Help with configuration profile for GlobalProtect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-03-2020 12:53 PM
I'm attempting to create a configuration profile for GlobalProtect so that users don't have to enter the vpn server address. When testing the following which was added to a configuration profile in Jamf, it still prompts. Any ideas?
And, yes, I have our real address in the one I'm using.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Palo Alto Networks</key>
<dict>
<key>GlobalProtect</key>
<dict>
<key>PanSetup</key>
<dict>
<key>Portal</key>
<string>vpn.server.edu</string>
<key>Prelogon</key>
<string>0</string>
</dict>
</dict>
</dict>
</dict>
</plist>- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-04-2021 04:02 PM
Hi everyone, so been trying to set this up for a few days and can't figure it out. the documentation from PA is not really clear, so far I have tried everything that was suggested here but no luck. And when I made changes to the Plist the address only gets added after a reboot. am I missing something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2021 08:32 PM
@mmunoz I tried the above process and it worked well all OS. We kept 10.10 only excluded. Please let me know if this works for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-05-2021 08:32 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-19-2021 02:28 PM
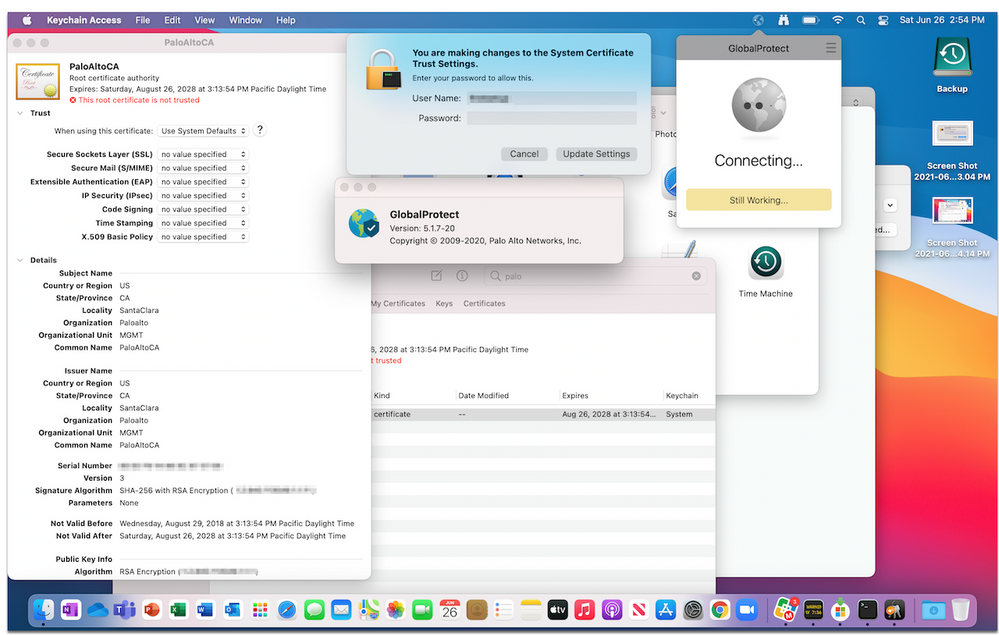
Anybody else seeing GlobalProtect 5.2.5-84 triggering a "You are making changes to System Certificate Trust Settings" authorization prompt at the first connection attempt after initial install (so @franton's removal of the GPService keychain isn't applicable) on Big Sur systems?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2021 10:43 AM - edited 08-27-2021 10:59 AM
@sdagley so it sounds like you are talking about something I encountered in 5.1.7 (see screenshot). We opened a case wit PA and they came back with Apple's macOS Big Sur 11.0.1 Release Notes (not realizing the intended audience is the vendor not the end user). It states:
Security
New Features
macOS Big Sur 11 beta improves system security by requiring an administrator password when a certificate trust settings change is made in the admin trust domain. Running as the root user alone is no longer sufficient to modify certificate trust. User trust domain settings continue to require confirmation by entering the password for the user’s account. This change may affect you if one of the following is true:
o You have written scripts which call /usr/bin/security add-trusted-cert -d ... as root.
o Your process runs as root and calls the SecTrustSettingsSetTrustSettings function to trust a certificate.
