I'm hoping I'm missing something obvious but I'm stumped. I want to have a number of policies available in Self Service that are only available when a member of the IT team is logged into Self Service on that computer.
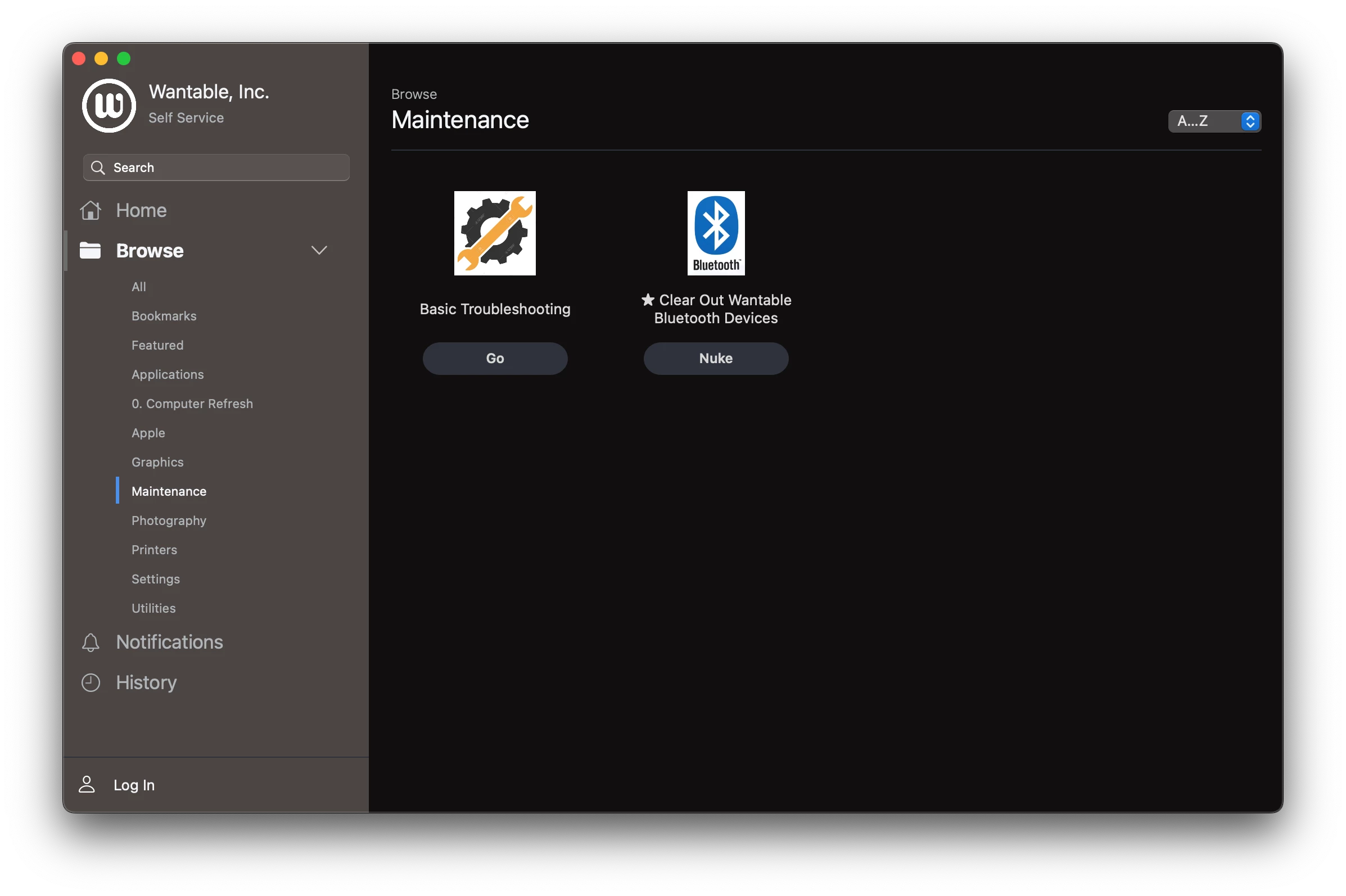
For example, if an employee is having problems, we can log into Self Service and run an policy to gather diagnostics and save it to Jamf.
