- Jamf Nation Community
- Products
- Jamf Pro
- Re: What scripts and helpdesk tools do you use wit...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
What scripts and helpdesk tools do you use with self service?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-31-2019 02:54 AM
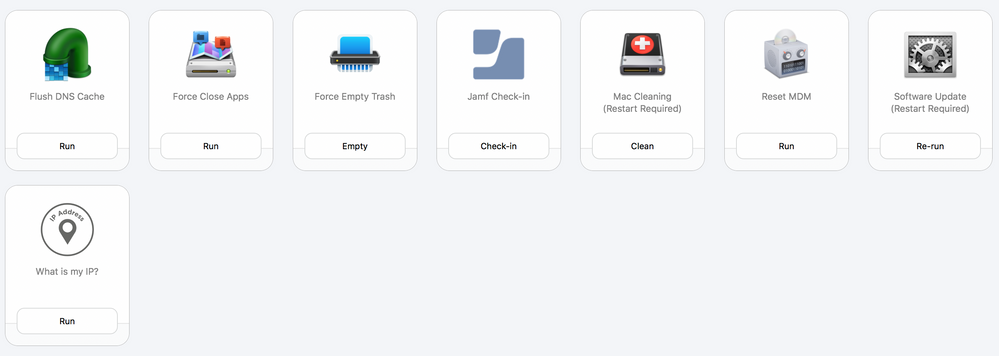
Hi everyone! I've been slowly building out our self service with software from VPP, scripts for updating and some help desk tools.
I was hoping you all could share some of the scripts and other tools you use for your users. There have been some older threads showing off their tools but they are a little sparse on how to make them work. One great one I saw, but have no idea how to get it to work, was an emergency backup to Google Drive.
I would love to see some scripts for updating Adobe CC and some other nifty scripts for helpdesk. Attached is what I have so far.
Cheers everyone! :)
- Labels:
-
Self Service (macOS)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2019 06:09 AM
Thank you @bergmire
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2019 08:00 AM
@neilrooney @bergmire posted the exact script we use. I essentially wanted to replicate going into the Printers & Scanners preference pane and right-clicking to 'reset printing system'. One call-out is that when a user clicks to reset the printing system in Self Service we force them to read the card that tells them that this will blow out all their printers and they will need to re-add them.
Similarly, any of these options we have that require a restart (Optimize My Mac, Flush Font Caches, etc) we force the user to read the card telling them clicking will restart their machine and they should first save any work, quit apps, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-07-2019 10:14 AM
Thanks, @bergmire for that. However, I wonder (and have for years and never got an answer, even from our Apple guys - what exactly does the "Reset printing system..." do? And how do we replicate this in total? It may very well be doing what your script does and just sounds fancier, but I still wonder...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-13-2019 05:24 AM
Thanks @jr139 , this has been a great source of inspiration for my SSP. I hope we can keep it going.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-19-2019 09:22 AM
I'm seeing a lot of screenshots, but not a lot of scripts... can anyone share scripts along with their screenshot so those of us that are new get an idea on how it all works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-19-2019 12:38 PM
Agreed with @bjhobbs as I'm still learning myself and would love to tap into any GitHub pages, etc. that you guys use or see some scripts posted here.
Also thank you all for the brilliant ideas, scripts and approaches to using self service like this!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-19-2019 01:32 PM
These are all great ideas on how to improve and use self service. I would like to echo other comments here and ask if there could be a repo somewhere where these ideas could be captured and stored for others to follow.
I am thinking of a visual page somewhere, perhaps, a click on any one of these items and it takes you to a site that shares the code or script that makes that piece work? Maybe this is a feature request from Jamf to collectively gather these things?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-26-2019 06:52 AM
Seems like a good use of a new Jamf Marketplace category?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2019 11:30 AM
@neilrooney This is a great thread and I even found some ideas to update some of our options as well!
