- Jamf Nation Community
- Products
- Jamf Pro
- Re: Adding WPA2 Enterprise network but allowing us...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Adding WPA2 Enterprise network but allowing users to supply credentials
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on
07-24-2018
10:04 AM
- last edited on
03-04-2025
09:21 AM
by
![]() kh-richa_mig
kh-richa_mig
I'm in an environment in which we're deploying a new, WPA2 Enterprise wireless network, which will replace our old Corporate WPA2 Personal network. We have AD, but our machines are not bound (I'm looking into NoMAD for password synching without the bind, but that's a separate project). Previously, we would just deploy the Corporate network via config profile.
The new SSID is hidden by default, so I'm looking for something that will add the network AND prompt the user for their credentials. We're not currently requiring certs to connect, and when we do will be pushing them out separately.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2018 10:15 AM
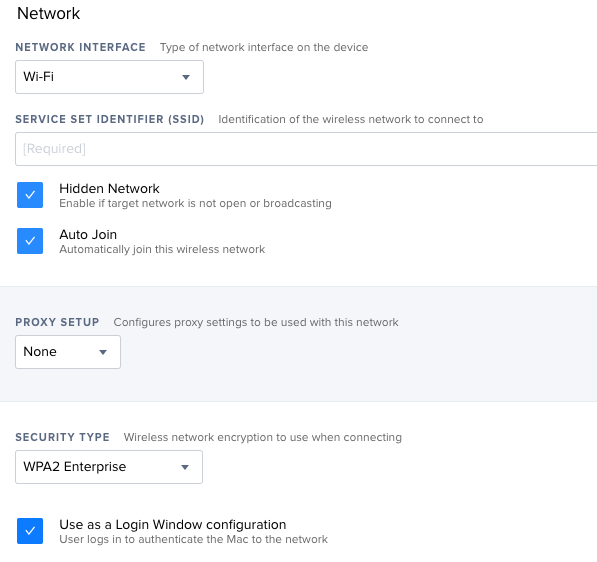
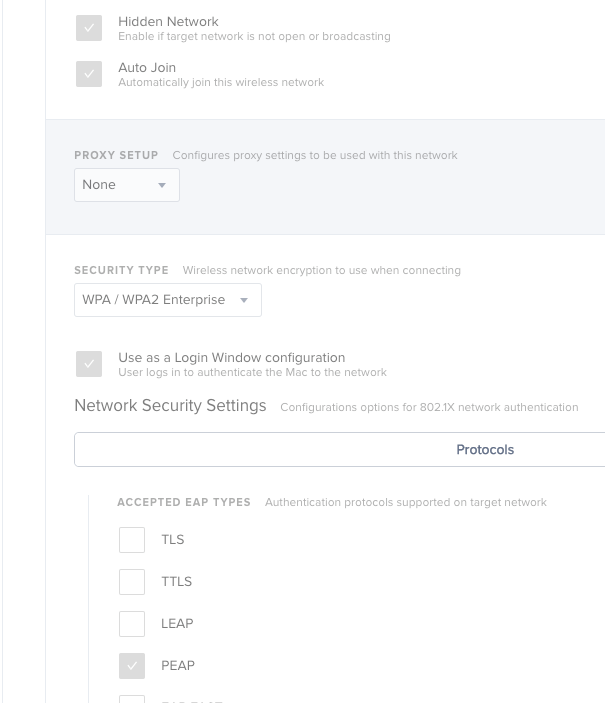
Network Configuration Profile should be able to handle this... Just click the "Hidden Network" and after selecting the Security Type check the "Use as a Login Window configuration"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2018 11:17 AM
Thanks for the response! However, when I select "Use as a Login Window configuration", the box becomes unchecked as soon as I save the payload settings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2018 11:44 AM
It looks to be a known bug starting in 10.0.0 i believe...