But these policies should not be available all the time.
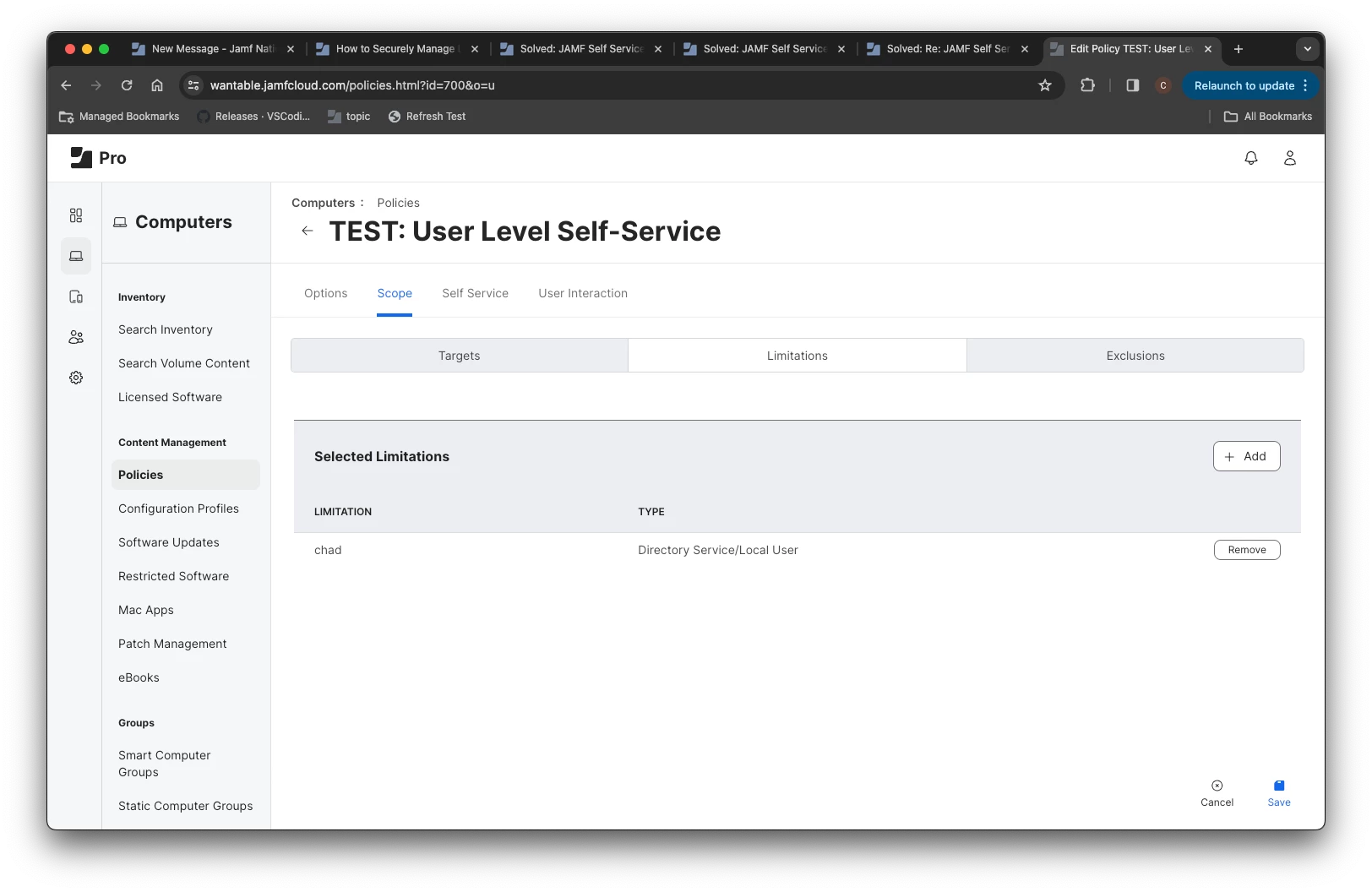
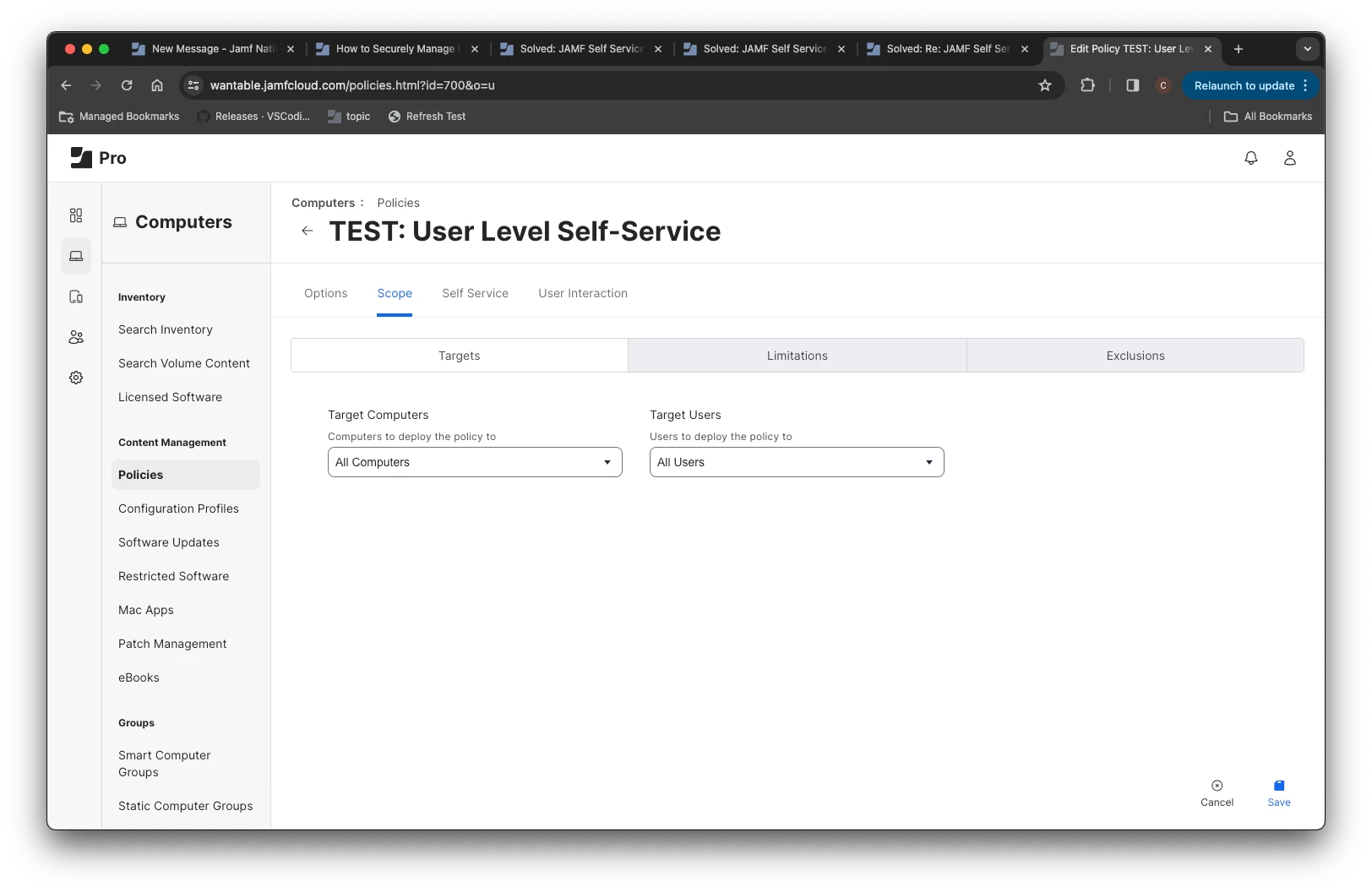
So the goal is to have them scoped to "All Computers" but use Limitations for specific Jamf Pro admin users.
