Gents,
We have the following situation in our macOS environment.
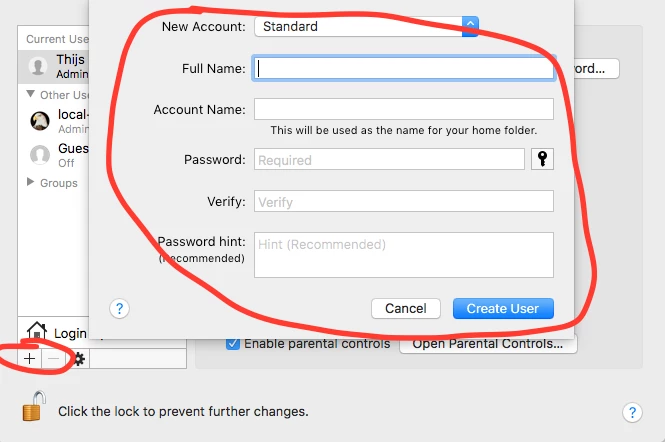
The user is using a macbook, on the macbook are the following accounts pre-defined
- local administrator account that is only available for IT Support staff.
- The user his personal account (Managed, Mobile)
The users have the possibility at this moment to create local accounts for family members or kids or even co-workers.
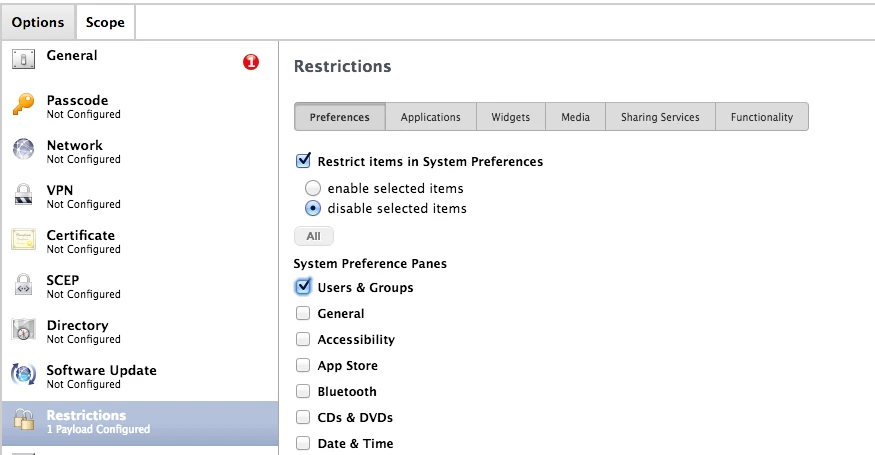
We really want to block that, but keep the admin user rights active for the user of the macbook.
Anyone knows how?
Many thanks!