Our security team has mandated that we get all Macs patched every month. Jamf is our primary source, and we use Tanium for pushing updates to those who failed to perform the installs themselves. 10.11 and 10.12 security updates work fine and install without issues now in both. I got 10.13 combo/standalone updaters working in Jamf using "Restart if a package or update requires it" and checking off "perform authenticated restart...". In Tanium, running the installer doesn't do anything, because it just installs and doesn't actually reboot. I created a script to run the installer then reboot after, but that doesn't actually install the script.
What exactly is Jamf's method to reboot with the "authenticated restart"? I have seen people suggest "fdesetup authreboot" or something along those lines, but it requires entering a username/password. The issue with that is a user can cancel any dialog box and that part would fail. We need to be able to install all updates and reboot as needed, so this should be easy to figure out.
It's a little unclear. It sounds like you are doing the right things with Jamf, and you say the combo updates are working. It also sounds like Tanium is the product that isn't working. Is that right?
As for suggestions, you could try a payload-free package that runs the softwareupdate binary as a patch policy. This way you could have a prompt for users when it's time to update as well as a time when that window expires and the update is forced. I'm not sure if you would need to do any additional scripting with FileVault, but this could possibly be added on into the payload-free package.
@wesleya Most of our non domain bound devices update fine. The problem is the domain bound ones, which are also behind a proxy, so running softwareupdate doesn't always work, unfortunately.
If Jamf can get the computers to restart OK, I might try delivering a payload-free package through Tanium that calls the Jamf policy with a custom trigger. Something like this:
#!/bin/sh
sudo jamf policy -event UpdatePolicy
exit 0
@wesleya Our non bound devices can't reach our file share (we're working on fixing that), but I think I might try to figure out how to deliver the pkg file with tanium, install it, then call a jamf policy to reboot with the authenticated option checked. That might work in the interim.
Sounds like the right idea to me. Depending on how that works, you may also be able to use the installer binary to install the combo update PKGs. The script might look something like this:
#!/bin/sh
installer -pkg $ComboUpdatePKG -target /
shutdown -r now
exit 0
I'm running pretty much that exact script through Tanium, and it reboots, but it's not an authenticated reboot so it doesn't actually install the patch.
Gotcha. Sorry, just throwing out what I can think of on this one. It looks like an authenticated restart (under the restart options payload) might only work if you use a management account, and I'm not sure if that's changed now with Secure Token and all the rest in 10.13.
I did see a script out there (rebooting-and-bypassing-an-encryption-login)
that uses cocoaDialog to prompt users for a password, but that probably isn't quite ideal either. Probably at this point, it's worth bringing in Jamf support. They've probably seen something like this before.
It might not be the management account, since the user has to be allowed to unlock the drive. But it can take the recovery key, so I wonder if they look at the inventory to find the recovery key and pass that to "fdesetup authrestart" to use. Once the recovery key is set, you can't pull it via script on the device like you can with, say, a BitLocker managebde command. I would have to enroll a clean device and encrypt it without my FileVault configuration profiles to test that I think.
I saw that post you linked and some similar ones, but like I said, If a user cancels that then it would fail and the update wouldn't install.
Well, the recovery key isn't accessible via the API, so I'm not sure how you'd pass it to the script. There is a feature request for this though here. Another place you might want to ask about this is the Mac Admins Slack. Plenty of FileVault users there, there might even be a Tanium group.
So I created a policy with a custom trigger that gets called from my script. The restart options are configured below:
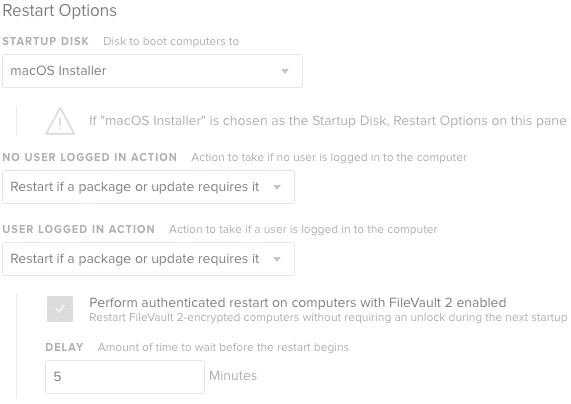
The command from Tanium is:
/bin/bash TaniumInstallAndAuthReboot.sh macOSUpdCombo10.13.6.pkg
The "TaniumInstallAndAuthReboot.sh" script is:
#!/bin/sh
/usr/sbin/installer -pkg $1 -target /
/usr/local/bin/jamf policy -trigger PerformInstallerAuthReboot
My first test looks like it was successful. I'll be testing some more, but I'm glad I found a way to get this working. Thank you @wesleya!

