Sophos issues with BigSur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2020 03:22 AM
Hey guys hope you are all well coming up to Christmas. We have been having issues with Sophos popups on BigSur. i have followed all the steps Sophos recommend but we still get the pop ups i have attached out configs and the pop ups were getting
- Labels:
-
Configuration profiles
-
Jamf Pro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 12-18-2020 03:31 AM
Do you have early access to v10.0.2? Any version prior to that is not compatible with macOS Big Sur. v10.0.2, I am hoping will become officially available early-mid January as we're having to hold back on deploying M1 based MacBooks.
See here for more information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2021 01:33 PM
good luck, it still not approved as of last week. Suggest to move away from Sophos into any other vendor that truly cares.. Big Sur has been out since November 12, 2020. its now 1 day short of march and nothing...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 02-28-2021 01:42 PM
v10.0.4 is the version that will support Big Sur, and I am told it is currently rolling out with the aim of being deployed to all customers by 4th March.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-03-2021 12:00 PM
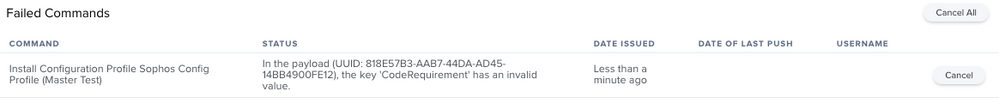
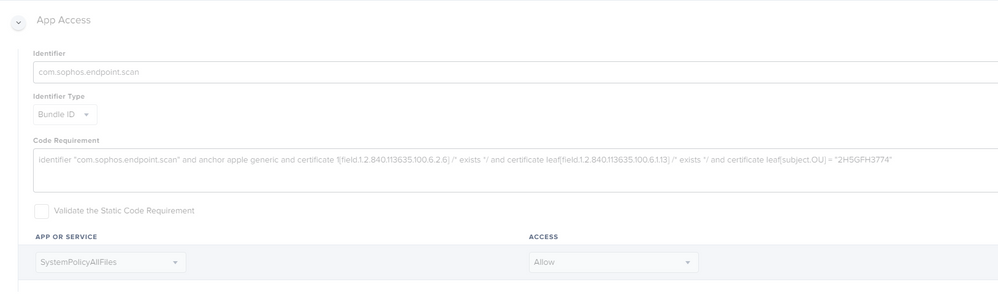
Hi all, So I went by the following article (https://community.sophos.com/intercept-x-endpoint/f/recommended-reads/116397/sophos-mac-endpoint-how-to-configure-jamf-privacy-preferences-for-10-15-compatibility) pretty much the same process as @Jack.Turner and keep getting a failed status "In the payload (UUID: 818E57B3-AAB7-44DA-AD45-14BB4900FE12), the key 'CodeRequirement' has an invalid value."
Anyone else getting the same error message? Currently deploying this to intel - Big Sur, with Sophos Endpoint on 10.0.4. Also erroring out for the M1's as well...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-04-2021 05:08 AM
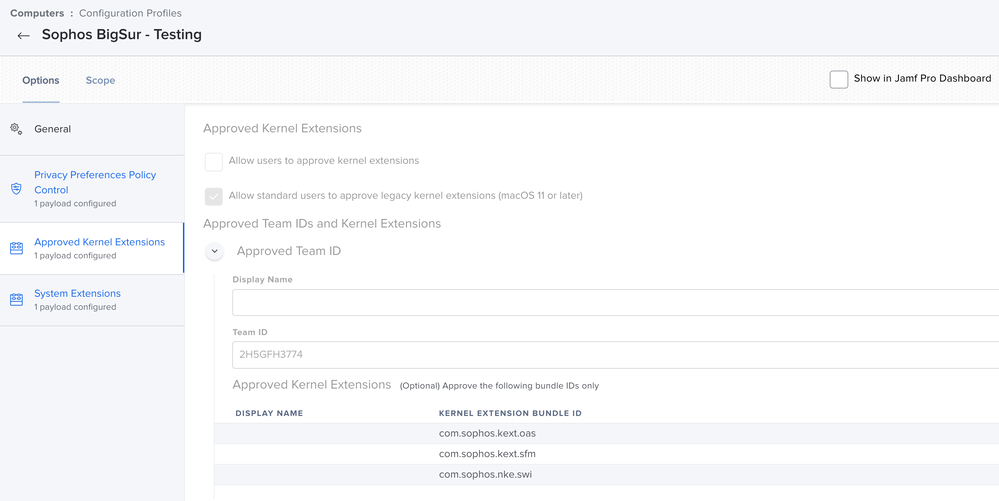
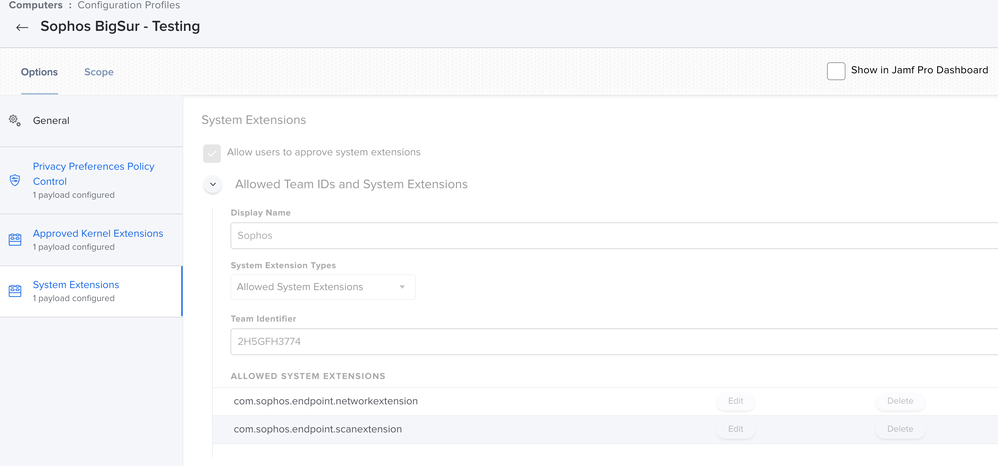
