- Jamf Nation Community
- Products
- Jamf Pro
- Re: Catalina Single Sign On
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Catalina Single Sign On
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-23-2019 12:16 PM
Has anyone setup Single Sign on with Catalina OS? I heard about it in during their last event. I am up to date with the Catalina Beta but cannot find anything to set it up. https://developer.apple.com/videos/play/wwdc2019/303/ towards the end of this video is where it is mentioned. We want to have the Mac users login to their computers the same way our PC (All PCs are joined to Azure) users do by using their email address and password. Any recommendations?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2020 01:35 PM
anyone use Enterprise Connect or Apple SSO extension with multiple realms? (35147)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2020 03:13 PM
@sheltond3 I'm working on the finishing touches for my how to guide on the Apple Kerberos SSO extension. The SSO extension does NOT run scripts on it's own because its sandboxed. To get scripts to run, you need something that monitors Distributed Notifications which are sent out when things happen via the SSO extension. My guide is going to include a custom app that will monitor the Distributed Notifications as well as sample scripts that will run based on connection complete, password change, and auditing. I'm hoping to release the guide to the public by end of next week. All of our guides are located here: https://hcsonline.com/support/white-papers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2020 05:14 AM
@kmitnick I too am having problem running their sample script but you app is working but i did get constant pop ups about malicious software and had to run xattr -r -d com.apple.quarantine against it. Do you have your source code available for the sso app you made? Would like to sign, notarize and build it with xcode.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2020 05:54 AM
@tkimpton I did not create the app, but I can ask the person who created it if they mind me sending you the source code. You are correct with the xattr step. xattr -c -r /path/to/download will avoid the malicious software popups. Stay Tuned.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2020 07:14 AM
@kmitnick Thanks very much
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-02-2020 07:57 AM
@tkimpton Here's the source code. I only ask if you can share your finished Xcode project with everyone here when you're done so we can continue working on things to make it better. Thanks.
import Foundation
import AppKit
class NotifyHandler { var notification: String var action: String init(notification: String, action: String) { self.notification = notification self.action = action }
func observe() { DistributedNotificationCenter.default.addObserver( forName: Notification.Name(notification), object: nil, queue: nil, using: self.gotNotification(notification:) ) }
func gotNotification(notification: Notification) { print("Running action") let task = Process() task.launchPath = "/bin/zsh" task.arguments = ["-c", self.action] task.launch() }
}
class AppDelegate: NSObject, NSApplicationDelegate {
func applicationDidFinishLaunching(_ notification: Notification) {
let scriptPath: String = CommandLine.arguments.first!
guard let notificationName = UserDefaults.standard.string(forKey: "notification") else {
print("(scriptPath): No notification passed, exiting...")
exit(1)
}
guard let actionPath = UserDefaults.standard.string(forKey: "action") else {
print("(scriptPath): No action passed, exiting...")
exit(1)
}
let nh = NotifyHandler.init(notification: notificationName, action: actionPath)
nh.observe()
}
}
let app = NSApplication.shared
let appDelegate = AppDelegate()
app.delegate = appDelegate
_ = NSApplicationMain(CommandLine.argc, CommandLine.unsafeArgv)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-03-2020 01:41 PM
Hi there,
In my testing, the keys that perform the Active Directory and local passwords sync in .ExtensionData work great in both ways. Now, I would be very interesting to know which method you guys use to monitor it and what remediation do you use when the sync fails to update Keychain? Thanks all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-06-2020 07:37 AM
@kmitnick unfortunately I could not get that to work. I have reached out to Apple as their instructions do not work. If it is the case an application is need then Apple need to provide this in the OS so all we have to is create a launch agent instead of faffing about.