Question about access: how are you limiting access to some of these policies only to your helpdesk team? Or are all these policies available to any user that open Self Service?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2019 01:17 PM
@kevinwilemon If your Helpdesk team members are in AD, and assigned to a Helpdesk specific security group, you can use that as a Limitation when scoping Self Service policies you only want available to them. Specifically as an "LDAP User Groups" Limitation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2019 02:01 PM
Thanks, @sdagley . No AD here (should have mentioned) so I'm always curious if anyone has gotten this working with JAMF users. It works as it should in regards to displaying the appropriate policies when our Helpdesk log into Self Service, but policies don't actually run displaying "This item is no longer available" and refreshing. When not limited to JAMF users, the policies run fine.
We've a standing ticket open with JAMF about it, but thought I'd ask in case anyone has that function working without AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2019 06:47 PM
@kevinwilemon How do your Helpdesk folks log in to Self Service if there's no directory system for them to authenticate against? For policies that display the "This item is no longer available" message, have you looked in the policy log to see if anything was logged regarding the attempt to run? I've seen that behavior on policies that have actually run, and have a inventory update at the end of the policy so they go out of scope at the completion of the policy, which causes Self Service to display that message.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2019 07:04 PM
@sdagley We don't currently do this due to the "no longer found" issue, but JAMF does allow Self Service login outside of AD. If you look under All Settings >> Self Service >> macOS >> Login, you can set the Authentication type to either "Single Sign On" or "LDAP account or Jamf Pro user account" so we would have them login with their JAMF accounts.
For the "no longer found" issue, support confirmed it's an issue with the JAMF user login not working properly. It displays the correct policies, but the feature itself isn't working as expected in that they don't actually action.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2019 12:22 PM
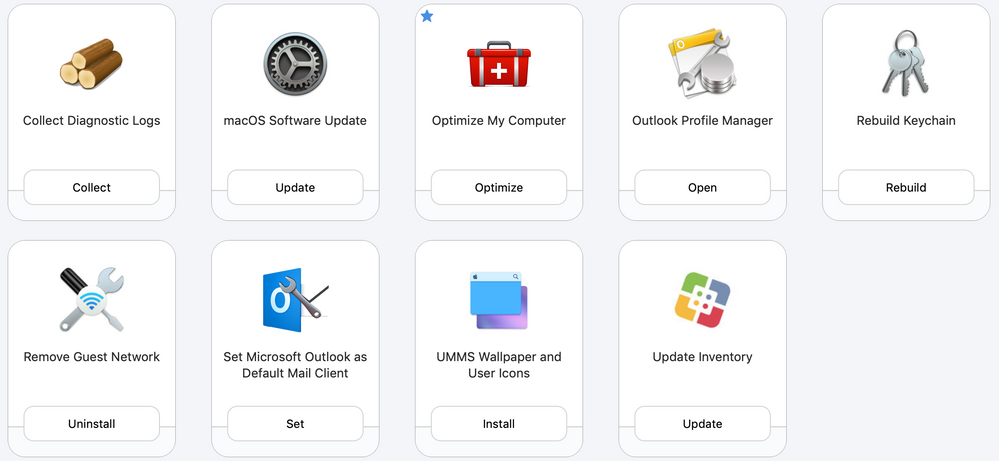
Here are our tools scoped to everyone:
When a tech signs in, they get access to McAfee Uninstall Script, Office Uninstall Script, Adobe Uninstall Script, Spotlight rebuild, Remove Office license and a few more.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2019 06:51 PM
@hrhnick Can you share with us your Rebuild Keychain script? Does it fix the issue with password resets with computers bind to AD?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2019 07:02 PM
@emily can you share your remove Wifi script?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2019 09:19 PM
it’s very crude. we don’t bind to AD, so it literally warns the user what it’s gonna do, renames the old keychain folder in case we need to undo, then prompts a logout which regenerates a new keychain. If you look on github, I’ve seen some more advanced scripts that do what you seek.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-20-2019 09:56 AM
I'm still using https://github.com/jmahlman/uarts-scripts/blob/master/Adobe-RUMWithProgress-jamfhelper.sh for my Adobe CC updater. It's a little finicky, but still worthwhile to keep everyone directed to the "Self Service does it all for you" ethos (myth?).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2019 08:39 AM
@wildfrog Can you share your Set Outlook as Default script/policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2019 03:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2019 05:10 AM
This is an awesome post, but I have to agree that the screen shots are giving me great ideas that are not going to be implemented without access to the scripts. If these are being pulled from github, could you just share the links instead of posting a bunch of scripts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2019 11:49 AM
@ammonsc This is what I use for Outlook as the default. If you run this with a user that's been in place for awhile it could mess up their outlook plist. but we run this as part of our new computer setup.