@G_Zirrak Did you separate the Kext Approvals, Privacy Policies, and Approved System Extensions into different profiles? I've only tested on a Big Sur M1 mac so far and it seems to be working (without the Kext approval profile since that is not possible on M1.)
Edit: Cannot get 10.0.0.4 working on an Intel Mac running Big Sur.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2021 01:42 AM
Hi,
I get most of it working on Intel, however, noticed 1 Mac not getting ScanD to start, any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2021 04:08 PM
Hi,
Sophos 10.0.4 seems to work on both Intel x86_64 and M1, however it still requires users to Allow ScanD in System Preferences > Security & Privacy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2021 04:33 PM
Hello,
Thanks for the heads up @SirSir I went ahead and separated the Kext Approvals, Privacy Policies, and Approved System Extensions to 3 different config profiles. I've scoped out the KEXT approval to OS's below Catalina and scoped out the System extensions to Catalina and Big Sur smart groups. Seems to be working for the most part, although not sure if I had manually check marked the boxes within the security & privacy settings before shooting these config profiles out.
@fredrik.virding I also noticed the same issue with not getting ScanD to start on one MacBook Pro. I have not tested a re-install of Sophos yet... But if you happen to find any resolutions/work arounds please let me/us know. Not seeing much Sophos Endpoint for Mac customers on here or any other community platforms as much... It would be great if we can all continue to communicate issues/resolutions on this thread, specially with M1 + Sophos. I truly appreciate everyones time and efforts to assist.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-10-2021 11:42 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2021 04:35 AM
just on the above the kext profile is installing on our m1 machines (11.2 and above) from the above error message just check the code requirements for all the stuff you copied and pasted to make sure there is no special characthers or spaces. i think when i copied them out the first time one of the boxes didnt copy the "i" in identifier and i got the same message.