It’s great your application works but I don’t like to down load and run things other made for security reasons.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-07-2020 12:58 PM
If anyone would have and could share a working LaunchAgent plist file that would trigger a changePW shell non-Swift scripts, that'd be awesome. I am also struggling with this part of the SSO extension setup and deploying CLT isn't planed for now. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2020 09:19 AM
I agree. I do not want to have to deploy and update the CLT to every device in our enterprise, especially when we had a perfectly good working tool (EC) that did all the functionality that this tool is "supposed" to have that didn't require them before.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-12-2020 02:32 PM
Hi everybody,
By any chance, do you know how to:
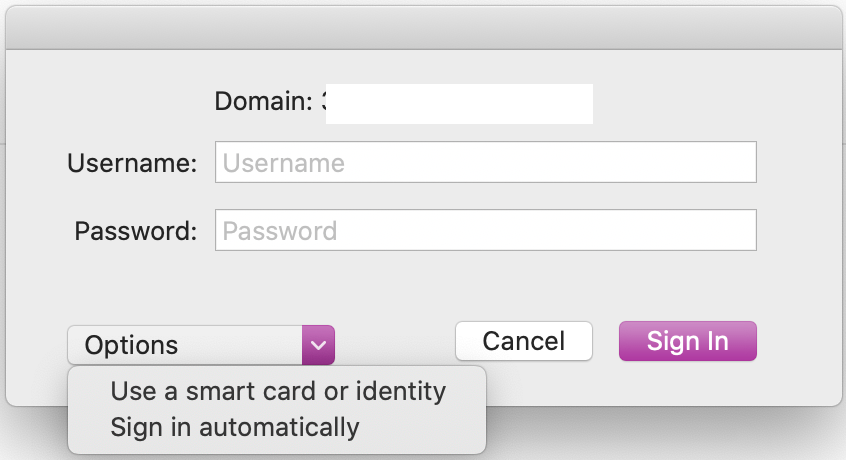
- Remove or replace the @domain in SSO menu in toolbar
- Remove the "Options" field when user wants to authenticate
Thanks :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2020 09:54 AM
Those are a couple things I've asked our rep on as well. They've been put in as feature requests. I'm actually meeting with APS next week to go over some things with the Kerberos Extension SSO, hopefully will get closer to being able to replicate EC and make it an easier transition for all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-13-2020 09:58 AM
Those are a couple things I've asked our rep on as well. They've been put in as feature requests. I'm actually meeting with APS next week to go over some things with the Kerberos Extension SSO, hopefully will get closer to being able to replicate EC and make it an easier transition for all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-26-2020 01:34 PM
This might be the correct discussion to ask this, but, I've been trying to figure out SSO for our web browsers and our Intranet site. All browsers prompt for AD creds (Safari, Chrome, Firefox). I not that familiar with the SSO process and what is needed. I suspect I have a setting incorrect somewhere or not even set. I'm onprem, are using AD credentials with mobile accounts, and, we have Enterprise Connect.
From previous posts it sounds like EC should be able to do this. My Intranet SharePoint guy said they are not using Kerberos for authentication in the site. He said they use NTLM on our windows devices and it works for IE, Chrome, and, Firefox without any issues. Anyone have any suggestions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-26-2020 07:14 PM
@bcbackes As best I could tell MacOS doesn't support SSO on NTLM in the browser. We got this working in our environment by configuring our servers for kerberos authentication. We are using AD bound Macs with Nomad.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-02-2020 11:39 AM
So there are different types of notifications, and because I was using the default one that was in the template scripts (which also looked to be the correct duplicate that we used in EC), that may be what was causing my issues. Apple has asked that I change some permissions around, but also change the launchd to use the "com.apple.KerberosExtension.passwordChangedWithPasswordSync notification" instead. For clarification, our users have to use a separate internal website to change their account password so all the different types of user account will sync, as well as to support some legacy systems and PCI compliances.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-02-2020 02:33 PM
@sheltond3 we also use a separate internal website. Would you mind letting me know what script you're using for password changes and if you installed the command line developer tools on your endpoint? To my knowledge, Kerberos SSO can't trigger a bash script which is where we're stuck right now.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-03-2020 09:32 AM
@jtrant You can use Kerberos notifications to trigger bash scripts, it works. HCSOnline has a nice tutorial about that.
Also, once SSO configuration profile is installed, is anyone would know if there is a key or anything else I could use to avoid SSO extension window to automatically pops up when it first detect local network over VPN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-13-2020 03:57 AM
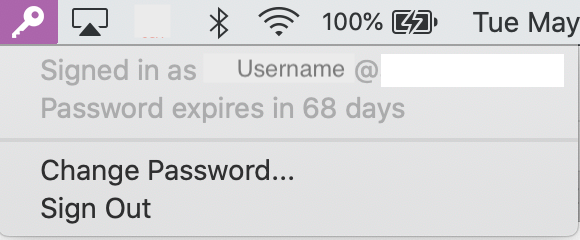
Curious if the days to expiration is still configurable so it shows when rolling over the icon, as it did when we used Enterprise Connect? Users can click on the icon and see how many days they have now, so not a big issue, just curious.
Thankfully changing your password through the SSO syncs back to your FileVault 2 password (like Enterprise Connect did).
https://donmontalvo.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-13-2020 01:18 PM
@jtrant I use a cleaned up version of the passwordChangeSample.sh script that came with the Enterprise Connect installers. This is triggered by the launch agent and the specific kerberos notification trigger that works in your case. For me, with having the separate internal site and the password being synced manually, I use the "com.apple.KerberosPlugin.LocalPasswordSynced" trigger now (after bouncing around a bunch of different notifications, this one turned out to be correct with some config modifications). I've posted a cleaned up version of the password change script I run on github.