#!/bin/bash
# It's meant to be run immediately after a user logs in for the first time.
# pulled from https://www.jamf.com/jamf-nation/discussions/6845/sharing-a-script-set-outlook-as-default-email-contacts-calendar-app
plistbuddy="/usr/libexec/PlistBuddy"
USER=$(/bin/ls -l /dev/console | /usr/bin/awk '{print $3}')
launchServicesSecure="/Users/$USER/Library/Preferences/com.apple.LaunchServices/com.apple.launchservices.secure.plist"
PLIST_ENTRIES=$(/usr/bin/defaults read $launchServicesSecure | /usr/bin/grep LSHandlerPreferred | /usr/bin/wc -l | /usr/bin/sed 's/ //g')
if [ "$PLIST_ENTRIES" = "0" ]; then
ONE="0"
TWO="1"
THREE="2"
FOUR="3"
FIVE="4"
SIX="5"
else
ONE=$(/bin/echo $(($PLIST_ENTRIES+1)))
TWO=$(/bin/echo $(($PLIST_ENTRIES+2)))
THREE=$(/bin/echo $(($PLIST_ENTRIES+3)))
FOUR=$(/bin/echo $(($PLIST_ENTRIES+4)))
FIVE=$(/bin/echo $(($PLIST_ENTRIES+5)))
SIX=$(/bin/echo $(($PLIST_ENTRIES+6)))
fi
# Create the LSHandlers array
$plistbuddy -c "add:LSHandlers array" "${launchServicesSecure}"
# Set default for mailto links
$plistbuddy -c "add:LSHandlers:${ONE}:LSHandlerPreferredVersions dict" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${ONE}:LSHandlerPreferredVersions:LSHandlerRoleAll string -" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${ONE}:LSHandlerRoleAll string com.microsoft.outlook" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${ONE}:LSHandlerURLScheme string mailto" "${launchServicesSecure}"
# Set Outlook 2016 as default for email
$plistbuddy -c "add:LSHandlers:${TWO}:LSHandlerContentType string com.apple.mail.email" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${TWO}:LSHandlerPreferredVersions dict" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${TWO}:LSHandlerPreferredVersions:LSHandlerRoleAll string -" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${TWO}:LSHandlerRoleAll string com.microsoft.outlook" "${launchServicesSecure}"
# Set Outlook 2016 as default email from Outlook 2011
$plistbuddy -c "add:LSHandlers:${THREE}:LSHandlerContentType string com.microsoft.outlook14.email-message" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${THREE}:LSHandlerPreferredVersions dict" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${THREE}:LSHandlerPreferredVersions:LSHandlerRoleAll string -" "${launchServicesSecure}"
$USER $plistbuddy -c "add:LSHandlers:${THREE}:LSHandlerRoleAll string com.microsoft.outlook" "${launchServicesSecure}"
# Set Outlook 2016 as default for .ics files
$plistbuddy -c "add:LSHandlers:${FOUR}:LSHandlerContentType string com.apple.ical.ics" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${FOUR}:LSHandlerPreferredVersions dict" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${FOUR}:LSHandlerPreferredVersions:LSHandlerRoleAll string -" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${FOUR}:LSHandlerRoleAll string com.microsoft.outlook" "${launchServicesSecure}"
# Set Outlook 2016 as default calendar from Outlook 2011
$plistbuddy -c "add:LSHandlers:${FIVE}:LSHandlerContentType string com.microsoft.outlook14.icalendar" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${FIVE}:LSHandlerPreferredVersions dict" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${FIVE}:LSHandlerPreferredVersions:LSHandlerRoleAll string -" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${FIVE}:LSHandlerRoleAll string com.microsoft.outlook" "${launchServicesSecure}"
# Set Outlook 2016 as default for .vcard
$plistbuddy -c "add:LSHandlers:${SIX}:LSHandlerContentType string public.vcard" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${SIX}:LSHandlerPreferredVersions dict" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${SIX}:LSHandlerPreferredVersions:LSHandlerRoleAll string -" "${launchServicesSecure}"
$plistbuddy -c "add:LSHandlers:${SIX}:LSHandlerRoleAll string com.microsoft.outlook" "${launchServicesSecure}"
exit- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2019 02:01 PM
@ammonsc While I'm pretty sure it's more convoluted than it needs to be, here's what we do. . .