[PI-004491] The Use as a Login Window configuration checkbox fails to remain selected for computer configuration profiles with WPA2 Enterprise as security type.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2018 01:36 PM
think its fixed in 10.6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-24-2018 01:54 PM
Thanks, all! I've scheduled an upgrade of our dev environment for tomorrow, so hopefully that resolves the issue. I'll report back once it's upgraded and I've had a chance to test it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-25-2018 05:14 PM
10.6 fixed the checkbox issue, but when I put the profile in Self Service and try installing it, I'm not actually prompted for credentials. System Prefs show that I did get the profile, but I don't connect to the network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-26-2018 06:12 AM
@DaK3ll3r Not that this helps with your question, but more food for thought...
It's been a while since I looked at WiFi security recommendations, but I thought that general consensus was that hidden SSIDs were now considered false security and not worth the trouble they caused. In my previous organization where we had a campus with over 1000 MacBook Airs the recommendation from Cisco and Apple was to broadcast the SSIDs to reduce connection time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-05-2018 05:48 AM
@DaK3ll3r I'm having the same issue right now, did you ever get around to fix this? Network preferences show the "disconnect" button which indicates that the computer knows that it's supposed to connect to my wifi but the popup for the login credentials is not showing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-05-2018 05:04 PM
@mathias.kuse We ended up using NoMAD (aka Jamf Connect) to deploy certs and an identity preference, which associates our corporate SSID with the cert. We then scope a policy that applies a configuration profile that tells the machine to auto-join using EAP-TLS. Together, NoMAD and the config profile deployed by Jamf make for a pretty smooth connection, though the user does have to allow the eapolclient to access the cert's key.
Hope that helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2019 03:43 PM
I am having the same issue - I see the Disconnect button and every few seconds it shows "Authenticating" but no prompt for username and password. I can sometimes click on Disconnect and then Connect. The login prompt then appears and I am able to log in and join the WPA2 Enterprise network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-14-2019 02:15 PM
@leojason sadly I still haven't found a solution and jamf is still analysing the issue. Will keep you posted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-05-2019 09:19 AM
@mathias.kuse +1 on this, please update us if you hear back regarding this issue. I'm deploying WPA2 Enterprise shortly, and would love to make it easier for the users through Jamf
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-27-2019 11:17 AM
@mathias.kuse +1, having the same issues here so would be very interested to hear if this gets solved somehow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-08-2019 10:45 AM
any update??? having the same issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-12-2019 06:40 AM
@DaK3ll3r Can you share some more info about how you're doing this? Our ISE server requires AD user certs which is super unreliable and seems to be tying me to the bind. I've tried messing around with the Identity, Certificates, and AD configuration profiles but I haven't been able to get anything to work at all besides AD Certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-12-2019 02:30 AM
@DaK3ll3r are you able to expand on what you did to get this working with Jamf Connect?
What settings did you use to get the cert from the CA via JCS?
What does the Config Profile look like? Did you then PKG it up to install via a Policy? Why?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-12-2019 11:32 AM
We actually moved away from JCSync, since it required already having access to the CA and that users retain the app on their machine in order to handle renewal. To get the cert in that original use-case, though, we did the following:
- configured the app to point to our Okta domain
- enabled the key to get a cert automatically
- then changed the Get Help menu item to read "Get Certificate"
- configured it to launch a self service policy. That policy would a) confirm connectivity to the CA, b) unload and reload the agent to obtain a cert, and c) touch an empty file against which the supplicant config was scoped.
- That supplicant config included a network payload that told the machine to autojoin our corp network using TLS.
I hope that helps! We found that using ADCS was much more flexible (can be deployed outside the corporate network, the cert + supplicant were in one profile, and it auto-renews), and recently migrated to that. We still leverage Jamf Connect to authenticate a user, and then deploy ADCS certs once a user has authenticated. For new machines that go through Jamf Connect Login, certs are deployed automatically during splashbuddy, and for existing machines on which a user has never authenticated they through a similar JC Sync process as above but in which the "Get Certificate" menu command deploys the ADCS profile directly.