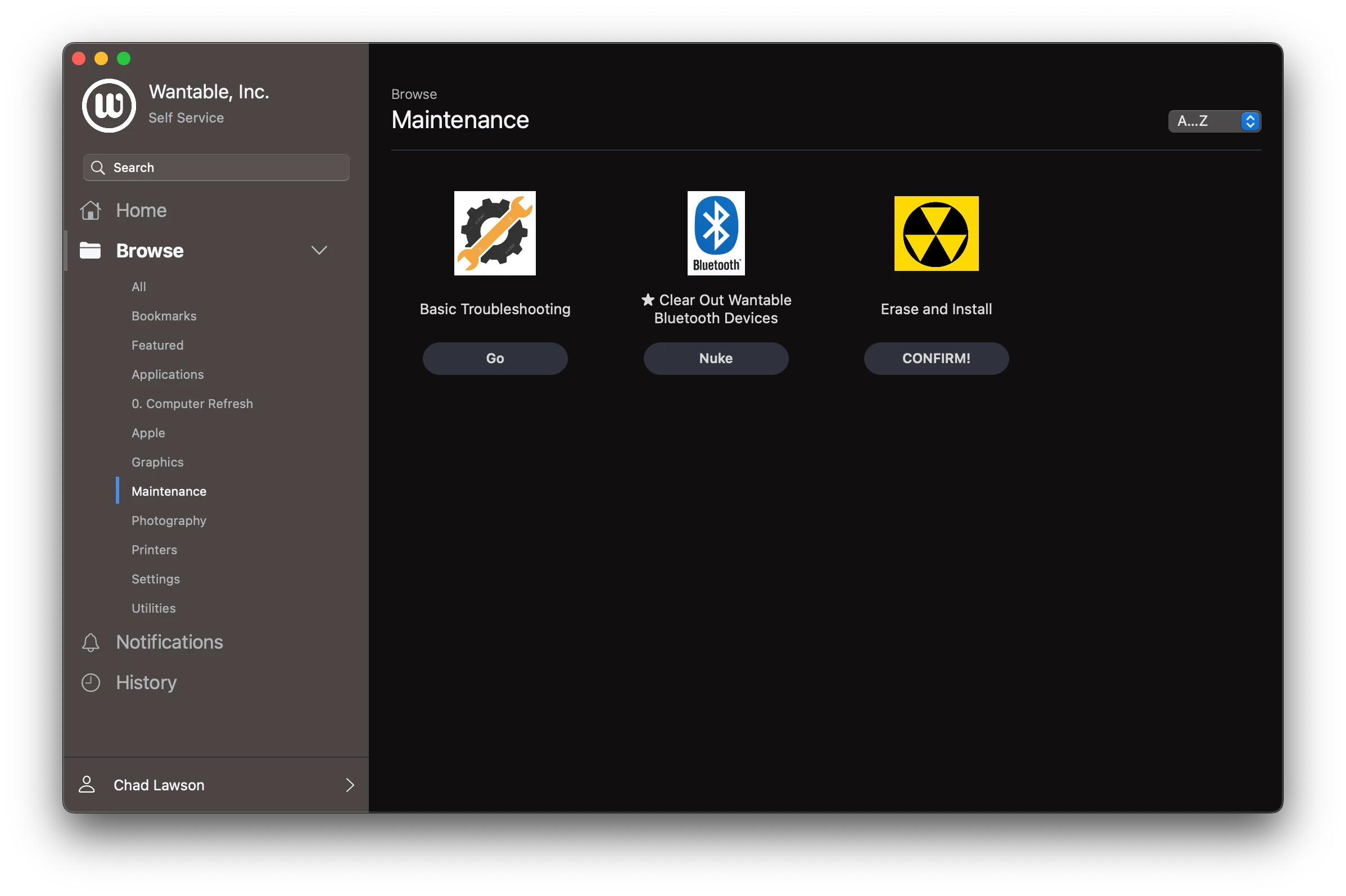
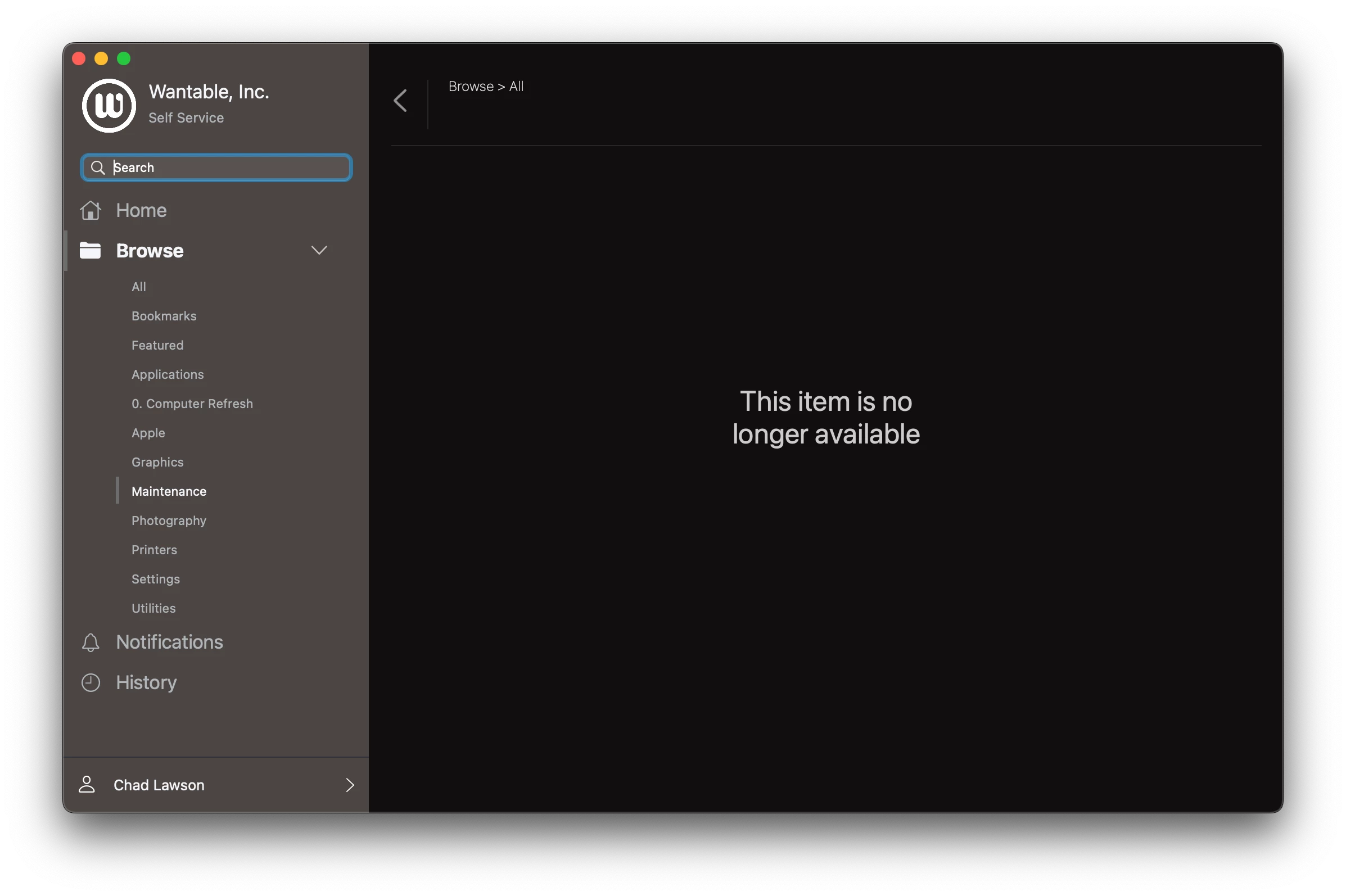
But... when I go to use one of these tools, they start and then disappear and say "This item is no longer available."
If I take away the user limitation, they work just fine; but I can't have these laying around all the time.
What am I doing wrong?