Hello jamfnation,
I have a question. I try to rename some user accounts to match the company pattern. We want to do this process as smooth as possible for the user and admins. Therefore I've written a script which checks values and asks the user several questions which in the end creates a plist with some variables. After that the script reboots the computer and uses Rich Troutons "First Boot Package Install" (script almost completely rewritten) to show a log to the user what is happening. At that window the script, which is started by a LaunchDaemon, uses dscl to change the homefolder, uses mv to move the homefolder and again uses dscl to change the username.
Now my problem:
In order for dscl or mv to be able to change the homefolder it needs access to it (PPPC). My script is signed and stays signed, and a PPPCP is in place to allow for my script to access Admin Files and/or All Files. I also tried the unsecure way and allowed /bin/bash access to AdminFiles/AllFiles.
However it is not working.
When I inspect the logs of com.apple.TCC I see this entry:
Refusing TCCAccessRequest for service kTCCServiceSystemPolicySysAdminFiles from client /bin/bash in backgroundIf I try the same script manually from terminal (not via LaunchDaemon) I get this at com.apple.TCC, which I know how to allow:
Prompting for access to kTCCServiceSystemPolicySysAdminFiles from /System/Applications/Utilities/Terminal.app/Contents/MacOS/Terminal on behalf of /usr/bin/dscland this prompting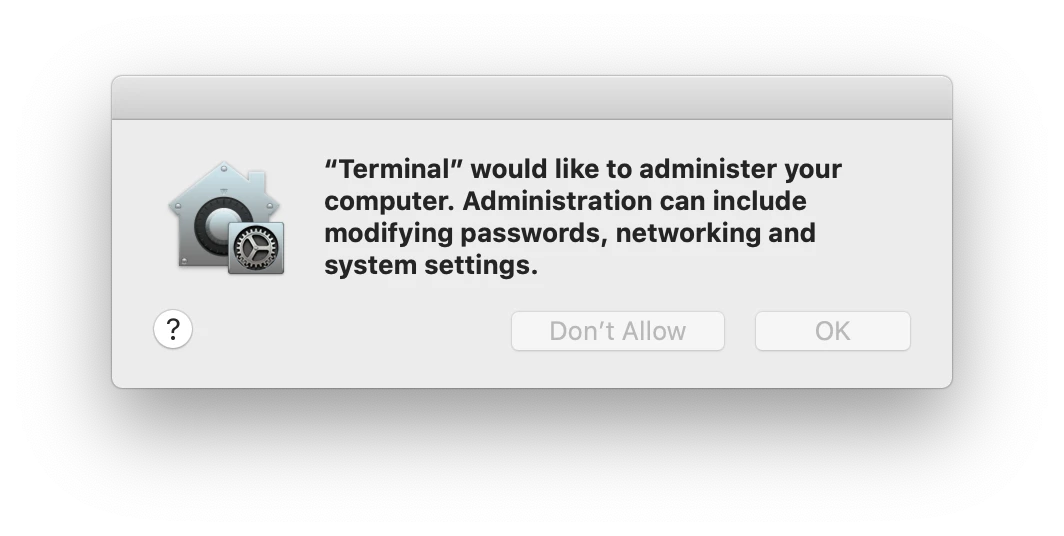
Now my question:
What am I missing?
Is it somehow not possible for a script, started via LaunchDaemon at loginwindow (without any user logged in), to leverage PPPCP to be able to access local user homes?
Any ideas how to get around it?
I hope you can help me!
Thanks
Lenny