iam seeing something slightly different. When i go to system preferences > network the sophos web network extention is showing as not running, but in the application itself the service is showing as running.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2021 04:44 AM
Sophos Endpoint is incredibly frustrating. I have followed their documentation to the letter, or as best one can given their screenshots and writing style. They took far too long to get it ready for Big Sur at all. Still no luck having it working on all Big Sur machines. Some work, some don't. Most ocmmon issue I have is services stopping or not starting at all, esp. scand and SophosEventMonitor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2021 05:16 AM
According to Sophos, if you're upgrading from Catalina to Big Sur, Sophos will not operate properly. You have to uninstall Sophos, upgrade to Big Sur, and then re-install Sophos. And make sure that all of your PPPC/Extension/Kext profiles are on the machine BEFORE upgrading to Big Sur. I don't think this is intended behavior, but still very annoying.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-11-2021 04:41 PM
@SirSir that's mind-blowing that Sophos has no better recommendation. Most of our users are standard users, so they couldn't uninstall Sophos even if we asked them to.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-12-2021 04:33 AM
@cradice I agree! And with the tamper password and removing of the system extensions that requires turning off SIP in recovery, its just not a possibility. We're staying on Catalina for another year until they can get this stuff figured out. Hopefully we can switch to another AV product in the next few years as Sophos continues to drop the ball.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-12-2021 02:55 PM
Hi @fredrik.virding , would you be able to share a screenshot of the ScanD PPPC addition you created? I would greatly appreciate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-12-2021 05:10 PM
It's far from ideal, but I am using a self-service policy that first uninstalls Sophos, and then updates to Big Sur. From there a separate policy that runs at user login (post-update) that triggers another policy, scoped to computers running Big Sur without Sophos installed, to re-install Sophos. In my limited testing, this worked for me. This allowed for the system extension profile for Sophos to exist before the Endpoint installation, which was originally creating the failures. Everything in pre-requisites showed green across the board afterward with this workflow, though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-12-2021 05:49 PM
Hi @cradice On my Intel + Big Sur test machine, which was previously upgraded from Catalina, I manually uninstalled Sophos using the Sophos uninstaller. From the Sophos Dashboard I got the uninstall password for the specific computer and disabled the tamper proof feature. After uninstallation, I did not delete any other sophos extension/files from any library or system folders. I just did a restart, made sure the computer had the correct PPPC and System extensions before re-installing (I did not scope out Kernal extension for Big Sur). After re-install I still get the ScanD service not working. Other then the Sophos Uninstaller, was another step I should've done for completely removing Sophos from the computer?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-13-2021 07:01 AM
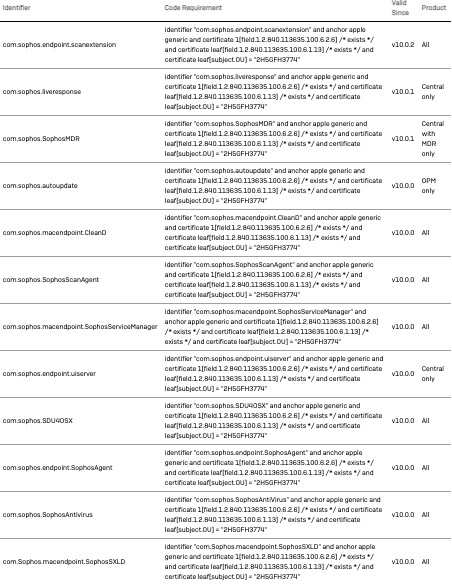
Hi @G_Zirrak ,
Something like this. This has worked for us on newly installed M1´s with Big Sur, and Intel Macs with Big Sur.
More info coming about Catalina > Big Sur.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-15-2021 11:49 AM
Thanks @fredrik.virding for sharing that screenshot. I pretty much created the same config profile using the PPPC Utility through GitHub last week. So far didn't find much luck with the additional PPPC, I even uninstalled Sophos and re-installed after making sure that all of my PPPC profiles were present before the re-install. I will be doing some more troubleshooting/testing this week...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-15-2021 11:57 AM
Hi @G_Zirrak ,
I did some uninstall / reinstall too. I can update later with my results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-15-2021 05:02 PM
@G_Zirrak my workflow looks like this:
Self Service policy to upgrade to Big Sur: First step: Script to uninstall Sophos
!/bin/bash
# Remove Tamper Protection
rm -R /Library/Sophos Anti-Virus/product-info.plist
# Remove and uninstall Sophos Endpoint
/Library/Application Support/Sophos/saas/Installer.app/Contents/MacOS/tools/InstallationDeployer --force_removeSecond step: Script for macOSUpgrade.sh
Once the upgrade completes I have a policy that runs at login (which the user must do post install):
#!/bin/bash
## Jamf Recon
sudo jamf recon
## Take a break
sleep 10
## Trigger Sophos re-install policy
jamf policy -trigger reinstallSophos;
exit 0This script runs a recon, which puts the computer in a smart group for computers on Big Sur, that don't have Sophos installed - and then calls on another policy to re-install Sophos to that is scoped to the aforementioned smart group. This last policy that re-installs Sophos performans an inventory update afterward as well to remove the computer from the group.
Configuration Profiles: System Extensions - The two System Extensions necessary for Sophos/Big Sur scoped to computers on Big Sur. These should apply as soon as that first recon runs, which should make sure they are applied before Sophos is re-installed.