Workflows that add trust settings in the admin trust domain, such as for an enterprise root certificate, may require modification if the user can’t authenticate as an administrator at the time settings are changed. (21855995)
Workaround: Use Apple Configurator 2 to create and install a configuration profile containing your root certificate.
Our ask of PA:
Proposed Solution: For PA to use Apple’s suggested workaround. One of the following solutions should suffice:
- Provide a signed configuration profile containing 1 payload: the required root certificate
- Provide the required root certificate to be used in our own signed configuration profile
Then they came back and said they don't provide those solutions or file types. And I then replied with their own KB where they do in-fact offer config profiles and instructions on how to create them. and then reiterated...
Palo Alto is performing an action where scripted actions that are no longer supported by Apple due to increased security. The provided workaround for the vendor is clearly stated and should be provided to their customers by one of the two methods discussed already.
Interestingly in our 5.2.8 testing, we have not seen this prompt for the system level cert. So maybe they fixed this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-27-2021 06:37 PM
@TechM I never followed up my post in this thread, but I solved the problem by extracting the PaloAltoCA certificate from a Mac that had already connected via GlobalProtect, and then added a Certificate payload with that certificate to the Configuration Profile we deploy to approve the GlobalProtect System Extension.
As for why you didn't see the cert prompt with 5.2.8, had those Macs previously connected with any other version of GP? I don't believe that cert changes between client versions, but will depend on GP host server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-05-2021 10:11 AM
Yes @sdagley I have the same issue. Did you figure it out?
thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-05-2021 10:16 AM
@tender It appears that prompt is a requirement on Big Sur now based on the responses I received to my question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2021 10:05 AM
@sdagley: It was something on the VPN backend setting. The root cert was configured to install and disabling that resolved the issue.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-23-2021 12:16 PM
@tender Do you know to go about disabling the installation of the Palo Alto root cert? Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2021 08:08 AM
@tfish Way would you want to disable the installation of the Palo Alto root cert? That's probably necessary for GlobalProtect to establish a connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-06-2021 12:46 PM
@tender Thanks for that info. I'll have to get with our GP team to find out if they're doing the same, and if that certificate is really required. Hopefully it can be deployed via a Configuration Profile if it is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-14-2021 07:52 AM
@Saikat I get an error when running that command.
Running command /usr/libexec/PlistBuddy -c "Add :Palo Alto Networks:GlobalProtect:PanSetup:Portal string myvpn" /Library/Preferences/com.paloaltonetworks.GlobalProtect.settings.plist ; /usr/bin/su - "/usr/bin/stat -f%Su /dev/console" -c "/usr/bin/pkill -l -U /usr/bin/stat -f%Su /dev/console GlobalProtect" ; /bin/sleep 3 ; /usr/local/bin/jamf recon...
Result of command:
su: unknown login: /usr/bin/stat -f%Su /dev/console
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-14-2021 10:30 AM
@Jamie.Boyd you made a mistake in the command. Please see the command line below.
/usr/libexec/PlistBuddy -c "Add :Palo Alto Networks:GlobalProtect:PanSetup:Portal string servername" /Library/Preferences/com.paloaltonetworks.GlobalProtect.settings.plist ; /usr/bin/su - "/usr/bin/stat -f%Su /dev/console" -c "/usr/bin/pkill -l -U /usr/bin/stat -f%Su /dev/console GlobalProtect" ; /bin/sleep 3 ; /usr/local/bin/jamf recon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-14-2021 01:17 PM
Thanks @saikat.tripathi. I'm copying and pasting the command directly into Jamf, and changing the portal string to my vpn name. Can you tell me where the difference is? It looks exactly the same to me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-14-2021 07:16 PM
@saikat.tripathi @Jamie.Boyd The forum software tends to mangle code if one doesn't use the ` (backtick) escape character at the beginning and end of the code. Better yet is to put the script fragment in a separate block by using the ``` (triple-backtick) on a new line, followed by the script lines, and closed by another ``` on a new line. Or just type the code, select it, then use the icon above the Post Response field that looks like >_ to mark the selection as a code block.