Smart Group collecting all machines that have Outlook installed.
Policy scoped to the "Outlook Installed" smart group that installs Rich Trouton's OutlookDefault app into /Applications/Utilities
Then we have a Smart Group that collects all machines that have the OutlookDefault app installed
And finally we have a policy scoped to the machines with the OutlookDefault app installed that will allow the user to click from Self Service to launch the OutlookDefault app and click to tell it to make Outlook the default.
I did it this way in large part because the OutlookDefault app needs to be run from the user context and scripting around that requirement exceeds my scripting skills.
Now. . .I probably could do away with the smart group that collects OutlookDefault being installed because if the first policy worked correctly, every machine with Outlook should have the OutlookDefault app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-07-2019 10:42 AM
@tlarkin can you point me to a script I can use for log scrapping? Ty sir.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-09-2019 08:39 PM
I wrote that at a previous job, but basically something along these lines:
#!/bin/bash
# poc for a log collector
currentuser=$(scutil <<< "show State:/Users/ConsoleUser" | awk '/Name :/ && ! /loginwindow/ { print $3 }')
logdir="/Users/${currentuser}/Desktop/logs"
logs_to_collect=(
/var/log/jamf.log
/var/log/system.log
/var/log/install.log
)
mkdir "${logdir}"
for log in ${logs_to_collect[@]} ; do
cp log "${logdir}"
done
zip "${logdir}.zip" "${logdir}"I just rewrote that in a few min and tested it, seems to work. It just places a folder of zipped logs on that user's Desktop. This is basically what it was. I don't have this yet at my current job, but I am still building things out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-09-2019 08:51 PM
Cool @tlarkin I appreciate the help. I will add this to self service and scope this to our Corp IT Dept for end user troubleshooting. Thank you again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2019 02:34 AM
@tlarkin Hi, I ran your script, but the folder comes back empty, have I missed something? any advice would be greatly appreciated. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2019 01:41 PM
Maybe there is nothing to log yet @sdunbar maybe try running sudo jamf policy, manage and recon, install some software on a test machine and see if it dumps to the logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2019 01:43 PM
ahhh yeah I didn't even realize this, but that is a bash-ism you must use full paths with cp and I apparently also wrote one specific piece as if I were writing it in Python, lol sorry y'all
Here is the updated code, tested on my Mac just now
#!/bin/bash
# poc for a log collector
currentuser=$(scutil <<< "show State:/Users/ConsoleUser" | awk '/Name :/ && ! /loginwindow/ { print $3 }')
logdir="/Users/${currentuser}/Desktop/logs"
logs_to_collect=(
/var/log/jamf.log
/var/log/system.log
/var/log/install.log
)
mkdir "${logdir}"
for log in "${logs_to_collect[@]}" ; do
echo $log
cp "${log}" "${logdir}"
done
zip "${logdir}.zip" "${logdir}"my output:
bash-3.2# bash -x ~/IdeaProjects/bash/log_collector.sh
++ scutil
++ awk '/Name :/ && ! /loginwindow/ { print $3 }'
+ currentuser=tlarkin
+ logdir=/Users/tlarkin/Desktop/logs
+ logs_to_collect=(/var/log/jamf.log /var/log/system.log /var/log/install.log)