Kernel Extensions - One configuration profile scoped to Catalina and earlier computers that has "allow standard users to approve kernel extensions" unchecked, and another scoped to Big Sur machines that has the checkbox enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-16-2021 09:51 AM
'According to Sophos, if you're upgrading from Catalina to Big Sur, Sophos will not operate properly. You have to uninstall Sophos, upgrade to Big Sur, and then re-install Sophos. And make sure that all of your PPPC/Extension/Kext profiles are on the machine BEFORE upgrading to Big Sur. I don't think this is intended behavior, but still very annoying.'
Is this documented anywhere? Been looking for it on the Sophos site but can't find it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-16-2021 11:19 AM
@agrant Wasn't documented, was in the comments of one of their documentation/forum posts from a Sophos employee.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-17-2021 07:21 AM
For a new installation of Sophos on a Mac, Sophos needs to be allowed in the General tab of the Security & Privacy window. If Sophos needs to be re-installed on the same Mac, the process of allowing Sophos no longer needs to be repeated since the same allow process will be retained by the operating system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-24-2021 01:48 AM
Hi folks.
Made some progress. As pointed out by many here, upgrading does seem to break the ScanD specifically. Everything else is green in our environment.
With some clever scripting, we uninstall Sophos via Self Service and also the device entry in Sophos Cloud. After that, we restart the Mac and reinstalls Sophos via Self Service.
This time, in System Preferences > Security & Privacy, there is an option to Approve 2 "nameless" items, most likely the SEXT's, once they are approved, the Mac is green again in Sophos. A very..annoying process, hopefully something that can be fixed by Sophos.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-24-2021 12:01 PM
@fredrik.virding Would you mind sharing the script?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-25-2021 07:40 AM
Sure,
#!/bin/sh
## Clearing out all Sophos Directories
sudo rm -R /Library/Sophos Anti-Virus/
sudo rm -R /Library/Application Support/Sophos/
sudo rm -R /Library/Preferences/com.sophos.*
sudo rm /Library/LaunchDaemons/com.sophos.*
sudo rm /Library/LaunchAgents/com.sophos.*
sudo rm -R /Library/Extensions/Sophos*
sudo rm -R /Library/Caches/com.sophos.*
echo "Sophos Libraries Removed"
##Unstalling Sophos
sudo /Applications/Sophos/Remove Sophos Endpoint.app/Contents/MacOS/tools/InstallationDeployer --force_remove
sudo /Library/Application Support/Sophos/saas/Installer.app/Contents/MacOS/tools/InstallationDeployer --force_remove
echo "Sophos was removed."I run that, performs the upgrade to Big Sur, and reinstalls via Self Service. However, more testing coming soon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 03-31-2021 08:01 AM
Hi Folks,
After some testing and several headaches. My current workflow, with alot of help from the Macadmins slack. I now have a way to go from Catalina to Big Sur without breaking Sophos.
At first, we make sure the Mac is running 10.15.7. I have created a button in Self Service doing to the following command, after some digging on the Apple forums and Slack.
#!/bin/bash
##
##
##
currentUser=$(scutil <<< "show State:/Users/ConsoleUser" | awk '/Name :/ && ! /loginwindow/ { print $3 }')
echo "$currentUser is logged in"
PATH=$PATH:/Library/Application Support/JAMF/bin/jamfHelper.app/Contents/MacOS
# Run a fullscreen jamfHelper window and put it into the background
jamfHelper -windowType fs -fullScreenIcon "/System/Library/CoreServices/JavaLauncher.app/Contents/Resources/JavaLauncher.icns" -icon "/System/Library/CoreServices/JavaLauncher.app/Contents/Resources/JavaLauncher.icns" -heading "Preparing your Mac for Big Sur" -description "Please ensure the charger is connected and do not turn off your Mac" &
PID=$! # Get the pid of the jamfHelper command
#Remove software update restriction
sudo /usr/sbin/softwareupdate --reset-ignored
#Write to update plist
sudo /usr/bin/defaults write /Library/Preferences/com.apple.commerce.plist LastRecommendedMajorOSBundleIdentifier "com.apple.InstallAssistant.macOSBigSur"
sudo /usr/bin/defaults write /Library/Preferences/com.apple.SoftwareUpdate.plist LastRecommendedMajorOSBundleIdentifier "com.apple.InstallAssistant.macOSBigSur"
#Creating receipt to get System Extensions and Network Proxy
sudo touch /Library/Application Support/JAMF/Receipts/bigsurrequested.pkg
#Final Recon to update Jamf
sudo /usr/local/jamf/bin/jamf recon
sleep 1m
#kill JamfHelper FS Window
kill $PID
echo "JamfHelper Killed"Forcing the recon just to ensure it all checks in.
Once done, i have a Smart Group checking for the receipt, and starts to download the installer via softwareupdate --fetch-full-installer.