I also do have to install the command line tools to run the swift script thats in the documentation from Apple. For the trigger, i'm using the sample swift script, and the sample daemon as a launchagent that has the corrected script path and the notification trigger i mentioned above edited into it.
@Karl941 I actually asked the Apple engineers this exact question as well as if its possible to set up the "Automatically sign in" button to just default answer yes instead of requesting to users, and the ability to hide the additional options dropdown menu in the main window, but so far those aren't available. I was hoping to get more from the updates from wwdc.
@donmontalvo I've never had EC do that, where it just shows when rolling over the icon before, i've always had users have to click it in order to see the days remaining. That would be an interesting feature to add, but seeing how there are still a lot of features missing to provide better parody between the two tools, I doubt that something like that would be high on the list.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-13-2020 04:19 PM
Following on from a few posts above regarding SSO Extension AND use of NoMAD, we are using NoMAD already, and take advantage of the auto mapping of network drives and the issuing of kerberos tickets from on-prem AD via the NoMAd tool. Having only recently begun upgrading to Catalina across the fleet, I've come across and contemplating use of the SSO Extension (way back then and again now its readily available), but wondering what SSO Extension will provide over and above NoMAD? Can the two work together, or is it a case of one OR the other?
Am i missing something here, as there appears a lot of cross over ?
Anyone had any experience using JAMF Connect/NoMAD and the SSO Extension ? Benefits, if any at all ??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-20-2020 06:52 PM
@UbiquitousChris you've saved my life. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-21-2020 10:57 AM
@sheltond3, this is really useful, thanks. Thanks for also sharing your script on Github!
@Karl941 , thanks for pointing me to that guide. Very helpful!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-05-2020 06:44 PM
Hello guys, Do you know how to prompt users to sync passwords using a script? I wrote a bash script to compare the dates of the password changes but don't have anything to trigger the sync screen.
I've been testing the password sync for a while and always worked with me but I was changing the password from the kerberos extension tool.
The thing is that now in production, users have other ways to change passwords, like accessing a portal or using AI. So if they change passwords using other tools, they are not prompted to sync their passwords in the extension, even if the user signs out and signs in again.
Hope someone can help. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-09-2020 09:57 AM
Has anyone found a way to determine if the user is signed into the Kerberos SSO tool? I have an extension attribute for Enterprise Connect but since Kerberos SSO tool is built into the OS I can't figure out a way to do so with the new configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-10-2020 06:00 AM
@jtrant you can use the command
app-sso -I AD-REALM- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-10-2020 08:43 AM
That command is nice but I the only way I can seem to make it work is to save its output to a file and then use defaults to read that. I don't like the idea of using an EA to write anything, and less likely to use it to clean up whats been written. One syntax misstep and you're in for a world of hurt on all devices.
edit n/m, making it output json allows for easier manipulation.
app-sso -i $ADREALM -j | grep user_name | awk '{print $3}'- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-27-2020 11:02 PM
@jtrant , you can read the values of various keys available in the com.apple.appSSOAgent.plist. It is user based plist which means each and every account present in the device will have this plist.
Path to plist file: ~/Library/Preferences/com.apple.appSSOAgent.plist
i am using the same approach to read whether my users have completed the password sync activity or not through Extension Attributes, because users do have an option to cancel the password sync prompt.
If user has Signed into Kerberos tool then you will have various values like
Last connected Date and Time, Last Site Name and so on...
Let me know if you need the bash code, i can share it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-29-2020 12:59 PM
Here's what I've come up with so far:
#!/bin/bash
loggedInUser=$( /usr/bin/stat -f %Su "/dev/console" )
adDomain=$(/usr/bin/app-sso -l -j | grep -- '"' | cut -d'"' -f2)
adUser=$(/usr/bin/app-sso -i "$adDomain" -j | grep user_name | cut -d'"' -f4)
if [[ ${loggedInUser} == "root" ]] || [[ ${loggedInUser} == "localadmin" ]] || [[ ${loggedInUser} == "adobeinstall" ]] || [[ ${loggedInUser} == "_mbsetupuser"]]; then
result="Local"
else
if [[ -e "/Library/ManagedPreferences/com.apple.extensiblesso.plist" ]]; then
echo "Kerberos SSO is installed, continuing..."
elif [[ ${adUser} == "" ]]; then
result="No"
else
result="Yes"
fi
fi
echo "<result>${result}</result>"The 'Local' result is used to identify a not logged in result because a non end-user is logged in. This may or not be useful to you.
Let me know what you guys think!
