com.ni.Fantom.nxtFwdl, and nothing happens when clicking Allow. Redeploying the Config Profile did not resolve the issue either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-15-2018 01:24 PM
Any updates on this situation? Also trying to install Lego Mindstorms NXT with the missing Team_ID. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-16-2018 09:53 AM
@Costes, is the Profile loaded on the Mac before you install the package?
Are you using ONLY the TEAM ID?