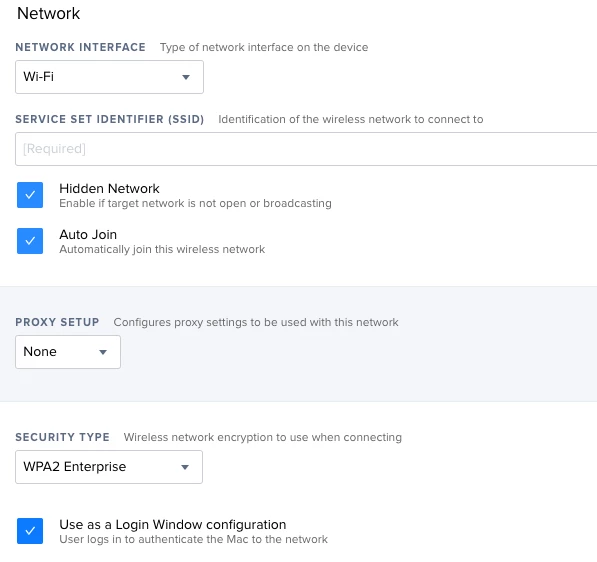
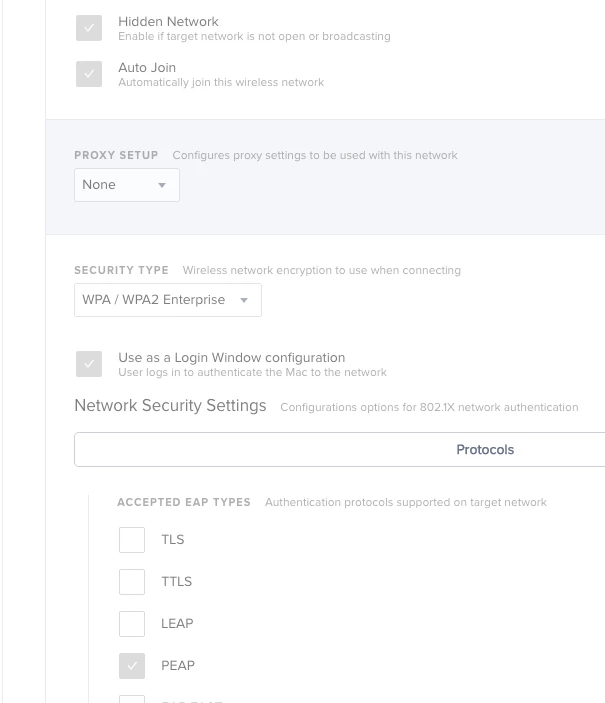
I'm in an environment in which we're deploying a new, WPA2 Enterprise wireless network, which will replace our old Corporate WPA2 Personal network. We have AD, but our machines are not bound (I'm looking into NoMAD for password synching without the bind, but that's a separate project). Previously, we would just deploy the Corporate network via config profile.
The new SSID is hidden by default, so I'm looking for something that will add the network AND prompt the user for their credentials. We're not currently requiring certs to connect, and when we do will be pushing them out separately.