Justin.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 09-30-2020 06:57 AM
Here is an EA that grabs a bunch of SSO info. Might not be the most efficient way, but it works for us.
~Scott
#!/bin/bash
loggedInUser=$( /usr/bin/stat -f %Su "/dev/console" )
/usr/bin/su - "${loggedInUser}" -c "/usr/bin/app-sso -i YOURDOMAIN.COM" > /Users/Shared/com.apple.KerberosSSO.attributes.plist
ssoLoginTest=$( /usr/libexec/PlistBuddy -c "Print:login_date" /Users/Shared/com.apple.KerberosSSO.attributes.plist 2>&1 )
if [[ ${ssoLoginTest} == *"Does Not Exist"* ]]; then
# User NOT logged into the single sign-on extension
result="${loggedInUser} NOT logged into Single Sign-on Extension"
else
result1=$( /usr/libexec/PlistBuddy -c "Print:upn" /Users/Shared/com.apple.KerberosSSO.attributes.plist | /usr/bin/awk -F@ '{print $1}' )
result2=$( /usr/libexec/PlistBuddy -c "Print:password_expires_date" /Users/Shared/com.apple.KerberosSSO.attributes.plist | /usr/bin/awk -F@ '{print $1}' )
result3=$( /usr/libexec/PlistBuddy -c "Print:password_changed_date" /Users/Shared/com.apple.KerberosSSO.attributes.plist | /usr/bin/awk -F@ '{print $1}' )
result4=$( /usr/libexec/PlistBuddy -c "Print:login_date" /Users/Shared/com.apple.KerberosSSO.attributes.plist | /usr/bin/awk -F@ '{print $1}' )
result5=$( /usr/libexec/PlistBuddy -c "Print:realm" /Users/Shared/com.apple.KerberosSSO.attributes.plist | /usr/bin/awk -F@ '{print $1}' )
result6=$( /usr/libexec/PlistBuddy -c "Print:site_code" /Users/Shared/com.apple.KerberosSSO.attributes.plist | /usr/bin/awk -F@ '{print $1}' )
fi
echo "<result>Kerberos SSO Signed-in User: ${result1}
AD Password Expiration Date: ${result2}
AD Password Last Changed Date: ${result3}
Last SSO Login Date: ${result4}
Kerberos Realm: ${result5}
Kerberos Site Code: ${result6}
</result>"
exit 0- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-10-2020 07:46 AM
Do you actually get a prompt when your password is within the pwNotificationDays? Can anyone provide a screenshot?
In testing this for the first time, my local password did not sync. I changed it again and it synced. Does the SSO extension know to check this and prompt you to sync them if they are out of sync? If so, how often does it check?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-08-2021 03:26 PM
Is there any way to setup the Kerberos SSO so it doesn't run under some user accounts in Catalina? We've got a non-admin account used as a 'guest' account on machines that we'd rather not get synced to someone's AD password. I tried a script run at login-every with outset that kills it, but it relaunches. Relaunch would normally be good, but not in this case. I guess I could setup a launchdaemon for the user account that checks if its running and kills it every 10 seconds or something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-09-2021 09:03 AM
No. File feedback.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2021 04:53 AM
Anyone having to use the kdestroy command to get this kerberose extension working again? I have to do this 2-3 times a week. When we had NoMAD configured we did not see this issue. Is there something I need to look at in the configuration profile to stop this from happening?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2021 07:52 AM
@stutz Unfortunately I have a question rather than an answer for you. We still haven't explored options other than binding but it's on the radar. Is there a reason you're trying out the kerberos extension rather than NoMAD? I've heard a lot of good things about it so this move makes me curious. Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-12-2021 08:18 AM
@jhuls We use Nomad on machines running legacy or outdated OS versions i.e. Sierra, High Sierra and Mojave. Nothing against it as it's an excellent tool, but not having to install another package just to get this simple functionality was a major motivation to use the SSO/Kerberos extension on our Catalina and up machines.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2021 08:42 AM
@jhuls I echo what @mainelysteve said. One less third party package to manage. With this extension that functionality is built into the OS and won't have to rely on a third party developer fixing issues and making it compatible with newer releases.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2021 12:23 PM
Thanks for the responses. I actually figured that aspect was a given but didn't know if there was anything regarding features or bugs that made those decisions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-20-2021 10:42 PM
Nomad definitely has more features, such as managing wifi certificates and mounting network shares.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-21-2021 05:11 AM
@SteveC Absolutely. It's best to list your needs and determine which one will fit the environment best. For us we don't use wifi certs and my staff haven't used network shares since the Stone Age. It boiled down to ensuring we got accurate accounting in PaperCut and that the user got placed in the correct web filter group, both of which are AD controlled.