Once done, if the User is admin, the app can start and they can begin upgrading right away. If not admin, the installer App quits right away, and they go via Self Service instead.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-14-2021 07:25 AM
@G_Zirrak did you ever get this to work? I'm having the same issue where ScanD is stopped on my M1 and I'm having issues even with creating the PPPC profile for all files for ScanD. I am going to wipe the M1 clean and try again tomorrow but just wondering if you had any success.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-15-2021 02:17 PM
@sintichn I've been doing some more testing these past couple of days and unfortunately, have not succeeded... What I have done is un-installed clients current Sophos install using @fredrik.virding script above. Before installing a new version of Sophos I ensured that the computer had the proper System extensions (KEXT for Macs below Big Sur) and PPPC settings from Sophos's documentation. I had also created a separate PPPC for the ScanD setting using the PPPC Utility from Github. Next I installed the newest version of Sophos which I guess is 10.0.4... After a restart, I still get ScanD stopped error on both M1 and Intel macOS Big Sur Macs. So pretty much ScanD is the issue we are facing.
I have not tested out a wipe and reinstall (re-image - antiquated term) with an install of Sophos on a clean OS. Even if that method works, its not feasible to wipe and re-install OS for our users on the spot. Although we don't have very many users on Big Sur currently with a restriction. But still, we shouldn't have to wipe-erase/reinstall OS on users computer just to make Sophos function... That does not seem like a viable solution.
Other than that, I have no other updates on my end. I'm going to maybe try creating new Config profile, possibly on a clean image, and see what happens just like @sintichn . If that works then great, but what should we do with current M1/Big Sur users having issues with Sophos...?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2021 01:20 AM
I did some testing on machines who already were on Big Sur, i noticed that once you deploy all the PPPC's, system and network extension, the Users saw a new thing in System Preferences > Security & Privacy > General.
At the bottom, if they click "Advanced", there were 2 blank boxes, and if they checked those and restarted, it seemed to work. Try that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2021 07:41 AM
I think I found my issue. We had depnotify installing an old sophos package upon setting up the M1. I wiped it and excluded it from the old sophos policy and just had it install the new one. It works with no issues as of yet!
Thanks,
Nick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-16-2021 03:25 PM
Hi @fredrik.virding Totally understand with having users check marking the 2 boxes from within system preferences, security/privacy. The issue is our users don't have admin rights to unlock the settings in order to check mark the boxes... I want to be able to check mark those boxes through JAMF/MDM solution.
@sintichn I still haven't tried a wipe/erase, but will try that shortly and download the newest Sophos package from the Sophos Central dashboard. But do you still need to check mark the ScanD and the other feature from system preferences, security/privacy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-18-2021 06:14 AM
I know what you mean. Had the same issues on my end. I think the best move forward is to pre-load all System Extensions and such before allowing Users to upgrade.
I did so with a "Prepare my mac" policy, which basically added the System Extensions, Network Extensions and such, ran a recon, then allowed the Users to get the Big Sur downloader. So far, that has worked fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-22-2021 10:04 AM
@SirSir Is this still the case?
According to Sophos, if you're upgrading from Catalina to Big Sur, Sophos will not operate properly. You have to uninstall Sophos, upgrade to Big Sur, and then re-install Sophos. And make sure that all of your PPPC/Extension/Kext profiles are on the machine BEFORE upgrading to Big Sur. I don't think this is intended behavior, but still very annoying.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-23-2021 02:14 PM
Why do the Sophos instructions say "Please ensure that 'Allow users to approve kernel extensions' is unchecked."? If we check the box is it going to break things?
I know that the KEXTs are not required for M1 Macs but how about Intel Macs running Big Sur? Or are you only scoping the KEXTs to Catalina and older macOS versions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2021 10:59 AM
@MrRoboto you sure you dont need the kext profiles for sophos on M1 machines? All the setup guides i saw still required them. They havent released the univeral app version of the client yet, So its just the intel version running under rossetta. The kext profiles install on big sur 11.2 and higher.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-26-2021 11:05 PM
@SCCM I'm still testing so not certain at this point. So far Sophos installs okay and is not prompting or showing any errors. In my testing with other KEXTs on M1 Macs the profile would not install and give an error in Jamf. To successfully install I had to lower the security settings on the M1 Mac. Even so the KEXT profile would not install immediately after computer enrollment, but after a couple reboots it would. Related to PI-009052.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Posted on 04-27-2021 08:11 AM
So, no basically it no longer gives those boxes as options since it's all included in the config profile that I made for it.