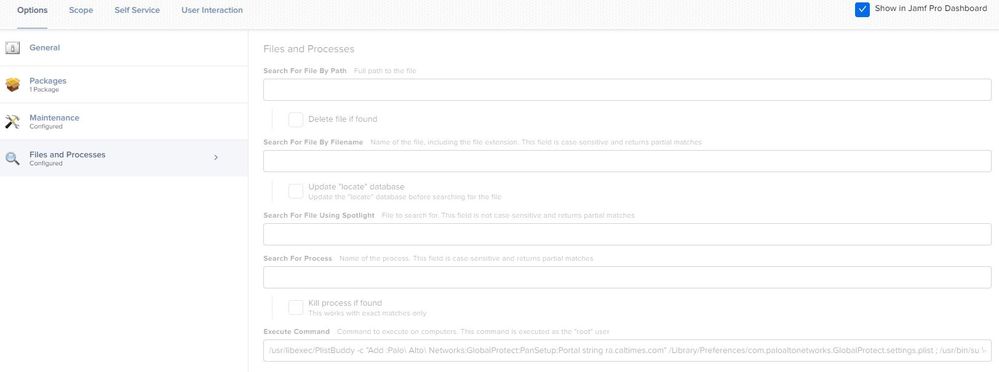
You might also find creating a Script in Jamf Pro for this rather than stuffing it into a Files and Processes -> Execute Command makes life easier since you're not limited to a single line for the entire command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 05-26-2021 09:19 PM
To suppress the keychain system popup for GP 5.2.x you need to export the PaloAltoCA from keychain, upload it in a configuration profile with cert payload, mark it as Allow apps to access and scope it to your device(s). This isnt documented anywhere but was the obvious change that prompted that popup
For its VPN and content filter settings I have been battling with the incompetent Palo Alto support to issue the settings required but this is what they said: "Upon checking found that the JAMF is not the supported MDM from the PaloAlto. The supported MDM are the AirWatch ,Microsoft Intune ,MobileIron ,Google Admin console"
So i asked them for the MobileIron and Airwatch settings.... not heard back yet. I will post here the settings if they ever supply them...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 08-24-2021 10:57 PM
Hello @kostas_athanas1, I believe this is what you're looking for:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u000000HAW8
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-19-2022 12:23 AM
@gregsheppard It's a handy guide for sure, but I don't see anything about the certificate prompt we're all getting...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-19-2022 08:15 AM
@TechSpecialist Are you referring to the prompt for System Certificate Trust settings? If so, extract the PaloAltoCA certificate from a Mac that had already connected via GlobalProtect, then add it a Certificate payload in the Configuration Profile you deploy to approve the GlobalProtect System Extension.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-25-2022 11:41 PM
Just saying thanks! This worked for me!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 01-20-2022 05:39 AM
@sdagley is correct put just add that PA cert to a configuration profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-28-2022 03:15 PM
Hoping to resurrect an old thread here. 😏 I can't get GlobalProtect (v. 5.2.12) to recognize my config profile that is structured like this:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Palo Alto Networks</key>
<dict>
<key>GlobalProtect</key>
<dict>
<key>PanSetup</key>
<dict>
<key>Portal</key>
<array>
<string>portal-1.mycompany.com</string>
<string>portal-2.mycompany.com</string>
</array>
</dict>
</dict>
</dict>
</dict>
</plist>Any idea what I might be doing wrong? The Managed Preference takes precedence over the ones in /Library/Preferences and ~/Library/Preferences, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-28-2022 06:31 PM - edited 06-28-2022 06:32 PM
@markopolo Trying to use a Configuration Profile to configure the portal settings for GlobalProtect is like micturating into the wind. Save yourself some frustration and use @franton 's technique posted below on 12-19-2020 06:26 PM for using defaults write to create the .plist into /Library/Preferences/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-29-2022 05:34 AM
The one thing that became clear to me was that Palo Alto absolutely does not care to change/fix the Mac configurations. That being said, we could never get it to work if we entered more than one portal, so we picked one and wrote a page for our users on how to add the others (we have four).