+ mkdir /Users/tlarkin/Desktop/logs
+ for log in '"${logs_to_collect[@]}"'
+ echo /var/log/jamf.log
/var/log/jamf.log
+ cp /var/log/jamf.log /Users/tlarkin/Desktop/logs
+ for log in '"${logs_to_collect[@]}"'
+ echo /var/log/system.log
/var/log/system.log
+ cp /var/log/system.log /Users/tlarkin/Desktop/logs
+ for log in '"${logs_to_collect[@]}"'
+ echo /var/log/install.log
/var/log/install.log
+ cp /var/log/install.log /Users/tlarkin/Desktop/logs
+ zip /Users/tlarkin/Desktop/logs.zip /Users/tlarkin/Desktop/logs
adding: Users/tlarkin/Desktop/logs/ (stored 0%)- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-10-2019 07:02 PM
@tlarkin lol I have been looking at so many python and bash scripts recently I didn't even realize that lol going cross eyed in code :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2019 12:54 AM
@tlarkin many thanks, working perfectly now. Cheers!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2019 07:17 AM
@hrhnick or anyone can help me with the software Update policy which you use on the Self service
Appreciate your help
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2019 07:56 AM
@Santosh https://hcsonline.com/images/PDFs/InPlace_macOS_Mojave_.pdf & https://hcsonline.com/images/PDFs/Jamf_SS_macOS_HS.pdf should do the trick for you. Follow the steps exactly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2019 08:20 AM
@kdean thanks a lot for sharing the links. But these links provides the details how upgrade the MacOS . But i am looking for installing the security updates from Self Service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2019 10:14 AM
@tlarkin lol I have been looking at so many python and bash scripts recently I didn't even realize that lol going cross eyed in code :)
@kdean yeah I have been primarily writing code in Python for the past few years, and I often forget the tiny things that bash requires nowadays because I don't write in that language every day anymore.
You start to forget things like closing if statements and how bash does string expansion, and other languages do not care about those things.
Glad it is working now, haha
Cheers,
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2019 03:42 PM
@Santosh it would work for the security update as well I believe, any updates that show up in Software Update like security updates should be updated the same way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-30-2019 12:30 AM
Hello @neilrooney , I am similarly looking for self help tools, Please share me the list of tools, ideas and scripts that you have in place.
Cheers!!
-Naren
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2019 05:25 PM
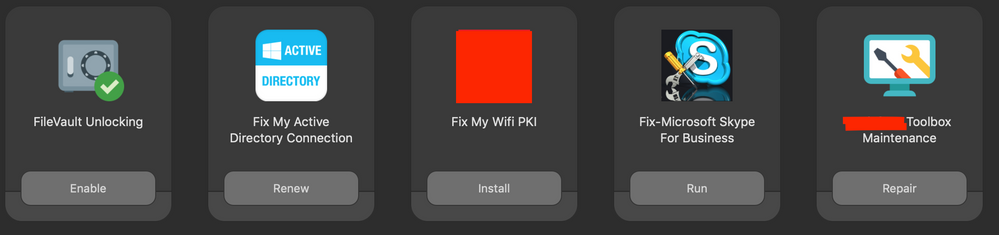
@Naren What does your toolbox maintenance policy do exactly?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-26-2019 09:14 PM
Hi
What key-chain reset script are you people using?
Thanks!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-27-2019 04:02 PM
@PE2000 - here's one that nukes the local keychain:
#!/bin/bash
## Placed by me
#current_user=finger -s -l | grep Login | cut -c 8-25
if test -e /Users/$USER/library/keychains/????????-????-????-????-????????????; then
echo "Local Items keychain found"
rm -rf /Users/$USER/library/keychains/????????-????-????-????-????????????
else
echo "No local items keychain found"
exit 1
fi