Currently, we're using the config profile for the system extensions and using the plist method that @sdagley references - works perfectly for us (still only one portal, though).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-28-2022 10:06 PM
@markopolo
Not sure if my experience can help but here we go!
I do recall it taking some time to figure out all the settings. I also used the GP documentation to set everything up.
In total I used 5 profiles. I like to keep mine separate incase a change has to be made.
- App & Custom Settings - Gateway
- Content Filter
- Notifications
- Sytem Extension
- Disk Access
I do recall our Networking team having issues with a user selecting which certificate required but they made a change an our users do not get prompt to choose a cert.
GP has been pretty stable for us. A few quirks here and there but nothing large scale.
Here is our Gateway setting Profile. All other settings are pushed down from GP Server once the user connects.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PanPortalList</key>
<array>
<string>xxxx.xxcloudservice.com</string>
</array>
<key>Prelogon</key>
<integer>0</integer>
<key>User</key>
<string>$USERNAME</string>
<key>WebKitCacheModelPreferenceKey</key>
<string>1</string>
<key>WebKitWebGLEnabled</key>
<string>:false</string>
<key>user-credential-saved</key>
<string>true</string>
</dict>
</plist>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-29-2022 06:09 AM
I was using a JAMF profile to configure the portal address but changed to using defaults write because issues reported by users. When using the profile, the portal was configured but users were not able to add additional portal addresses. Changing to defaults write solved this for me.
defaults write /Library/Preferences/com.paloaltonetworks.GlobalProtect.client PanPortalList -array-add portal.address.com;
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 06-29-2022 08:46 AM
Been a while since I last responded to this. Some notes:
1) Palo Alto changes the format of it's configuration files between releases. 5.1.x has a different format to 5.2.x which is different to 6.x
2) As a result, I start with the installer and a completely blank uncontrolled mac to capture what it's setting and it's formatting. That method has proved effective in helping generate config profiles for the URL settings.
3) Palo Alto provides some pre-built and signed .mobileconfig files for things like split tunnel DNS. Badger the heck out of your network team for Palo Alto documentation access. I've done a lot of this work blind and I really could have used that information.
4) That covers the URL side of things. Palo Alto still has this annoying habit of some of it's preferences won't read out from profiles but will read from the plist file directly hence the defaults write approach. That's a rabbit hole in advanced syntax I don't want to go near again.
Still all easier than a lot of other VPN clients. ;)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 07-27-2022 02:21 PM
Much appreciated!
Ours worked for 5.x.x but now that we are on 6.x.x - our configuration profile adds the URL but it doesnt launch the pop-up window to sign-in.
If we try it without the configuration profile, 6.x.x works (pop-up window appears) and we would need to enter manually.
Do you happen to have Configuration Profile for 6.x.x?
Extra info:
If we use old GP 5.x.x with configuration profile, the prompt pop-up works but we would need manually update it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-11-2022 09:56 AM
I'm starting to test GlobalProtect 6.1.0 because I've been struggling with getting the portal address populated without a reboot. The 6.1.0 documentation references this url for configuration in Jamf Pro:
Deploy the GlobalProtect Mobile App Using Jamf Pro (paloaltonetworks.com)
I'll be testing this out this week.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 10-11-2022 01:34 PM
This worked really well in my testing. It was clean and didn't require the user to interact with anything other than entering their username and password.
Policy for Package, Script, Inventory:
Configuration Profile for System Extension and PPPC:
Enable System and Network Extensions on macOS endpoints Using Jamf Pro (paloaltonetworks.com)
Configuration Profile for Notifications:
No link but just used a bundle id of "com.paloaltonetworks.GlobalProtect.client"
In case you missed it, this was with the 6.1.0 package.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 11-08-2022 11:46 PM
on version 6.1.0, deploy the application custom profile with preferences domain com.paloaltonetworks.GlobalProtect.client works.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PanPortalList</key>
<array>
<string>vip1.gptest.com</string>
<string>vip2.gptest.com</string>
</array>
</dict>
</plist>